The notorious North Korean hacking group 'Lazarus' was seen installing a Windows rootkit that abuses a Dell hardware driver in a Bring Your Own Vulnerable Driver attack.
The spear-phishing campaign unfolded in the autumn of 2021, and the confirmed targets include an aerospace expert in the Netherlands and a political journalist in Belgium.
According to ESET, which published a report on the campaign today, the primary goal was espionage and data theft.
Abusing Dell driver for BYOVD attacks
The EU-based targets of this campaign were emailed fake job offers, this time for Amazon, a typical and common social engineering trick employed by the hackers in 2022.
Opening these documents downloads a remote template from a hardcoded address, followed by infections involving malware loaders, droppers, custom backdoors, and more.
ESET reports that among the tools deployed in this campaign, the most interesting is a new FudModule rootkit that abuses a BYOVD (Bring Your Own Vulnerable Driver) technique to exploit a vulnerability in a Dell hardware driver for the first time.
"The most notable tool delivered by the attackers was a user-mode module that gained the ability to read and write kernel memory due to the CVE-2021-21551 vulnerability in a legitimate Dell driver," explains ESET in a new report on the attack.
"This is the first ever recorded abuse of this vulnerability in the wild."
"The attackers then used their kernel memory write access to disable seven mechanisms the Windows operating system offers to monitor its actions, like registry, file system, process creation, event tracing etc., basically blinding security solutions in a very generic and robust way."
A Bring Your Own Vulnerable Driver (BYOVD) attack is when threat actors load legitimate, signed drivers in Windows that also contain known vulnerabilities. As the kernel drivers are signed, Windows will allow the driver to be installed in the operating system.
However, the threat actors can now exploit the driver's vulnerabilities to launch commands with kernel-level privileges.
In this attack, Lazarus was exploiting the CVE-2021-21551 vulnerability in a Dell hardware driver ("dbutil_2_3.sys"), which corresponds to a set of five flaws that remained exploitable for 12 years before the computer vendor finally pushed security updates for it.
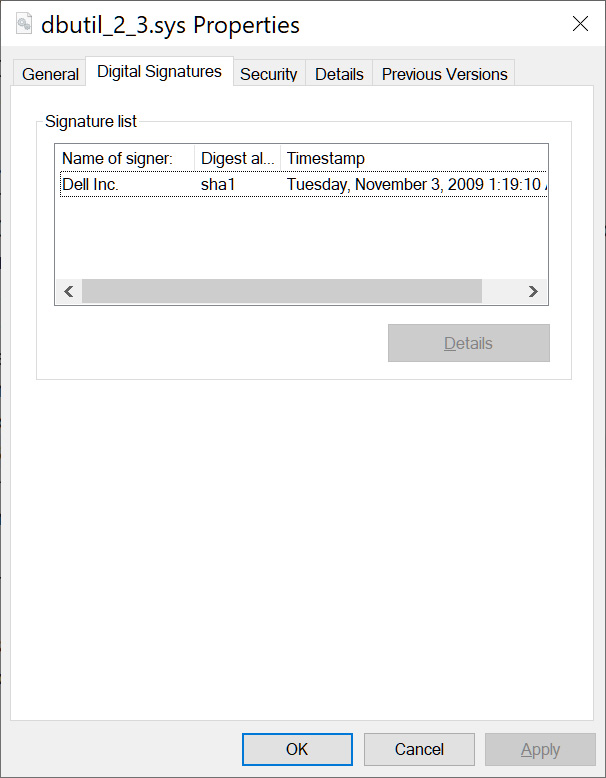
In December 2021, researchers at Rapid 7 warned about this particular driver being an excellent candidate for BYOVD attacks due to Dell’s inadequate fixes, allowing kernel code execution even on recent, signed versions.
It appears that Lazarus was already well aware of this potential for abuse and exploited the Dell driver well before security analysts issued their public warnings.
"The attackers then used their kernel memory write access to disable seven mechanisms the Windows operating system offers to monitor its actions, like registry, file system, process creation, event tracing etc., basically blinding security solutions in a very generic and robust way," continued ESET's report.
For those interested in the BYOVD aspect of the Lazarus attack, you can dive into the details on this 15-page technical paper that ESET published separately.
BLINDINGCAN and other tools
ESET added that the group deployed its trademark custom HTTP(S) backdoor ‘BLINDINGCAN,’ first discovered by U.S. intelligence in August 2020 and attributed to Lazarus by Kaspersky in October 2021.
The 'BLINDINGCAN' remote access trojan (RAT) sampled by ESET appears to run with significant backing from an undocumented server-side dashboard that performs parameter validation.
The backdoor supports an extensive set of 25 commands, covering file actions, command execution, C2 communication configuration, screenshot taking, process creation and termination, and system info exfiltration.
Other tools deployed in the presented campaign are the previously described FudModule Rootkit, an HTTP(S) uploader used for secure data exfiltration, and various trojanized open-source apps like wolfSSL and FingerText.
Trojanizing open-source tools are something Lazarus continues to do, as a Microsoft report from yesterday mentions this technique was used with PuTTY, KiTTY, TightVNC, Sumatra PDF Reader, and the muPDF/Subliminal Recording software installer.
- Karlston
-

 1
1



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.