The notorious North Korea-aligned state-sponsored actor known as the Lazarus Group has been attributed to a new campaign aimed at Linux users.
The attacks are part of a persistent and long-running activity tracked under the name Operation Dream Job, ESET said in a new report published today.
The findings are crucial, not least because it marks the first publicly documented example of the adversary using Linux malware as part of this social engineering scheme.
Operation Dream Job, also known as DeathNote or NukeSped, refers to multiple attack waves wherein the group leverages fraudulent job offers as a lure to trick unsuspecting targets into downloading malware. It also exhibits overlaps with two other Lazarus clusters known as Operation In(ter)ception and Operation North Star.
The attack chain discovered by ESET is no different in that it delivers a fake HSBC job offer as a decoy within a ZIP archive file that's then used to launch a Linux backdoor named SimplexTea distributed via an OpenDrive cloud storage account.
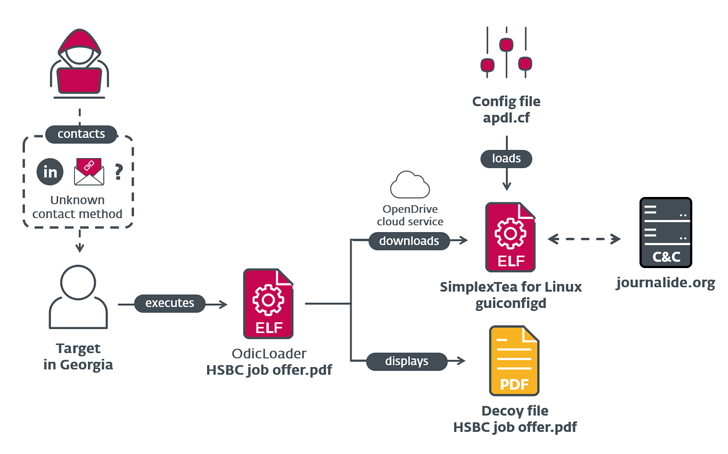
While the exact method used to distribute the ZIP file is not known, it's suspected to be either spear-phishing or direct messages on LinkedIn. The backdoor, written in C++, bears similarities to BADCALL, a Windows trojan previously attributed to the group.
Furthermore, ESET said it identified commonalities between artifacts used in the Dream Job campaign and those unearthed as part of the supply chain attack on VoIP software developer 3CX that came to light last month.
This also includes the command-and-control (C2) domain "journalide[.]org," which was listed as one of the four C2 servers used by malware families detected within the 3CX environment.
Indications are that preparations for the supply chain attack had been underway since December 2022, when some of the components were committed to the GitHub code-hosting platform.
The findings not only strengthen the existing link between Lazarus Group and the 3CX compromise, but also demonstrates the threat actor's continued success with staging supply chain attacks since 2020.
- Karlston and alf9872000
-

 2
2


Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.