A serious vulnerability named KeyTrap in the Domain Name System Security Extensions (DNSSEC) feature could be exploited to deny internet access to applications for an extended period.
Tracked as CVE-2023-50387, KeyTrap is a design issue in DNSSEC and impacts all popular Domain Name System (DNS) implementations or services.
It allows a remote attacker to cause a long lasting denial-of-service (DoS) condition in vulnerable resolvers by sending a single DNS packet.
DNS is what allows us humans to access online locations by typing in domain names instead of the server's IP address our computer needs to connect to.
DNSSEC is a feature of the DNS that brings cryptographic signatures to DNS records, thus providing authentication to responses; this verification ensures that DNS data comes from the source, its authoritative name server, and has not been modified on the way to route you to a malicious location.
Significant damage in one attack request
KeyTrap has been present in the DNSSEC standard well over two decades, and was discovered by researchers from the National Research Center for Applied Cybersecurity ATHENE, alongside experts from Goethe University Frankfurt, Fraunhofer SIT, and the Technical University of Darmstadt.
The researchers explain that the problem stems from DNSSEC's requirement to send all relevant cryptographic keys for supported ciphers and the corresponding signatures for the validation to happen.
The process is the same even if some DNSSEC keys are misconfigured, incorrect, or belong to ciphers that are not supported.
By taking advantage of this vulnerability, the researchers developed a new class of DNSSEC-based algorithmic complexity attacks that can increase by 2 million times the CPU instruction count in a DNS resolver, thus delaying its response.
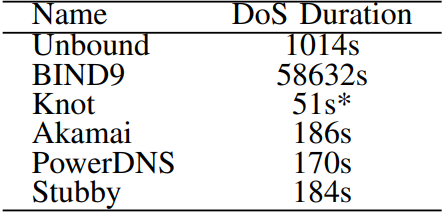
The duration of this DoS state depends on the resolver implementation but the researchers say a single attack request can hold the response from 56 seconds to as much as 16 hours.
"Exploitation of this attack would have severe consequences for any application using the Internet, including unavailability of technologies such as web-browsing, e-mail, and instant messaging," reads ATHENE's disclosure.
"With KeyTrap, an attacker could completely disable large parts of the worldwide Internet," the researchers say.
Complete details about the vulnerability and how it can manifest on modern DNS implementations can be found in a technical report published earlier this week.
The researchers have demonstrated how their KeyTrap attack can impact DNS service providers, such as Google and Cloudflare, since early November 2023 and worked with them to develop mitigations.
ATHENE says KeyTrap has been present in widely used standards since 1999, so it went unnoticed for nearly 25 years, primarily because of the complexity of the DNSSEC validation requirements.
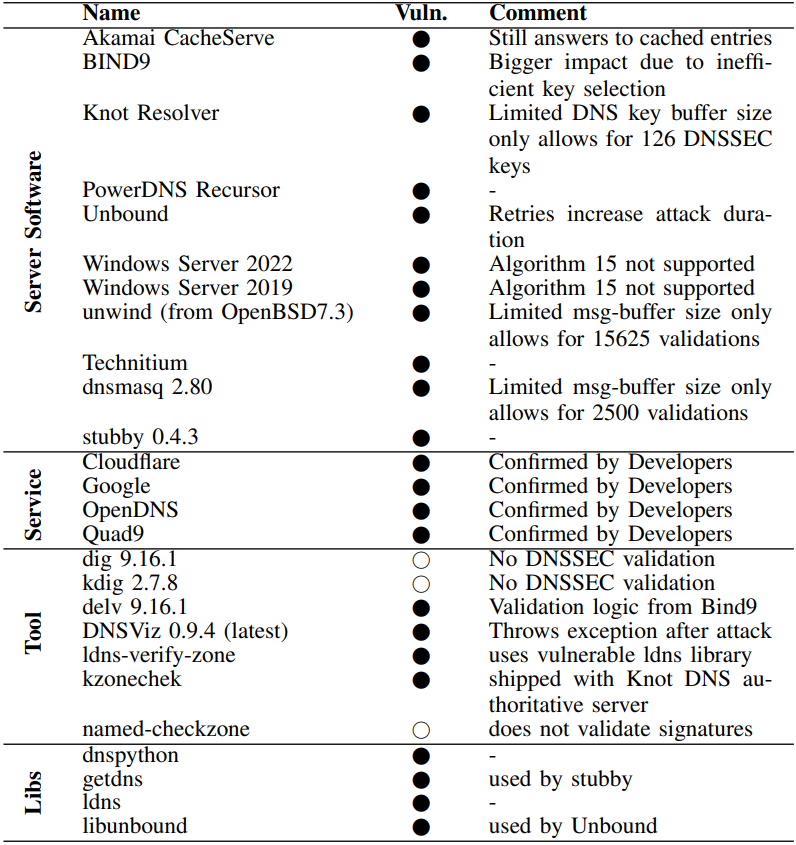
Though impacted vendors have already pushed fixes or are in the process of mitigating the KeyTrap risk, ATHENE states that addressing the issue at a fundamental level may require a reevaluation of the DNSSEC design philosophy.
In response to the KeyTrap threat, Akamai developed and deployed, between December 2023 and February 2024, mitigations for its DNSi recursive resolvers, including CacheServe and AnswerX, as well as its cloud and managed solutions.
This security gap could have allowed attackers to cause major disruption to the functioning of the internet, exposing one-third of DNS servers worldwide to a highly efficient denial-of-service (DoS) attack and potentially impacting more than one billion users. - Akamai
Akamai notes that based on APNIC data, approximately 35% of U.S.-based and 30% of internet users worldwide rely on DNS resolvers that use DNSSEC validation and, hence, are vulnerable to KeyTrap.
Although the internet company didn't share many details about the actual mitigations it implemented, ATHENE's paper describes Akamai's solution as limiting the cryptographic failures to a maximum of 32, making it practically impossible to exhaust CPU resources and cause stalling.
Fixes are already present in DNS services from Google and Cloudflare.



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.