The Keralty multinational healthcare organization suffered a RansomHouse ransomware attack on Sunday, disrupting the websites and operations of the company and its subsidiaries.
Keralty is a Colombian healthcare provider that operates an international network of 12 hospitals and 371 medical centers in Latin America, Spain, the US, and Asia. The group employs 24,000 people and 10,000 medical doctors who provide healthcare to over 6 million patients.
The company offers further healthcare services through its subsidiaries, Colsanitas, Sanitas USA, and EPS Sanitas.
Cyberattack disrupts Keralty's operations
Over the past few days, Keralty and its subsidiaries, EPS Sanitas and Colsanitas, have suffered disruption to their IT operations, the scheduling of medical appointments, and its websites.
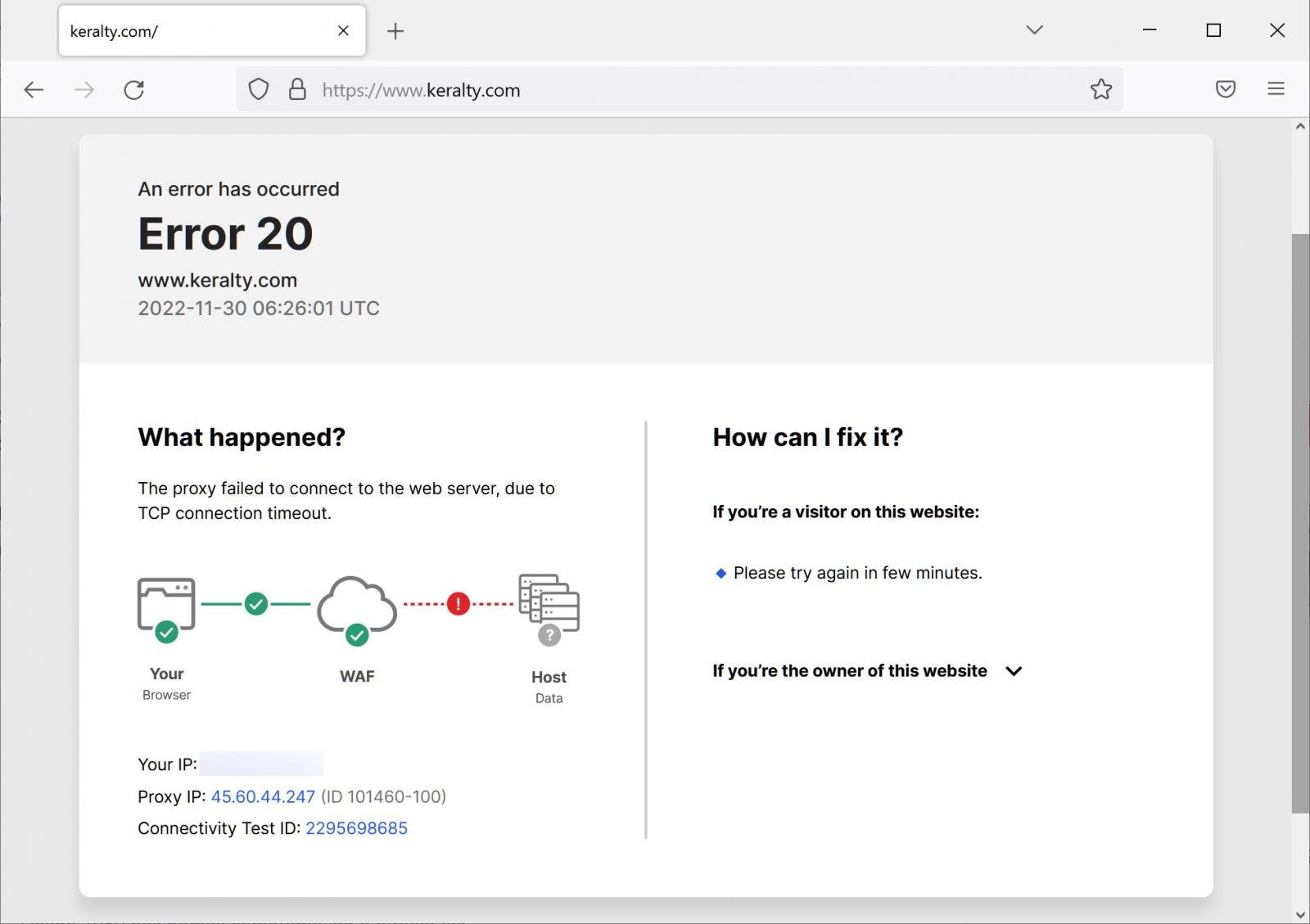
Errors shown when visiting Keralty.com
Source: BleepingComputer
The IT outages have impacted Colombia's healthcare system, with local media reporting that patients have been waiting in line for over twelve hours to receive care and some patients fainting due to a lack of medical attention.
On Monday, Keralty stated they were suffering technical issues but did not disclose the cause.
However, Keralty issued another statement yesterday confirming that the disruption was caused by a cyberattack on their network, causing technical failures in their IT systems.
"The computer servers of the Keralty Group companies have been the object of a cyberattack, which has generated technical failures in our systems," reads a translated statement from Keralty.
"From the moment it was identified, we have been working 24 hours a day, both from the technological team and from the medical and administrative team, to provide continuity of care to our members."
"Likewise, from the beginning, this situation was brought to the attention of the competent authorities and the respective criminal investigation has been initiated. In order to maintain attention to our users, from Keralty We continue to implement the necessary contingency plans to maintain the service."
BleepingComputer has attempted to contact the Keralty Group with questions about the attack but has not received a response at this time.
RansomHouse behind the attack
As first reported by Camilo Andrés García today, a Twitter user named Alexánder tweeted a screenshot of a VMware ESXi server with a ransom note displaying 'Dear Keralty,' indicating that the healthcare company suffered a ransomware attack.
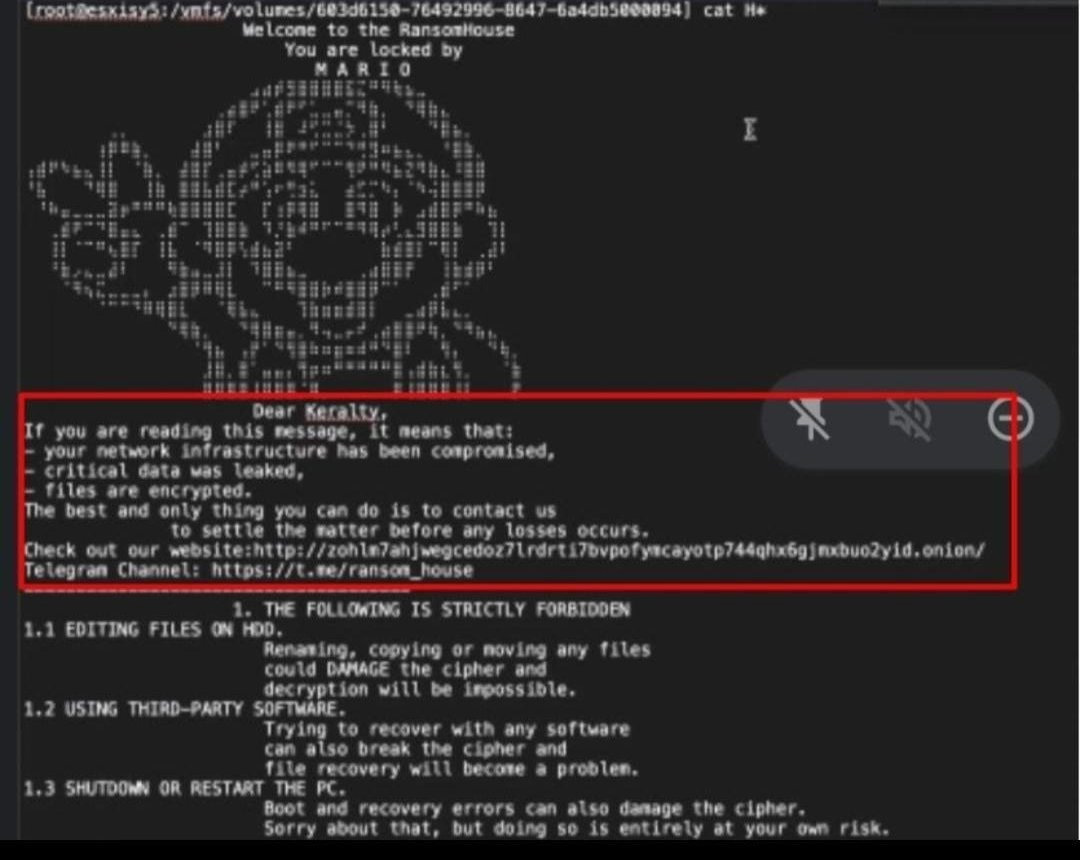
RansomHouse ransom note for Keralty
Source: BleepingComputer
BleepingComputer has identified this ransom note as belonging to the RansomHouse ransomware operation, which originally called its ransomware 'White Rabbit.'
During their attacks on eight municipalities in Italy, the threat actors changed the name to 'Mario' in homage to the Italian hero of the Super Marios Bros game.
This new encryptor will encrypt Windows and Linux devices and append the '.mario' extension to encrypted files while dropping ransom notes named 'How To Restore Your Files.txt.'
After seeing this tweet, BleepingComputer has since independently confirmed from a source that RansomHouse was behind the attack on Keralty.
The RansomHouse threat actors further told BleepingComputer that they were behind an attack on November 27th and claimed to have stolen 3 TB of data.
BleepingComputer has not been able to confirm the claims that data, if any, was stolen.
RansomHouse has previously stated they conducted data-theft attacks on AMD and ADATA.
However, ADATA denied they were attacked by RansomHouse and said the leaked data was from a previous RagnarLocker ransomware attack in 2021.




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.