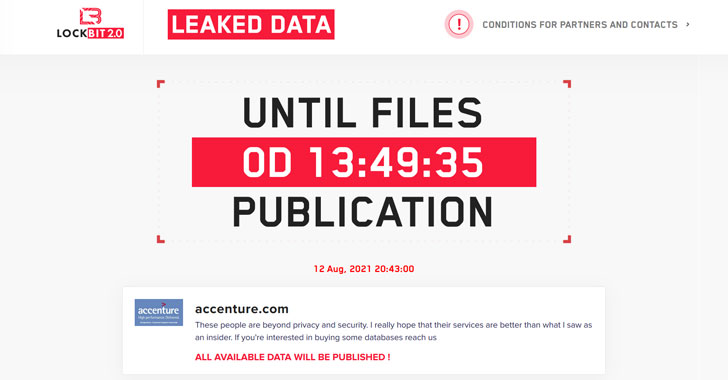
Global IT consultancy giant Accenture has become the latest company to be hit by the LockBit ransomware gang, according to a post made by the operators on their dark web portal, likely filling a void left in the wake of DarkSide and REvil shutdown.
"These people are beyond privacy and security. I really hope that their services are better than what I saw as an insider," read a message posted on the data leak website. Accenture said it has since restored the affected systems from backups.
LockBit, like its now-defunct DarkSide and REvil counterparts, operates using a ransomware-as-a-service (RaaS) model, roping in other cybercriminals (aka affiliates) to carry out the intrusion using its platform, with the payments often divided between the criminal entity directing the attack and the core developers of the malware.
The ransomware group emerged on the threat landscape in September 2019, and in June 2021 launched LockBit 2.0 along with an advertising campaign to recruit new partners. "LockBit also claims to offer the fastest data exfiltration on the market through StealBit, a data theft tool that can allegedly download 100 GB of data from compromised systems in under 20 minutes," Emsisoft noted in a profile of the crime syndicate.
Some of LockBit's past victims include the Press Trust of India and Merseyrail.
The development comes as ransomware incidents have become a critical threat to national and economic security that have left businesses scrambling to pay hefty extortion demands.
The spike in attacks against corporate and critical infrastructure have also been increasingly accompanied by a tactic called "triple extortion," wherein sensitive data on a target's systems is extracted prior to locking up through encryption, followed by applying pressure on victim companies into paying up by threatening to publish the stolen data online, failing which, the attackers then adopt a third phase, using that data to blackmail its customers or launch DDoS attacks.
"Through our security controls and protocols, we identified irregular activity in one of our environments. We immediately contained the matter and isolated the affected servers. We fully restored our affected systems from back up. There was no impact on Accenture's operations, or on our clients' systems," Accenture said in a statement shared with The Hacker News.
- Karlston
-

 1
1


Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.