Website of Israel's largest oil refinery operator, BAZAN Group is inaccessible from most parts of the world as threat actors claim to have hacked the Group's cyber systems.
The Haifa Bay-based BAZAN Group, formerly Oil Refineries Ltd., generates over $13.5 billion in annual revenue and employs more than 1,800 people.
The company boasts to have a total oil refining capacity of about 9.8 million tons of crude oil per year.
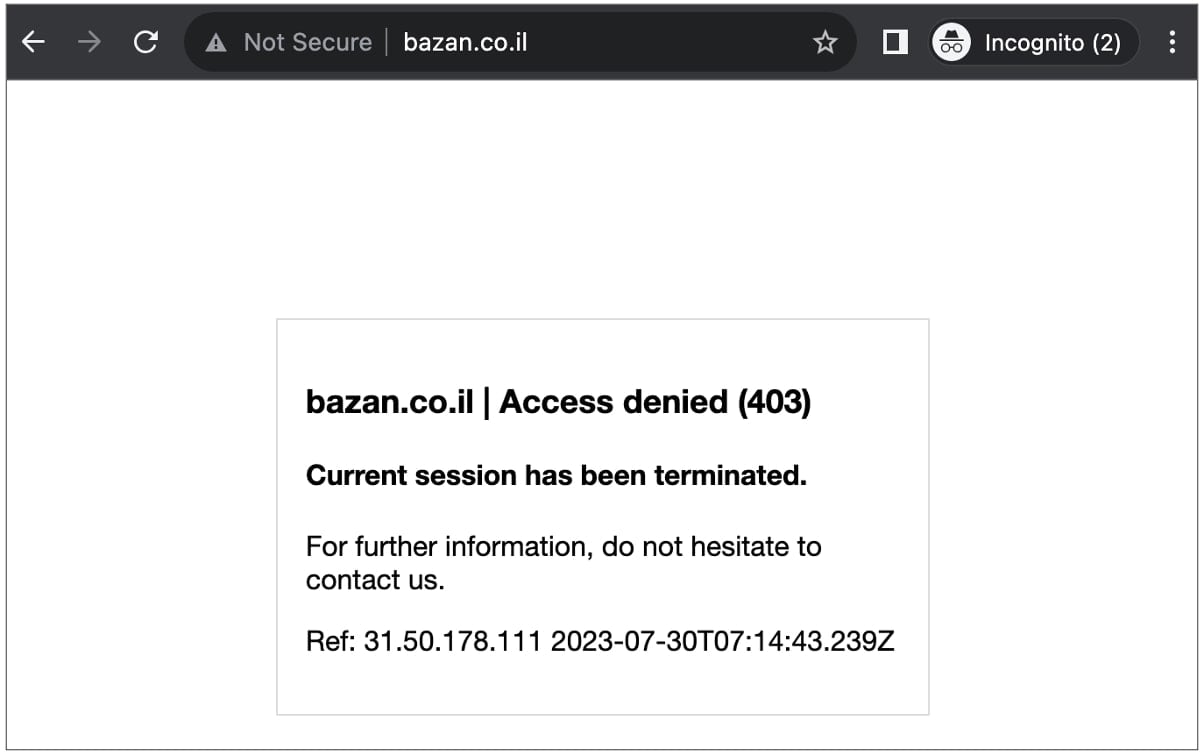
BAZAN website cut off from the internet
Over the weekend, incoming traffic to BAZAN Group's websites, bazan.co.il and eng.bazan.co.il is either timing out, with HTTP 502 errors, or being refused by the company's servers.
BleepingComputer confirmed that the oil refinery's website has been made inaccessible for most visitors from around the world.
In our tests, the website was, however accessible from within Israel, possibly after imposition of a geo-block by BAZAN in an attempt to thwart an ongoing cyber attack.
Cyber Avengers claims responsibility
In a Telegram channel, Iranian hacktivist group, 'Cyber Avengers' aka 'CyberAv3ngers' claimed that it had breached BAZAN's network over the weekend.
On Saturday evening, the group additionally leaked what appeared to be screenshots of BAZAN's SCADA systems, which are software applications used to monitor and operate industrial control systems.
These included diagrams of "Flare Gas Recovery Unit," "Amine Regeneration" system, a petrochemical "Splitter Section," and PLC code, as seen by BleepingComputer.
In a statement to BleepingComputer, published below, a spokesperson for BAZAN has dismissed the leaked materials as "entirely fabricated."
"We are aware of recent false publications regarding a hostile group's attempt to carry out a cyber-attack on Bazan. Please note that the information and images being circulated are entirely fabricated and have no association with Bazan or its assets. While our image website briefly experienced disruption during a DDoS attack, no damage was observed to the company's servers or assets. This appears to be an act of propaganda aimed at spreading misinformation and causing a consciousness effect."
"Our cybersecurity measures are vigilant, we are working closely with the Israeli National Cyber Directorate and our partners to monitor any suspicious activity to ensure the safety and integrity of our operations."
The hacktivist group further implied that it had breached the petrochemicals giant via an exploit targeting a Check Point firewall at the company.
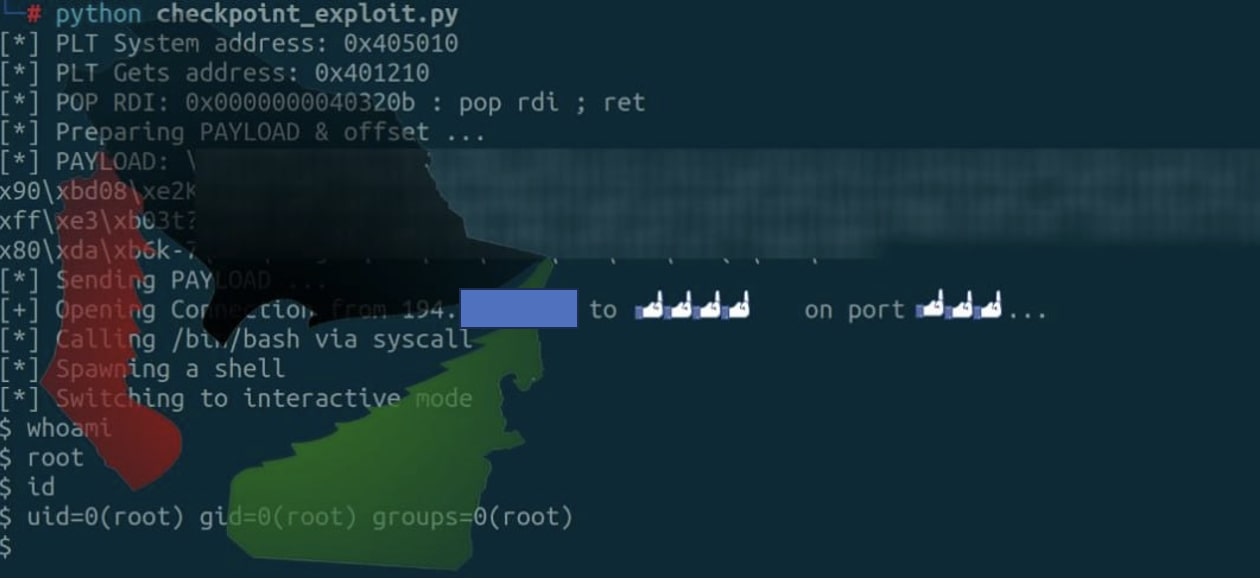
The IP address (194.xxx.xxx.xxx) purportedly belonging to the firewall device is indeed assigned to Oil Refineries Ltd., BleepingComputer could confirm via public records. At the time of writing, the IP address is returning a "Forbidden," error message when accessed in our test.
A Check Point spokesperson stressed that "none of these claims are true" and reiterated the refinery's findings in an email to BleepingComputer.
"There isn’t any past vulnerability which enabled such an attack," the Check Point representative further clarified.
Lastly, CyberAvengers boasts that they are responsible for the 2021 fires at the Haifa Bay petrochemical plants caused by a pipeline malfunction. In 2020, the same group of threat actors also claimed attacks on 28 Israeli railway stations by targeting more than 150 industrial servers.
BleepingComputer has not been able to independently verify the veracity of these prior claims made by the threat actor.
Update, July 30th 12:52 PM ET: Edited the article to include statements from Bazan Group and Check Point received after publishing.
- aum
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.