IT and communication companies in Israel were at the center of a supply chain attack campaign spearheaded by an Iranian threat actor that involved impersonating the firms and their HR personnel to target victims with fake job offers in an attempt to penetrate their computers and gain access to the company's clients.
The attacks, which occurred in two waves in May and July 2021, have been linked to a hacker group called Siamesekitten (aka Lyceum or Hexane) that has primarily singled out oil, gas, and telecom providers in the Middle East and in Africa at least since 2018, researchers from ClearSky said in a report published Tuesday.
Infections undertaken by the adversary commenced with identifying potential victims, who were then enticed with "alluring" job offers in well-known companies like ChipPc and Software AG by posing as human resources department employees from the impersonated firms, only to lead the victims to a phishing website containing weaponized files that unload a backdoor known as Milan to establish connections with a remote server and download a second-stage remote access trojan named DanBot.
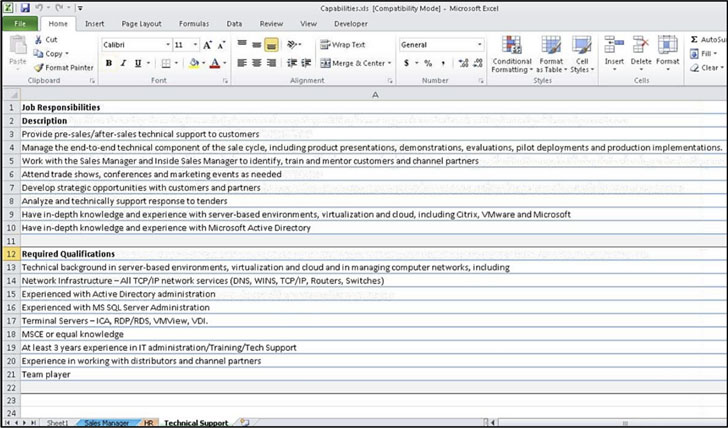
ClearSky theorized that the attacks' focus on IT and communication companies suggest they are intended to facilitate supply chain attacks on their clients.
Besides employing lure documents as an initial attack vector, the group's infrastructure included setting up fraudulent websites to mimic the company being impersonated as well as creating fake profiles on LinkedIn. The lure files, for their part, take the form of a macro-embedded Excel spreadsheet that details the supposed job offers and a portable executable (PE) file that includes a 'catalog' of products used by the impersonated organization.
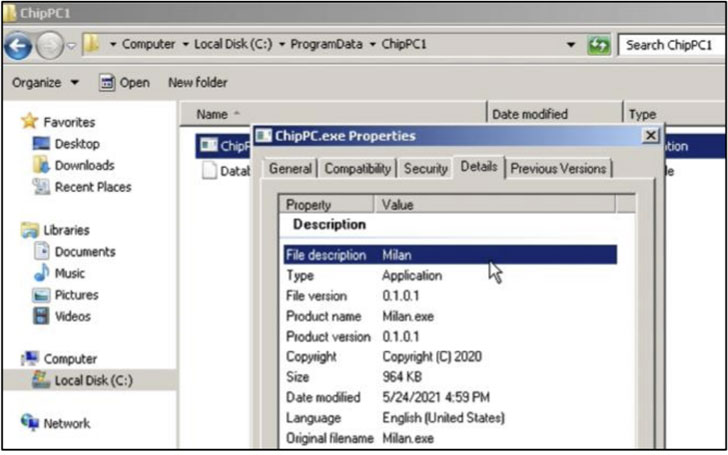
Regardless of the file downloaded by the victim, the attack chain culminates in the installation of the C++-based Milan backdoor. The July 2021 attacks against Israeli companies are also notable for the fact that the threat actor replaced Milan with a new implant called Shark that's written in .NET.
"This campaign is similar to the North Korean 'job seekers' campaign, employing what has become a widely used attack vector in recent years - impersonation," the Israeli cybersecurity company said. "The group's main goal is to conduct espionage and utilize the infected network to gain access to their clients' networks. As with other groups, it is possible that espionage and intelligence gathering are the first steps toward executing impersonation attacks targeting ransomware or wiper malware."
- Karlston
-

 1
1



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.