Internet Archive's "The Wayback Machine" has suffered a data breach after a threat actor compromised the website and stole a user authentication database containing 31 million unique records.
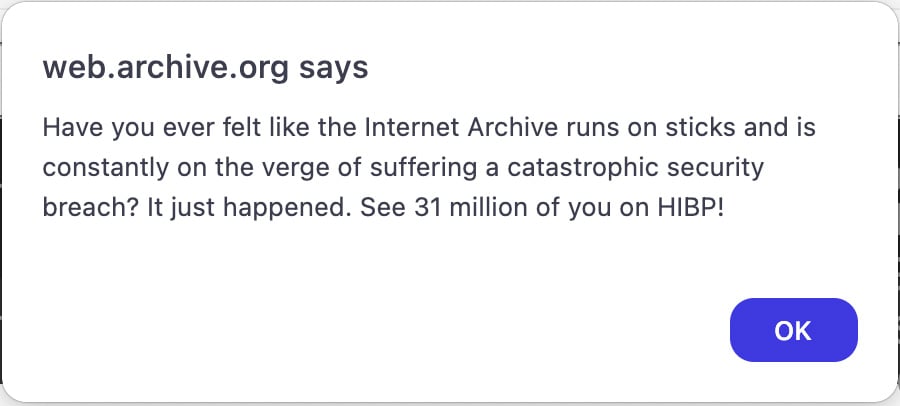
News of the breach began circulating Wednesday afternoon after visitors to archive.org began seeing a JavaScript alert created by the hacker, stating that the Internet Archive was breached.
"Have you ever felt like the Internet Archive runs on sticks and is constantly on the verge of suffering a catastrophic security breach? It just happened. See 31 million of you on HIBP!," reads a JavaScript alert shown on the compromised archive.org site.
Source: BleepingComputer
The text "HIBP" refers to is the Have I Been Pwned data breach notification service created by Troy Hunt, with whom threat actors commonly share stolen data to be added to the service.
Hunt told BleepingComputer that the threat actor shared the Internet Archive's authentication database nine days ago and it is a 6.4GB SQL file named "ia_users.sql." The database contains authentication information for registered members, including their email addresses, screen names, password change timestamps, Bcrypt-hashed passwords, and other internal data.
The most recent timestamp on the stolen records was ta is September 28th, 2024, likely when the database was stolen.
Hunt says there are 31 million unique email addresses in the database, with many subscribed to the HIBP data breach notification service. The data will soon be added to HIBP, allowing users to enter their email and confirm if their data was exposed in this breach.
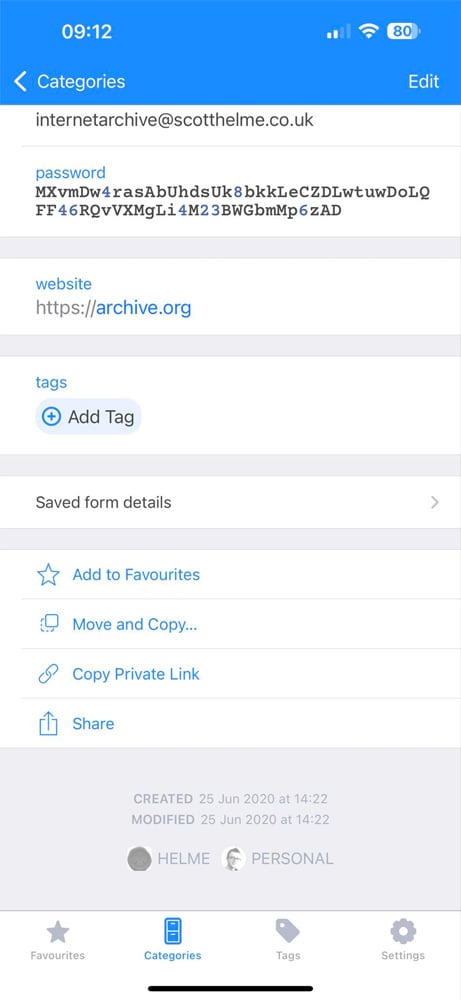
The data was confirmed to be real after Hunt contacted users listed in the databases, including cybersecurity researcher Scott Helme, who permitted BleepingComputer to share his exposed record.
9887370, [email protected],$2a$10$Bho2e2ptPnFRJyJKIn5BiehIDiEwhjfMZFVRM9fRCarKXkemA3PxuScottHelme,2020-06-25,2020-06-25,[email protected],2020-06-25 13:22:52.7608520,\N0\N\N@scotthelme\N\N\NHelme confirmed that the bcrypt-hashed password in the data record matched the brcrypt-hashed password stored in his password manager. He also confirmed that the timestamp in the database record matched the date when he last changed the password in his password manager.
Source: Scott Helme
Hunt says he contacted the Internet Archive three days ago and began a disclosure process, stating that the data would be loaded into the service in 72 hours, but he has not heard back since.
It is not known how the threat actors breached the Internet Archive and if any other data was stolen.
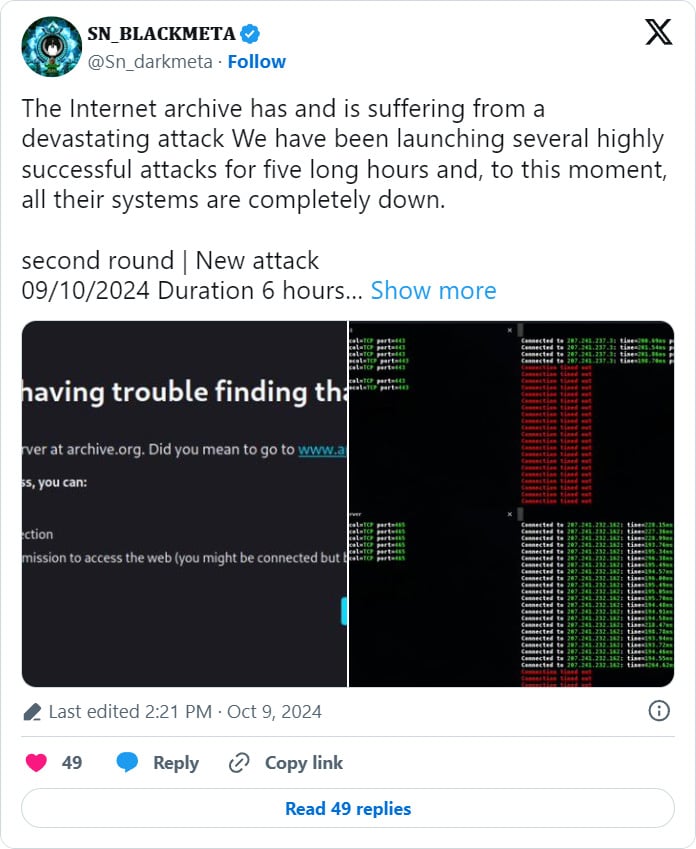
Earlier today, the Internet Archive suffered a DDoS attack, which has now been claimed by the BlackMeta hacktivist group, who says they will be conducting additional attacks.
BleepingComputer contacted the Internet Archive with questions about the attack, but no response was immediately available.
RIP Matrix | Farewell my friend ![]()
Hope you enjoyed this news post.
Thank you for appreciating my time and effort posting news every day for many years.
2023: Over 5,800 news posts | 2024 (till end of September): 4,292 news posts



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)


Recommended Comments
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.