The North Korean 'Kimsuky' threat actors are going to great lengths to ensure that their malicious payloads are only downloaded by valid targets and not on the systems of security researchers.
According to a Kaspersky report published today, the threat group has been employing new techniques to filter out invalid download requests since the start of 2022, when the group launched a new campaign against various targets in the Korean peninsula.
The new safeguards implemented by Kimsuky are so effective that Kaspersky reports an inability to acquire the final payloads even after they are successfully connected to the threat actor’s command and control server.
A multi-stage validation scheme
The attacks spotted by Kaspersky begin with a phishing email sent to politicians, diplomats, university professors, and journalists in North and South Korea.
Kaspersky was able to compile a list of potential targets thanks to retrieved C2 scripts containing partial email addresses of targets.
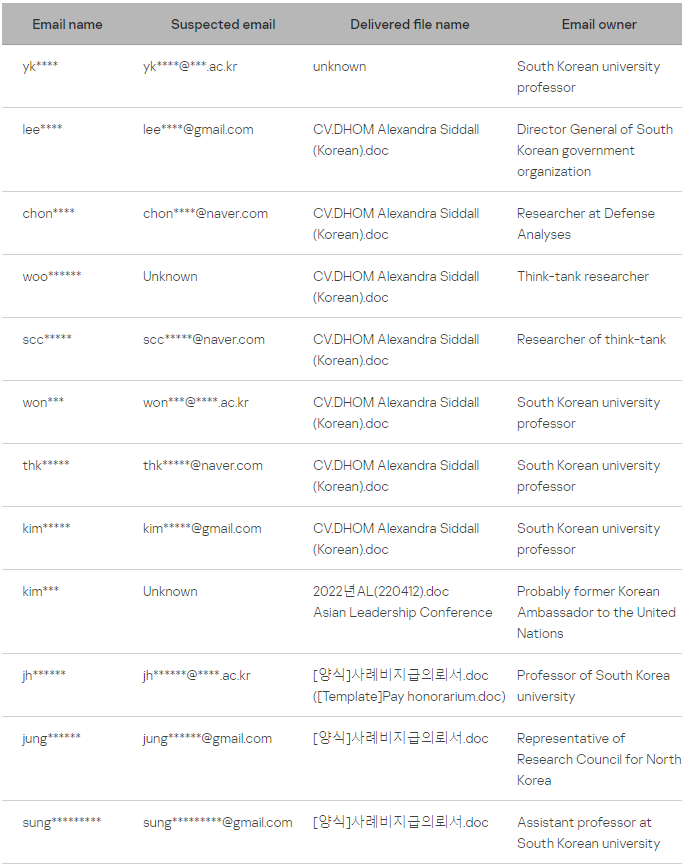
The emails contain a link that takes victims to a first-stage C2 server that checks and verifies a few parameters before delivering a malicious document. If the visitor doesn’t match the list of targets, they are served an innocuous document.
The parameters include the visitor’s email address, OS (Windows is valid), and the file “[who].txt” that’s dropped by the second-stage server.
At the same time, the visitor’s IP address is forwarded to the second-stage C2 server as a subsequent checking parameter.
The document dropped by the first-stage C2 contains a malicious macro that connects the victim to the second-stage C2, fetches the next-stage payload, and runs it with the mshta.exe process.

The payload is an .HTA file that also creates a scheduled task for auto-execution. Its function is to profile the victim by checking ProgramFiles folder paths, AV name, username, OS version, MS Office version, .NET framework version, and more.
The fingerprint result is stored in a string ("chnome"), a copy is sent to the C2, and a new payload is fetched and registered with a persistence mechanism.
The next payload is a VBS file that can take the victim to a legitimate blog or, if they’re valid targets, take them to the next payload-download phase.
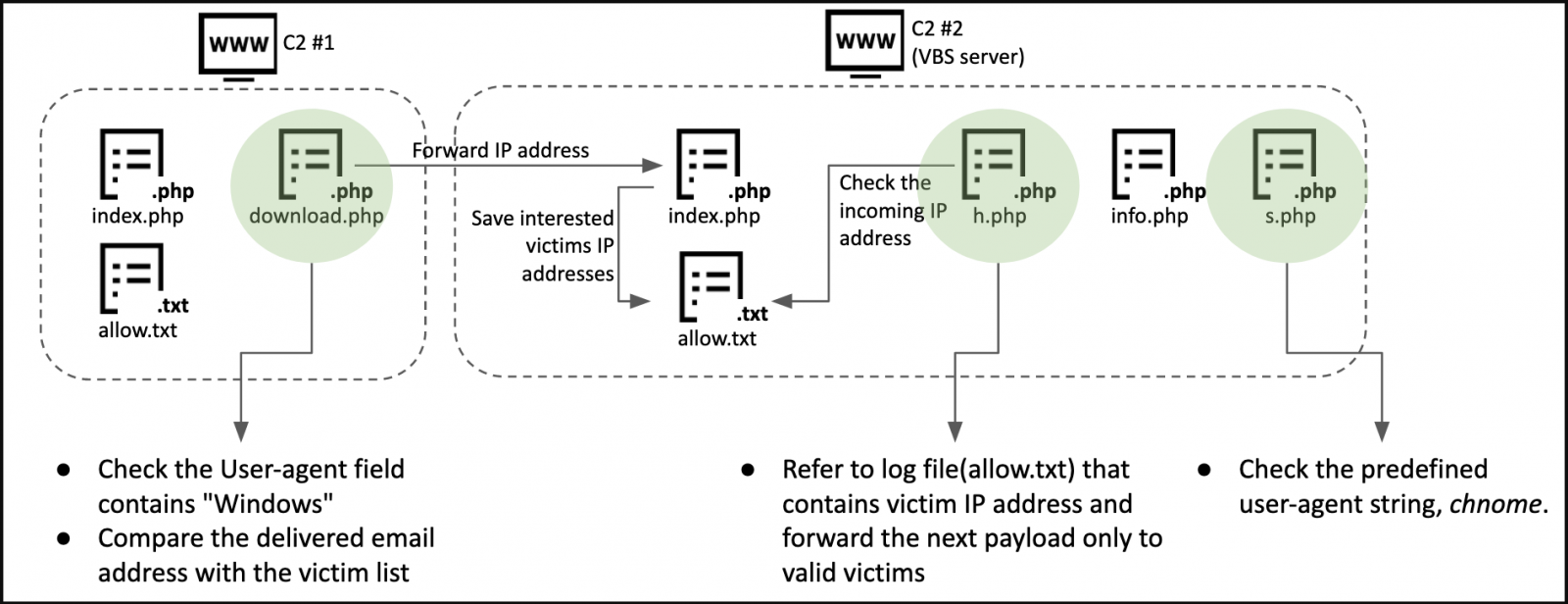
“Interestingly, this C2 script generates a blog address based on the victim’s IP address. After calculating the MD5 hash of the victim’s IP address, it cuts off the last 20 characters and turns it into a blog address,” details Kaspersky.
“The author’s intent here is to operate a dedicated fake blog for each victim, thereby decreasing the exposure of their malware and infrastructure.”
This is when the victim’s system is checked for the existence of the unusual “chnome” string, which was purposefully misspelled to serve as a unique validator that still doesn’t raise suspicions.
.png)
Unfortunately, Kaspersky couldn’t continue from here and fetch the next stage payload, so whether that would be the final one or if there were most validation steps remains unknown.
Kimsuky is a very sophisticated threat actor recently seen deploying custom malware and using Google Chrome extensions to steal emails from victims.
The campaign highlighted by Kaspersky illustrates the elaborate techniques employed by the Korean hackers to hinder analysis and make their tracking much harder.
Source: BleepingComputer






Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.