A three-year-long honeypot experiment featuring simulated low-interaction IoT devices of various types and locations gives a clear idea of why actors target specific devices.
More specifically, the honeypot was meant to create a sufficiently diverse ecosystem and cluster the generated data in a way that determines the goals of adversaries.
IoT (Internet of Things) devices are a booming market that includes small internet-connected devices such as cameras, lights, doorbells, smart TVs, motion sensors, speakers, thermostats, and many more.
It is estimated that by 2025, over 40 billion of these devices will be connected to the Internet, providing network entry points or computational resources that can be used in unauthorized crypto mining or as part of DDoS swarms.
Setting the stage
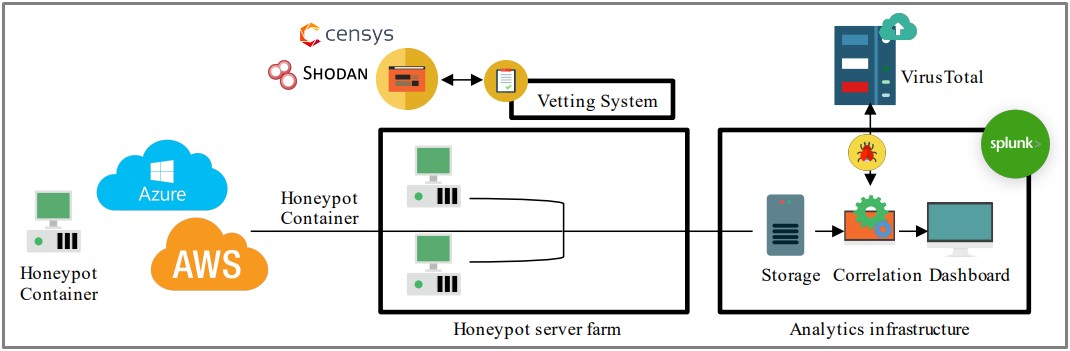
The three components of the honeypot ecosystem set up by researchers at the NIST and the University of Florida included server farms, a vetting system, and the data capturing and analysis infrastructure.
To create a diverse ecosystem, the researchers installed Cowrie, Dionaea, KFSensor, and HoneyCamera, which are off-the-shelf IoT honeypot emulators.
The researchers configured their instances to appear as real devices on Censys and Shodan, two specialized search engines that find internet-connected services.
The three main types of honeypots were the following:
- HoneyShell – Emulating Busybox
- HoneyWindowsBox – Emulating IoT devices running Windows
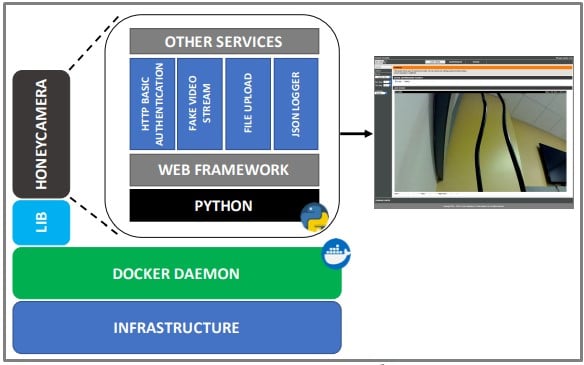
- HoneyCamera – Emulating various IP cameras from Hikvision, D-Link, and other devices.
Source: Arxiv.org
A novel element in this experiment is that the honeypots were adjusted to respond to attacker traffic and attack methods.
The researchers used the collected data to change the IoT configuration and defenses and then gather new data that reflected the actor's response to these changes.
The findings
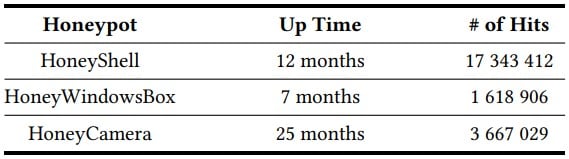
The experiment produced data from massive 22.6 million hits, with the vast majority targeting the HoneyShell honeypot.
Source: Arxiv.org
The various actors exhibited similar attack patterns, likely because their objectives and the means to achieve them were common.
For example, most actors run commands such as "masscan" to scan for open ports and "/etc/init.d/iptables stop" to disable firewalls.
Additionally, many actors run "free -m", "lspci grep VGA", and "cat /proc/cpuinfo", all three aiming to collect hardware information about the target device.
Interestingly, almost a million hits tested "admin / 1234" username-password combination, reflecting an overuse of the credentials in IoT devices.
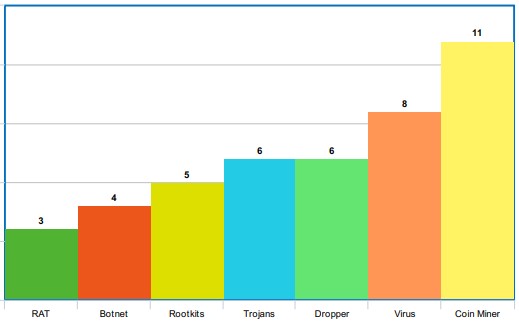
As for end goals, the researchers found that the HoneyShell and the HoneyCamera honeypots were targeted mainly for DDoS recruitment and were often also infected with a Mirai variant or a coin miner.
Coin miner infections were the most common observation on the Windows honeypot, followed by viruses, droppers, and trojans.
Source: Arxiv.org
In the case of the HoneyCamera, the researchers intentionally crafted a vulnerability to reveal credentials and noticed that 29 actors engaged in exploiting the flaw manually.
Source: Arxiv.org
"Only 314 112 (13 %) unique sessions were detected with at least one successful command execution inside the honeypots," explains the research paper.
"This result indicates that only a small portion of the attacks executed their next step, and the rest (87 %) solely tried to find the correct username/password combination."
Honeypot experiment reveals what hackers want from IoT devices
- aum, scarabou and Mutton
-

 3
3



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.