Security researchers have identified a new data-wiping malware they named SwiftSlicer that aims to overwrite crucial files used by the Windows operating system.
The new malware was discovered in a recent cyberattack against a target in Ukraine and has been attributed to Sandworm, a hacking group working for Russia’s General Staff Main Intelligence Directorate (GRU) as part of the Main Center for Special Technologies (GTsST) military unit 74455.
Go-based data wiper
While details are scant regarding SwiftSlicer at the moment, security researchers at cybersecurity company ESET say that they found the destructive malware deployed during a cyberattack in Ukraine.
The name of the target has not been published, recent Sandworm activity includes a data-wiping attack on Ukrinform, Ukraine’s national news agency.
However, in the attack that ESET discovered on January 25 the threat actor launched a different destructive malware called CaddyWiper, previously observed in other attacks on Ukrainian targets [1, 2].
ESET says that Sandworm launched SwiftSlicer using Active Directory Group Policy, which allows domain admins to execute scripts and commands throughout all of the devices in Windows network.
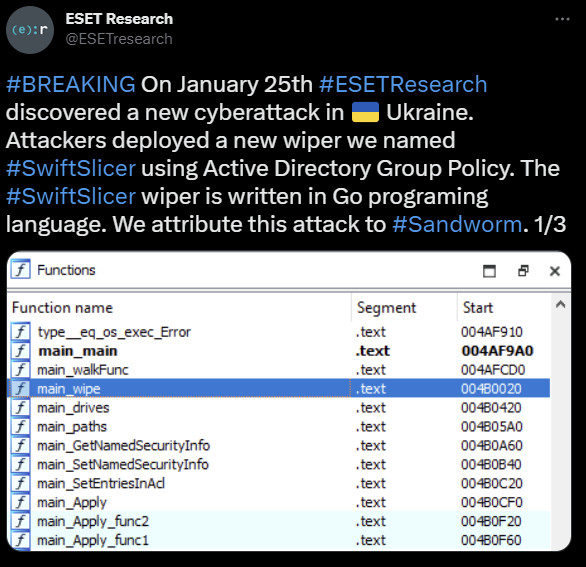
ESET researchers say that SwiftSlicer was deployed to delete shadow copies and to overwrite critical files in the Windows system directory, specifically drivers and the Active Directory database.
The specific targeting of the %CSIDL_SYSTEM_DRIVE%\Windows\NTDS folder indicates that the wiper is not only meant to destroy files but to also bring down the entire Windows domains.
SwiftSlicer data-wiping malware functions
source: ESET
SwiftSlicer overwrites data using 4096 bytes blocks that are filled with randomly generated bytes. After completing the data destruction job, the malware reboots the systems, ESET researchers say.
According to the researchers, Sandworm developed SwiftSlicer in Golang programming language, which has been adopted by multiple threat actors for its versatility, and it can be compiled for all platforms and hardware.
Although the malware has been added to the Virus Total database only recently (submitted on January 26), it is currently detected by more than half of the antivirus engines present on the scanning platform.
Russia's destructive malware
In a report today, the Ukrainian Computer Emergency Response Team (CERT-UA) says that Sandworm also tried to use five data-destruction utilities on the Ukrinform news agency’s network:
- CaddyWiper (Windows)
- ZeroWipe (Windows)
- SDelete (legitimate tool for Windows)
- AwfulShred (Linux)
- BidSwipe (FreeBSD)
The agency’s investigation revealed that SandWorm distributed the malware to computers on the network using a Group Policy Object (GPO) - a set of rules administrators use to configure operating systems, apps, and user settings in an Active Directory environment, the same method also used to execute SwiftSlicer.
- Karlston and Sonar
-

 2
2




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.