A previously undocumented, fully undetectable PowerShell backdoor is being actively used by a threat actor who has targeted at least 69 entities.
Based on its features, the malware is designed for cyberespionage, mainly engaging in data exfiltration from the compromised system.
When first detected, the PowerShell backdoor was not seen as malicious by any vendors on the VirusTotal scanning service.
However, its cover was blown due to operational mistakes by the hackers, allowing SafeBreach analysts to access and decrypt commands sent by the attackers to execute on infected devices.
From job application to PowerShell backdoor
The attack begins with the arrival of a phishing email with an attached malicious document named "Apply Form.docm." Based on the file contents and metadata, it is likely themed after a LinkedIn-based job application.
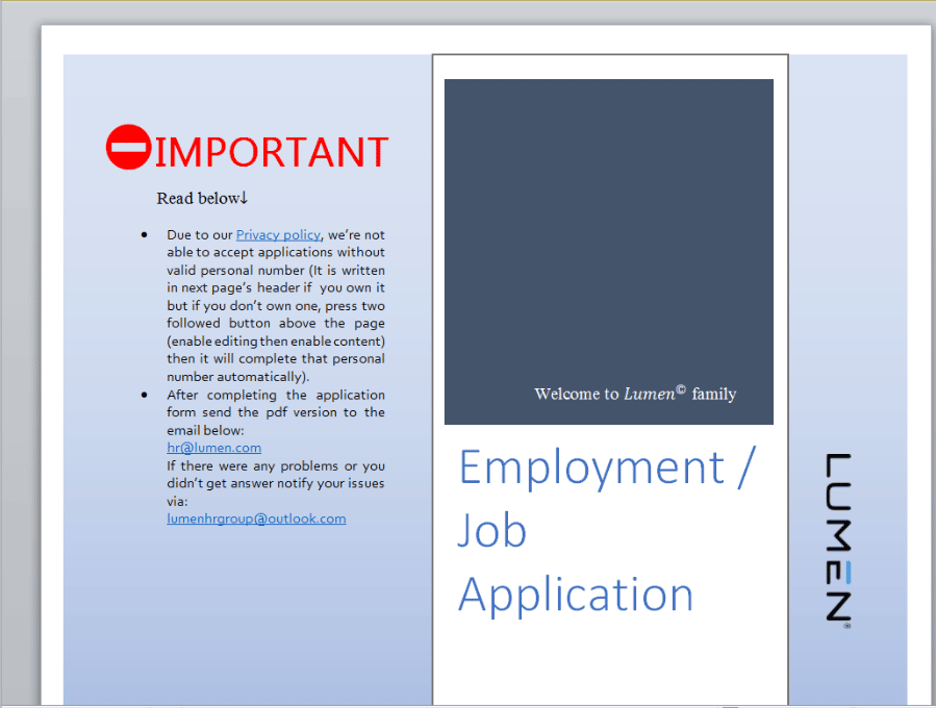
The document lure containing the macro (SafeBreach)
The document contains malicious macros that drop and execute an 'updater.vbs' script that creates a scheduled task to impersonate a routine Windows update.
The VBS script then executes two PowerShell scripts, "Script.ps1" and "Temp.ps1," both of which are stored inside the malicious document in obfuscated form.
When SafeBreach first discovered the scripts, none of the antivirus vendors on VirusTotal detected the PowerShell scripts as malicious.
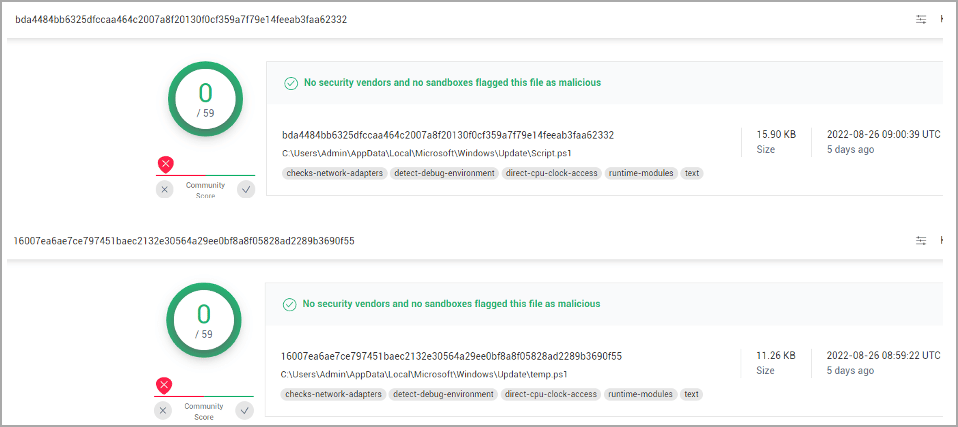
VirusTotal returning clean scans on both scripts (SafeBreach)
"Script.ps1" connects to the attacker's command and control servers (C2), sends a victim ID to the operators, and then awaits a command received in AES-256 CBC encrypted form.
Based on the ID count, SafeBreach analysts concluded that the threat actor's C2 had logged 69 IDs before them, which is likely the approximate number of breached computers.
The "Temp.ps1" script decodes the command in the response, executes it, and then encrypts and uploads the result via a POST request to the C2.
SafeBreach took advantage of the predictable victim IDing and created a script that could decrypt the commands sent to each of them.
The analysts found that two-thirds of the commands were to exfiltrate data, with the others used for user enumerations, file listings, removal of files and accounts, and RDP client enumerations.
.png)
Unknown stealthy threats
This PowerShell backdoor is a characteristic example of unknown stealthy threats used in attacks on government, corporate, and private user systems.
Defenders need not only to be informed about the known or emerging threats but also to account for unknown vectors that may be capable of bypassing security measures and AV scans.
While some AV engines can heuristically detect malicious behavior in the PowerShell scripts, threat actors constantly evolve their code to bypass these detections.
The best way to achieve this is by applying security updates as quickly as possible, limiting remote access to endpoints, following the least privilege principle, and monitoring network traffic regularly.
- Karlston and aum
-

 2
2




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.