The StrongPity APT hacking group is distributing a fake Shagle chat app that is a trojanized version of the Telegram for Android app with an added backdoor.
Shagle is a legitimate random-video-chat platform allowing strangers to talk via an encrypted communications channel. However, the platform is entirely web-based, not offering a mobile app.
StrongPity has been found using a fake website since 2021 that impersonates the actual Shagle site to trick victims into downloading a malicious Android.
Once installed, this app enables the hackers to conduct espionage on the targeted victims, including monitoring phone calls, collecting SMS texts, and grabbing contact lists.
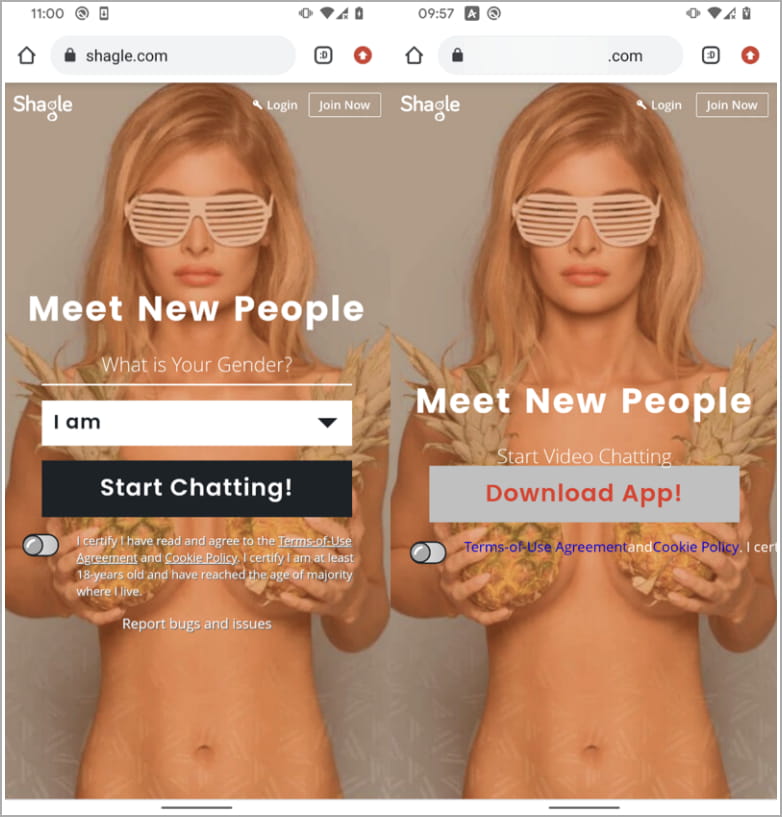
The real site is on the left. The fake site is on the right
Source: ESET
StrongPity, also known as Promethium or APT-C-41, was previously attributed to a campaign that distributed trojanized Notepad++ installers and malicious versions of WinRAR and TrueCrypt to infect targets with malware.
The latest StrongPity activity was discovered by ESET researchers who attributed the campaign to the espionage APT group based on code similarities with past payloads.
Additionally, the Android app is signed with the same certificate the APT used to sign an app that mimicked the Syrian e-gov Android application in a 2021 campaign.
Trojanizing the Android Telegram app
The malicious Android application distributed by StrongPity is an APK file named "video.apk," the standard Telegram v7.5.0 (February 2022) app modified to impersonate a Shagle mobile app.
ESET couldn't determine how victims arrive on the fake Shagle website, but it's likely through spear phishing emails, smishing (SMS phishing), or instant messages on online platforms.
The malicious APK is provided directly from the fake Shagle site and has never been made available on Google Play.
ESET says the cloned site first appeared online on November 2021, so the APK has likely been under active distribution since then. However, the first confirmed detection in the wild came in July 2022.
One drawback of using Telegram as the basis for the hacking group's fake app is that if the victim already has the real Telegram app installed on their phones, the backdoored version won't be installed.
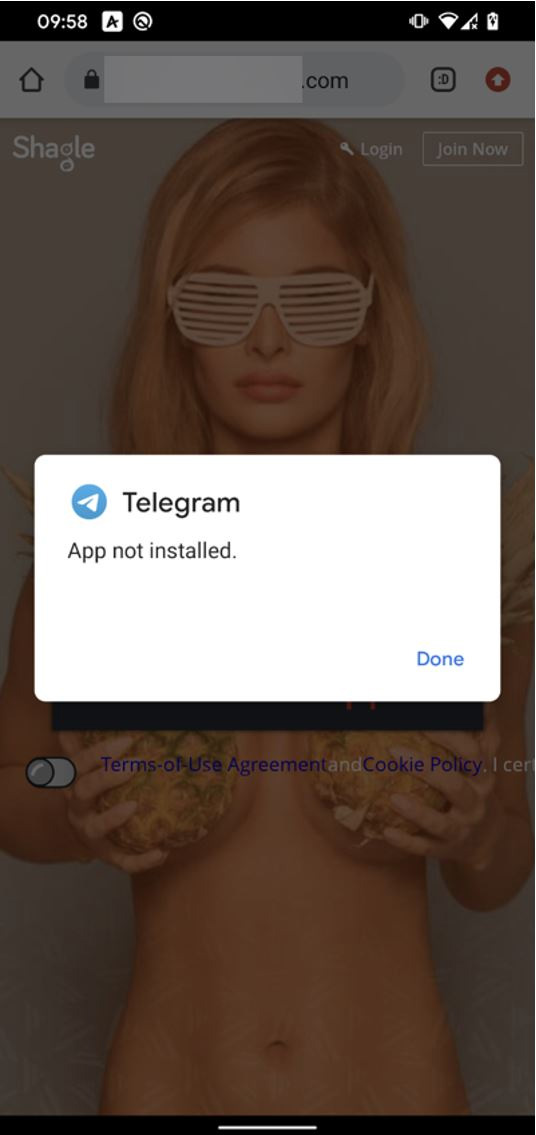
Malicious app won't install as Telegram installed already
Source: ESET
Currently, the API ID used in the captured samples has been limited due to overuse, so the trojanized app will no longer accept new user registrations; hence, the backdoor won't work.
ESET believes this indicates that StrongPity has successfully deployed the malware on targeted victims.
Backdoor designed to spy on victims
Upon installation, the malware requests access to Accessibility Service and then fetches an AES-encrypted file from the attacker's command and control server.
This file consists of 11 binary modules extracted to the device and used by the backdoor to perform various malicious functionality.
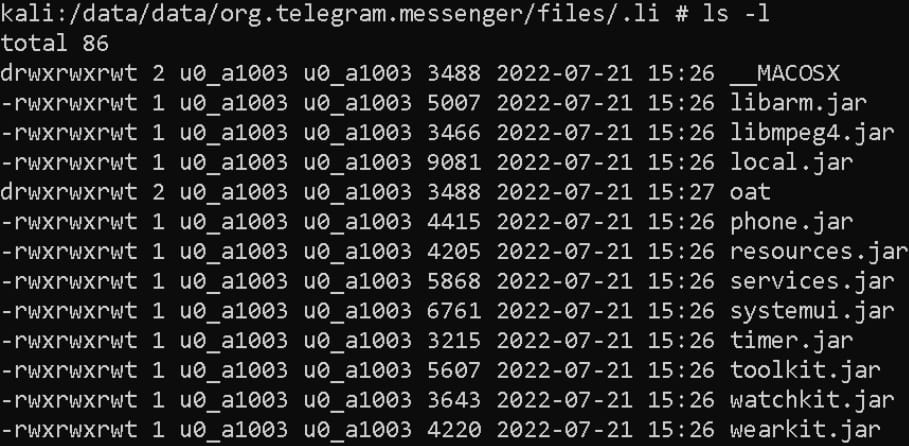
The 11 modules fetched from the C2
Source: ESET
Each module performs an espionage function and is triggered as needed. The complete list of the malicious spyware modules is listed below:
- libarm.jar – records phone calls
- libmpeg4.jar – collects text of incoming notification messages from 17 apps
- local.jar – collects file list (file tree) on the device
- phone.jar – misuses accessibility services to spy on messaging apps by exfiltrating contact name, chat message, and date
- resources.jar – collects SMS messages stored on the device
- services.jar – obtains device location
- systemui.jar – collects device and system information
- timer.jar – collects a list of installed apps
- toolkit.jar – collects contact list
- watchkit.jar – collects a list of device accounts
- wearkit.jar – collects a list of call logs
The gathered data is stored in the app's directory, encrypted with AES, and eventually sent back to the attacker's command and control server.
By abusing the Accessibility Service, the malware can read notification content from Messenger, Viber, Skype, WeChat, Snapchat, Tinder, Instagram, Twitter, Gmail, and more.
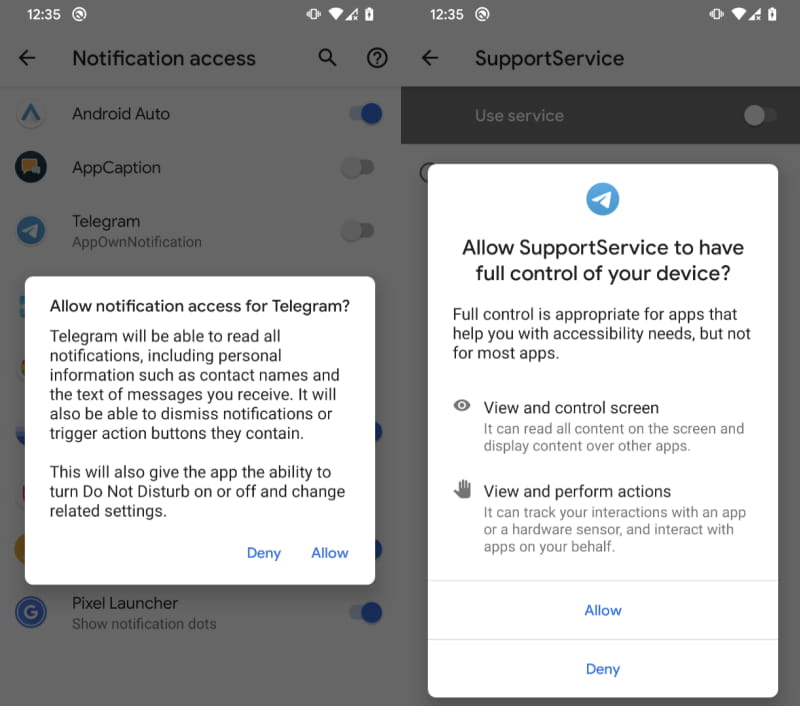
Trojan app requesting dangerous permissions
Source: ESET
In rooted devices where the regular user has administrator privileges, the malware automatically grants itself permission to perform changes on security settings, write on the filesystem, perform reboots, and perform other dangerous functions.
The StrongPity hacking group has been active since 2012, commonly hiding backdoors in legitimate software installers. Based on ESET’s report, the threat actor continues to employ the same tactic after a decade.
Android users should be cautious with APKs sourced outside Google Play and pay attention to permission requests while installing new apps.
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.