The U.S. Government today released an alert about state-backed hackers using a custom CovalentStealer malware and the Impacket framework to steal sensitive data from a U.S. organization in the Defense Industrial Base (DIB) sector.
The compromise lasted for about ten months and it is likely that multiple advanced persistent threat (APT) groups likely compromised the organization, some of them gaining initial access through the victim’s Microsoft Exchange Server in January last year.
Entities in the Defense Industrial Base Sector provide products and services that enable support and deployment of military operations.
They are engaged in the research, development, design, production, delivery, and maintenance of military weapons systems, including all necessary components and parts.
ProxyLogon, RAT, and custom malware
A joint report from the Cybersecurity and Infrastructure Agency (CISA), the Federal Bureau of Investigation (FBI), and the National Security Agency (NSA) provides technical details collected during incident response activity that lasted between November 2021 and January 2022.
The hackers combined custom malware called CovalentStealer, the open-source Impacket collection of Python classes, the HyperBro remote access trojan (RAT), and well over a dozen ChinaChopper webshell samples.
They also exploited the ProxyLogon collection of four vulnerabilities for Exchange Server around the time Microsoft released an emergency security update to fix them.
At the time, Microsoft had detected the ProxyLogon exploit chain when the vulnerabilities were zero days (unknown to the vendor), in attacks attributed to a Chinese state-sponsored hacking group they call Hafnium.
- CVE-2021-26855 is a server-side request forgery (SSRF) vulnerability in Exchange that allows sending arbitrary HTTP requests and authenticating as the Exchange server
- CVE-2021-26857 is an insecure deserialization vulnerability in the Unified Messaging service. Hafnium used it to run code as SYSTEM on the Exchange server
- CVE-2021-26858 is a post-authentication arbitrary file write vulnerability in Exchange. It could be exploited after compromising a legitimate admin’s credentials.
- CVE-2021-27065 is a post-authentication arbitrary file write vulnerability in Exchange
While the initial access vector is unknown, the current advisory notes that the hackers gained access to the organization’s Exchange Server in mid-January 2021.
Within four hours, the threat actor started mailbox searches and used a compromised administrator account belonging to a former employee to access the Exchange Web Services (EWS) API, which is used for sending and receiving web service messages from client applications.
Less than a month later, in early February 2021, the attackers accessed the network again using the same admin credentials through a virtual private network (VPN) connection.
After four days, the hackers engaged in reconnaissance activity using command shell. They learned about the victim’s environment and manually archived (WinRAR) sensitive data, e.g. contract-related information stored on shared drives, preparing it for exfiltration.
“These files were split into approximately 3MB chunks located on the Microsoft Exchange server within the CU2\he\debug directory” - joint report from CISA, FBI, and NSA
At the beginning of March, the hackers exploited the ProxyLogon vulnerabilities to install no less than 17 China Chopper webshells on the Exchange Server.
China Chopper carries powerful capabilities in a very small package (just 4 kilobytes). It was initially used by Chinese threat actors but it became so popular that other groups adopted it.
Activity to establish persistence on the network and to move laterally started in April 2021 and was possible Impacket, which allows working with network protocols.
CISA says that the attacker used Impacket with the compromised credentials to obtain a service account with higher privileges, which enabled remote access from multiple external IP addresses to the organization’s Exchange server through Outlook Web Access (OWA).
Accessing the remote Exchange Server was done through services from two VPN and virtual private server providers, M247 and SurfShark, a common tactic to hide the interaction with the victim network.
Burrowed deeply in the victim network, the hackers relied on the custom-built CovalentStealer to upload additional sensitive files to a Microsoft OneDrive location between late July and mid-October 2022.
In a separate report, CISA provides technical analysis for CovalentStealer noting that the malware relies on code from two publicly available utilities, ClientUploader and the PowerShell script Export-MFT, to upload compressed files and to extract the Master File Table (MFT) of a local storage volume.
CovalentStealer also contains resources for encrypting and decrypting the uploaded data, and configuration files, and to secure communications.
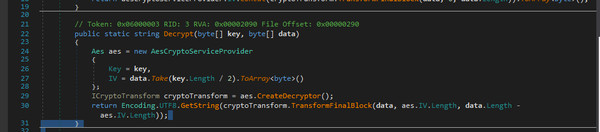
CISA shares technical details for the HyperBro RAT in distinct report, saying that the capabilities of the malware include uploading and downloading files to and from the system, logging keystrokes, executing commands on the infected host, and bypassing User Account Control protection to run with full admin privileges.
The U.S. government at this time does not provide an indication about the origin of the threat actors but notes that “CISA uncovered that likely multiple APT groups compromised the organization’s network.”
A set of recommendations are available in the joint report for detecting persistent, long-term access threat activity, one of them being to monitor logs for connections from unusual VPSs and VPNs.
Defenders should also examine connections from unexpected ranges and, for this particular attacker, check for machines hosted by SurfShark and M247.
Monitoring for suspicious account use, such as inappropriate or unauthorized use of administrator accounts, service accounts, or third-party accounts, is also on the list.
The use of compromised credentials with a VPS may also indicate a potential breach that could be uncovered by:
- Reviewing logs for "impossible logins," e.g. logins with changing username, user agent strings, and IP address combinations or logins where IP addresses do not align to the expected user’s geographic location
- Searching for "impossible travel," which occurs when a user logs in from multiple IP addresses that are a significant geographic distance apart. False positives can result from this when legitimate users connect through a VPN
- Searching for one IP used across multiple accounts, excluding expected logins (successful remote logins from M247 and SurfShark IPs may be a red flag)
- Identifying suspicious privileged account use after resetting passwords or applying user account mitigations
- Searching for unusual activity in typically dormant accounts
- Searching for unusual user agent strings, such as strings not typically associated with normal user activity, which may indicate bot activity
The joint report from CISA, FBI, and NSA shares a set of YARA rules created to detect activity from this particular threat actor and indicators of compromise for the tools used in the attack: CovalentStealer, HyperBro, and China Chopper.
- aum and Karlston
-

 2
2




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.