Hackers Spread BIOPASS Malware via Chinese Online Gambling Sites
Cybersecurity researchers are warning about a new malware that's striking online gambling companies in China via a watering hole attack to deploy either Cobalt Strike beacons or a previously undocumented Python-based backdoor called BIOPASS RAT that takes advantage of Open Broadcaster Software (OBS) Studio's live-streaming app to capture the screen of its victims to attackers.
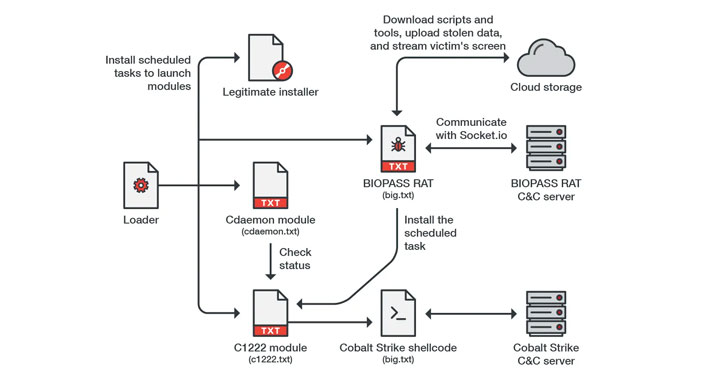
The attack involves deceiving gaming website visitors into downloading a malware loader camouflaged as a legitimate installer for popular-but-deprecated apps such as Adobe Flash Player or Microsoft Silverlight, only for the loader to act as a conduit for fetching next-stage payloads.
Specifically, the websites' online support chat pages are booby-trapped with malicious JavaScript code, which is used to deliver the malware to the victims.
"BIOPASS RAT possesses basic features found in other malware, such as file system assessment, remote desktop access, file exfiltration, and shell command execution," Trend Micro researchers noted in an analysis published Friday. "It also has the ability to compromise the private information of its victims by stealing web browser and instant messaging client data."
OBS Studio is an open-source software for video recording and live streaming, enabling users to stream to Twitch, YouTube, and other platforms.
Besides featuring an array of capabilities that run the typical spyware gamut, BIOPASS is equipped to establish live streaming to a cloud service under the attacker's control via Real-Time Messaging Protocol (RTMP), in addition to communicating with the command-and-control (C2) server using the Socket.IO protocol.
The malware, which is said to be under active development, is also notable for its focus on stealing private data from web browsers and instant messaging apps chiefly popular in Mainland China, including QQ Browser, 2345 Explorer, Sogou Explorer, and 360 Safe Browser, WeChat, QQ, and Aliwangwang.
It isn't clear exactly as to who is behind this malware strain, but Trend Micro researchers said they found overlaps between BIOPASS and that of TTPs often associated with the Winnti Group (aka APT41), a sophisticated Chinese hacking group specialized in cyber espionage attacks, based on the use of stolen certificates and a Cobalt Strike binary that was previously attributed to the threat actor.
What's more, the same Cobalt Strike binary has also been connected to a cyber attack targeting MonPass, a major certification authority (CA) in Mongolia, earlier this year wherein its installer software was tampered with to install Cobalt Strike beacon payloads on infected systems.
"BIOPASS RAT is a sophisticated type of malware that is implemented as Python scripts," the researchers said. "Given that the malware loader was delivered as an executable disguised as a legitimate update installer on a compromised website, [...] it is recommended to download apps only from trusted sources and official websites to avoid being compromised."
- Karlston and Mutton
-

 2
2


Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.