Cybersecurity researchers are calling attention to a free-to-use browser automation framework that's being increasingly used by threat actors as part of their attack campaigns.
"The framework contains numerous features which we assess may be utilized in the enablement of malicious activities," researchers from Team Cymru said in a new report published Wednesday.
"The technical entry bar for the framework is purposefully kept low, which has served to create an active community of content developers and contributors, with actors in the underground economy advertising their time for the creation of bespoke tooling."
The U.S. cybersecurity company said it observed command-and-control (C2) IP addresses associated with malware such as Bumblebee, BlackGuard, and RedLine Stealer establishing connections to the downloads subdomain of Bablosoft ("downloads.bablosoft[.]com"), the maker of the Browser Automation Studio (BAS).
Bablosoft was previously documented by cloud security and application delivery firm F5 in February 2021, pointing to the framework's ability to automate tasks in Google's Chrome browser in a manner similar to legitimate developer tools like Puppeteer and Selenium.
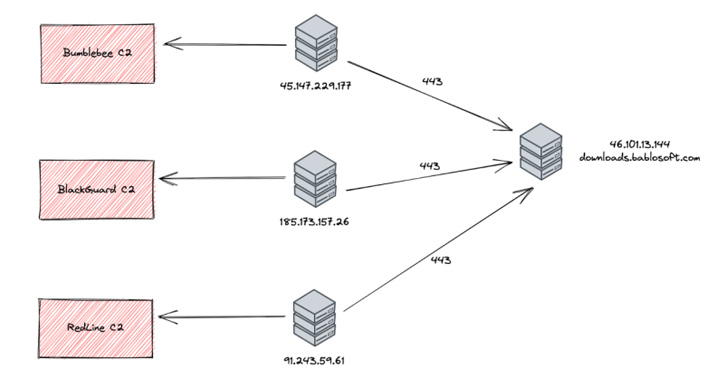
Threat telemetry for the subdomain's IP address — 46.101.13[.]144 — shows that a vast majority of activity is originating from locations in Russia and Ukraine, with open source intelligence indicating that Bablosoft's owner is allegedly based in the Ukrainian capital city of Kyiv.
It's being suspected that the operators of the malware campaigns connected to the Bablosoft subdomain for purposes of downloading additional tools for use as part of post-exploitation activities.
Also identified are several hosts associated with cryptojacking malware like XMRig and Tofsee communicating with a second subdomain named "fingerprints.bablosoft[.]com" to use a service that helps the mining malware conceal its behavior.
"Based on the number of actors already utilizing tools offered on the Bablosoft website, we can only expect to see BAS becoming a more common element of the threat actor's toolkit," the researchers said.


Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.