Hackers are abusing the open-source Linux PRoot utility in BYOF (Bring Your Own Filesystem) attacks to provide a consistent repository of malicious tools that work on many Linux distributions.
A Bring Your Own Filesystem attack is when threat actors create a malicious filesystem on their own devices that contain a standard set of tools used to conduct attacks.
This file system is then downloaded and mounted on compromised machines, providing a preconfigured toolkit that can be used to compromise a Linux system further.
"First, threat actors build a malicious filesystem which will be deployed. This malicious filesystem includes everything that the operation needs to succeed," explains a new report by Sysdig.
"Doing this preparation at this early stage allows all of the tools to be downloaded, configured, or installed on the attacker's own system far from the prying eyes of detection tools."
Sysdig says the attacks typically lead to cryptocurrency mining, although more harmful scenarios are possible.
The researchers also warn about how easy this novel technique could make scaling malicious operations against Linux endpoints of all kinds.
Abusing the Linux PRoot utility
PRoot is an open-source utility that combines the 'chroot', 'mount --bind', and 'binfmt_misc' commands, allowing users to set up an isolated root filesystem within Linux.
By default, the PRoot processes are confined within the guest filesystem; however, QEMU emulation can be used to mix host and guest programs execution.
Additionally, programs from within the guest filesystem can use the built-in mount/bind mechanism to access files and directories from the host system.
The attacks seen by Sysdig use PRoot to deploy a malicious filesystem on already compromised systems that include network scanning tools like "masscan" and "nmap," the XMRig cryptominer, and their configuration files.
The filesystem contains everything required for the attack, neatly packaged in a Gzip-compressed tar file with all the necessary dependencies, dropped directly from trusted cloud hosting services like DropBox.
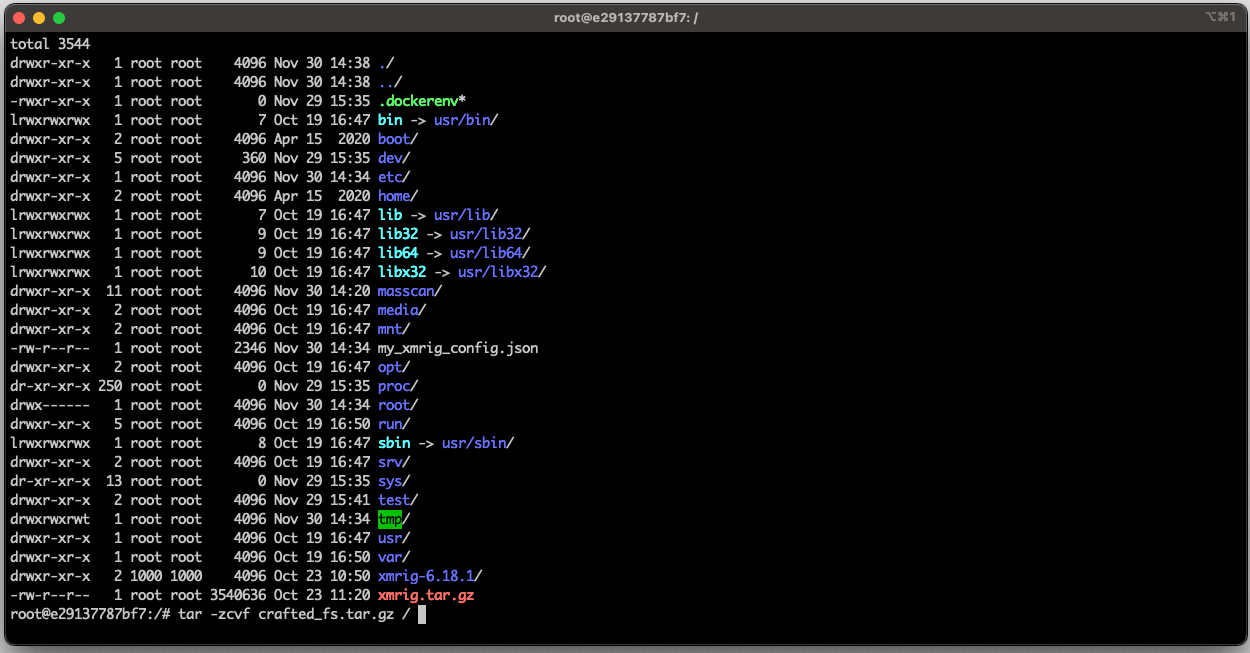
The malicious guest filesystem (Sysdig)
As PRoot is statically compiled and doesn't require any dependencies, threat actors simply download the precompiled binary from GitLab, and execute it against the attacker's downloaded and extracted filesystem to mount it.
In most cases seen by Sysdig, the attackers unpacked the filesystem on '/tmp/Proot/' and then activated the XMRig cryptominer.
"Any dependencies or configurations are also included in the filesystem, so the attacker does not need to run any additional setup commands," explains Sysdig
"The attacker launches PRoot, points it at the unpacked malicious filesystem, and specifies the XMRig binary to execute."
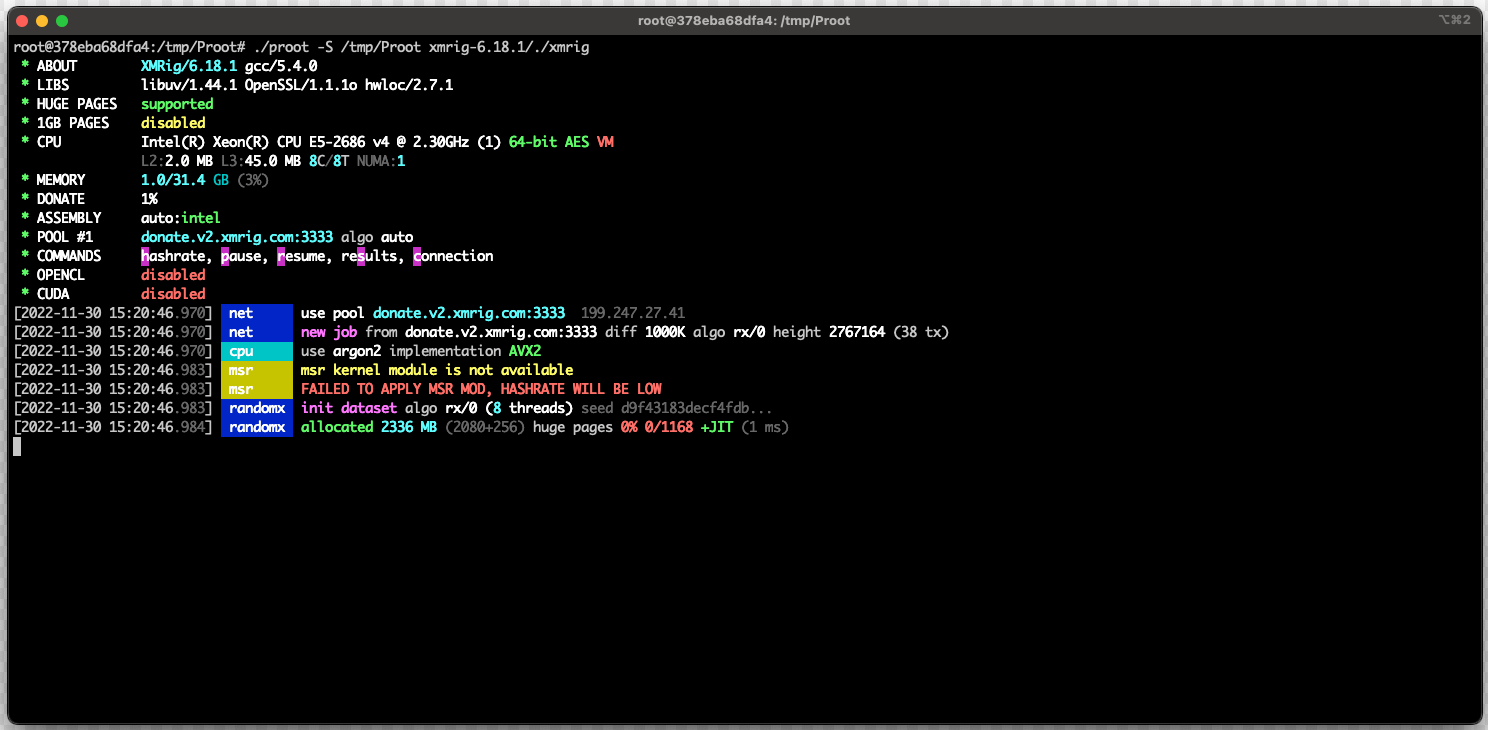
Launching XMRig on the guest filesystem to mine using host's GPU (Sysdig)
As Sysdig highlights in the report, the threat actors could easily use PRoot to download other payloads besides XMRig, potentially causing more severe damage to the breached system.
The presence of "mascan" on the malicious filesystem implies an aggressive stance by the attackers, likely indicating they plan on breaching other systems from the compromised machine.
Streamlining attacks
The abuse of PRoot by hackers makes these post-exploitation attacks platform and distribution-agnostic, increasing the chances of success and the threat actors' stealthiness.
Moreover, pre-configured PRoot filesystems allow attackers to use a toolkit across many OS configurations without having to port their malware to the targeted architecture or include dependencies and build tools.
"Using PRoot, there is little regard or concern for the target’s architecture or distribution since the tool smoothes out the attack struggles often associated with executable compatibility, environment setup, and malware and/or miner execution,"
explains Sysdig.
"It allows attackers to get closer to the philosophy of “write once, run everywhere,” which is a long sought-after goal."
Attacks backed by PRoot make the environment setup irrelevant for the hackers, enabling them to scale up their malicious operations quickly.
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.