Hackers are exploiting a critical command injection vulnerability in Zyxel CPE Series devices that is currently tracked as CVE-2024-40891 and remains unpatched since last July.
The vulnerability allows unauthenticated attackers to execute arbitrary commands using the ‘supervisor’ or ‘zyuser’ service accounts.
Vulnerability intelligence company VulnCheck added the security issue to its database last year on July 12 and listed it among other issues exploited in the wild for initial access.
Technical details on the vulnerability have not been publicly disclosed and Zyxel did not release a security advisory or a patch for CVE-2024-40891, and the issue remains exploitable in the latest firmware.
It appears that hackers discovered how to leverage the vulnerability and are using it in attacks as threat monitoring platform GreyNoise has observed recently exploitation activity originating from multiple unique IP addresses.
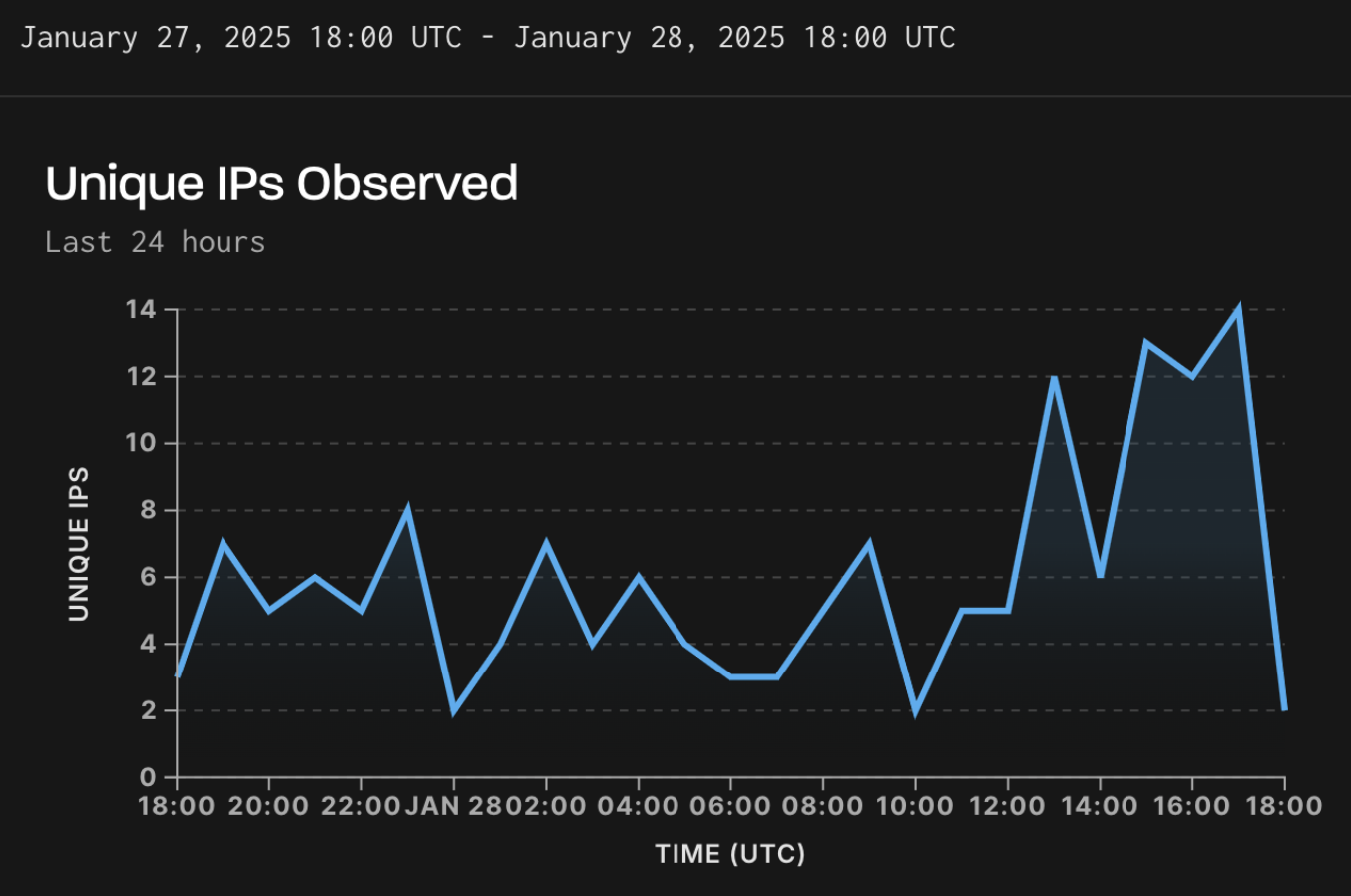
Source: GreyNoise
GreyNoise notes that the flaw is similar to CVE-2024-40890, which is HTTP-based. However, VulnCheck confirmed that the current exploitation detection is for the unpatched CVE-2024-40891, which is based on the telnet protocol.
“GreyNoise is observing active exploitation attempts targeting a zero-day critical command injection vulnerability in Zyxel CPE Series devices tracked as CVE-2024-40891,” reads the bulletin.
“At this time, the vulnerability is not patched, nor has it been publicly disclosed. Attackers can leverage this vulnerability to execute arbitrary commands on affected devices, leading to complete system compromise, data exfiltration, or network infiltration” - GreyNoise
Internet scanning service Censys reports that there are more than 1,500 Zyxel CPE Series devices currently exposed online, mostly in the Philippines, Turkey, the United Kingdom, France, and Italy.
Considering that no security update is available to address the problem, system administrators should at least try to block the IP addresses launching the exploitation attempts. However, this attacks from other IP addresses are still possible.
For further mitigation, it is recommended to monitor traffic for atypical telnet requests to Zyxel CPE management interfaces, and restrict access to the administrative interface only to a specified IP allowlist.
If remote management features are not used/needed, it is better to disable them entirely to reduce the attack surface.
BleepingComputer has contacted Zyxel with a request for a comment, but we are still waiting for the vendor’s response.
Hope you enjoyed this news post.
Thank you for appreciating my time and effort posting news every day for many years.
News posts... 2023: 5,800+ | 2024: 5,700+
RIP Matrix | Farewell my friend ![]()
- Mutton and phen0men4
-

 2
2



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.