Pwn2Own Vancouver 2024 has ended with security researchers collecting $1,132,500 after demoing 29 zero-days (and some bug collisions).
Throughout the event, they targeted software and products in the web browser, cloud-native/container, virtualization, enterprise applications, server, local escalation of privilege (EoP), enterprise communications, and automotive categories, all up-to-date and in their default configuration.
The total prize pool was over $1,300,000 in cash prizes and a Tesla Model 3, which Team Synacktiv won on the first day.
Competitors successfully gained code execution and escalated privileges on fully patched systems after hacking Windows 11, Ubuntu Desktop, VMware Workstation, Oracle VirtualBox, three web browsers (Apple Safari, Google Chrome, and Microsoft Edge), and the Tesla Model 3.
Vendors have 90 days to release security fixes for zero-day vulnerabilities reported during Pwn2Own contests before TrendMicro's Zero Day Initiative discloses them publicly.
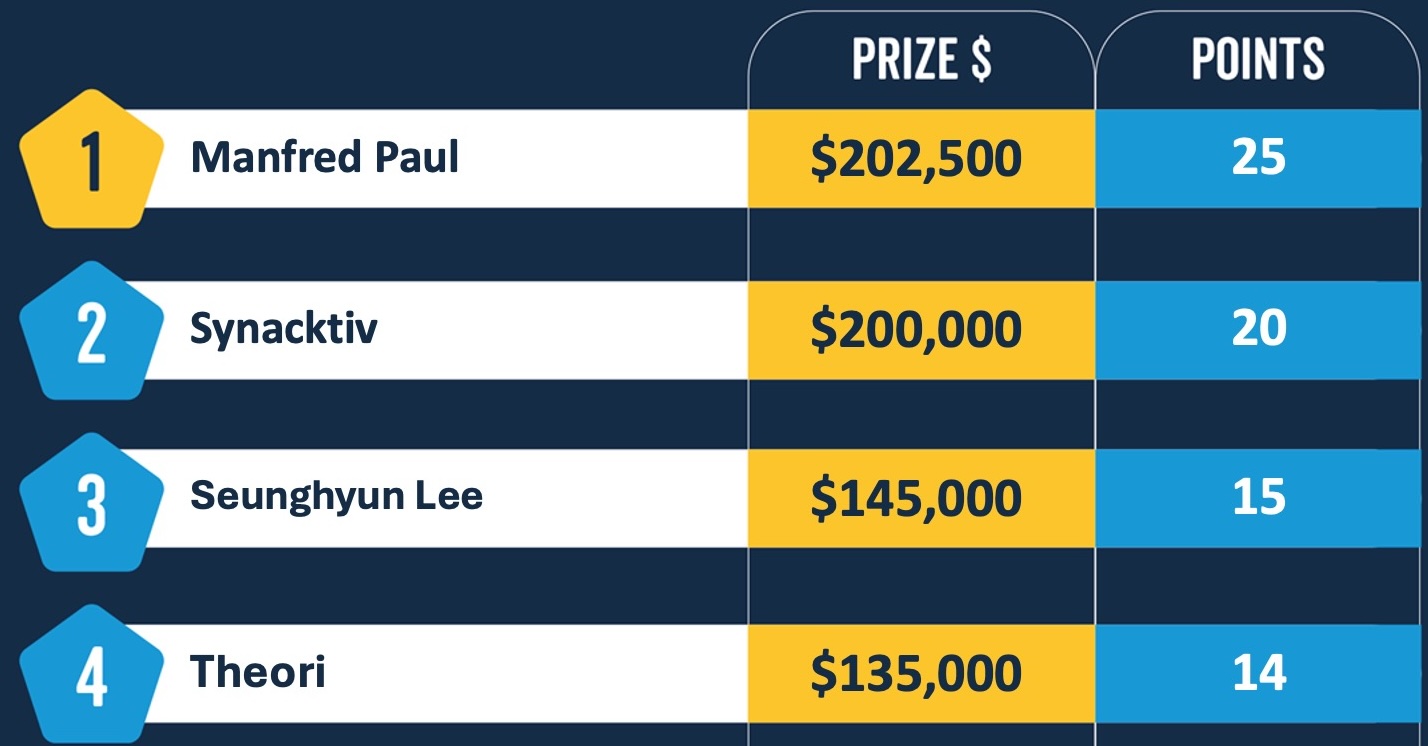
Manfred Paul won this year's edition of Pwn2Own Vancouver with 25 Master of Pwn points and $202,500 earned throughout the two-day competition after hacking the Apple Safari, Google Chrome, and Microsoft Edge web browsers.
On the first day of Pwn2Own, he gained remote code execution (RCE) in Safari via an integer underflow bug and a PAC bypass zero-day combo. He then used a double-tap RCE exploit targeting an Improper Validation of Specified Quantity in Input weakness to take down Chrome and Edge.
Synacktiv also made Pwn2Own Vancouver 2024's Day 1 highlight reel after winning a Tesla Model 3 car and $200,000 after hacking the Tesla ECU with Vehicle (VEH) CAN BUS Control in under 30 seconds using an integer overflow exploit.
On the second day, Manfred Paul also exploited an out-of-bounds (OOB) write zero-day vulnerability to gain RCE and escaped Mozilla Firefox's sandbox using an exposed dangerous function weakness.
Other successful attempts (and bug collisions) on the last day include:
- Windows 11 privilege escalation exploits from HackInside, IBM X-Force's Valentina Palmiotti, Marcin Wiązowski, and Gabriel Kirkpatrick,
- STAR Labs SG's VMware Workstation RCE and Ubuntu Linux privilege escalation exploits and a Docker escape,
- Palo Alto's team hacking Chrome and Edge after defeating V8 hardening,
- ColdEye's Oracle VirtualBox guest-to-host escape exploit,
- KAIST Hacking Lab's Seunghyun Lee double-tap Chrome and Edge RCE exploit,
- Theori with a privilege escalation on Ubuntu Linux.
ZDI has awarded $3,494,750 during the last three Pwn2Ownco hacking contests (Toronto, Tokyo Automotive, and Vancouver).
Also, at Pwn2Own Vancouver 2023, hackers collected another $1,035,000 in awards and a Tesla car (won by Synaktiv) for 27 zero-days in Windows 11, Microsoft Teams, Microsoft SharePoint, macOS, Ubuntu Desktop, VMware Workstation, Oracle VirtualBox, and Tesla's Model 3.



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.