The Pwn2Own Berlin 2025 hacking competition has concluded, with security researchers earning $1,078,750 after exploiting 29 zero-day vulnerabilities and encountering some bug collisions.
Throughout the contest, they targeted enterprise technologies in the AI, web browser, virtualization, local privilege escalation, servers, enterprise applications, cloud-native/container, and automotive categories.
According to Pwn2Own's rules, all targeted devices had all security updates installed and ran the latest operating system versions.
While Tesla also provided two 2025 Tesla Model Y and 2024 Tesla Model 3 bench-top units, security researchers who joined the contest haven't registered any attempts in this category before Pwn2Own started.
Competitors collected $260,000 in cash awards after the first day and another $435,000 on the second day after exploiting 20 zero-day vulnerabilities. On the third day of Pwn2Own, they collected another $383,750 for eight more zero-days.
After these vulnerabilities are demoed during Pwn2Own events, vendors have 90 days to release security updates before TrendMicro's Zero Day Initiative publicly discloses them.
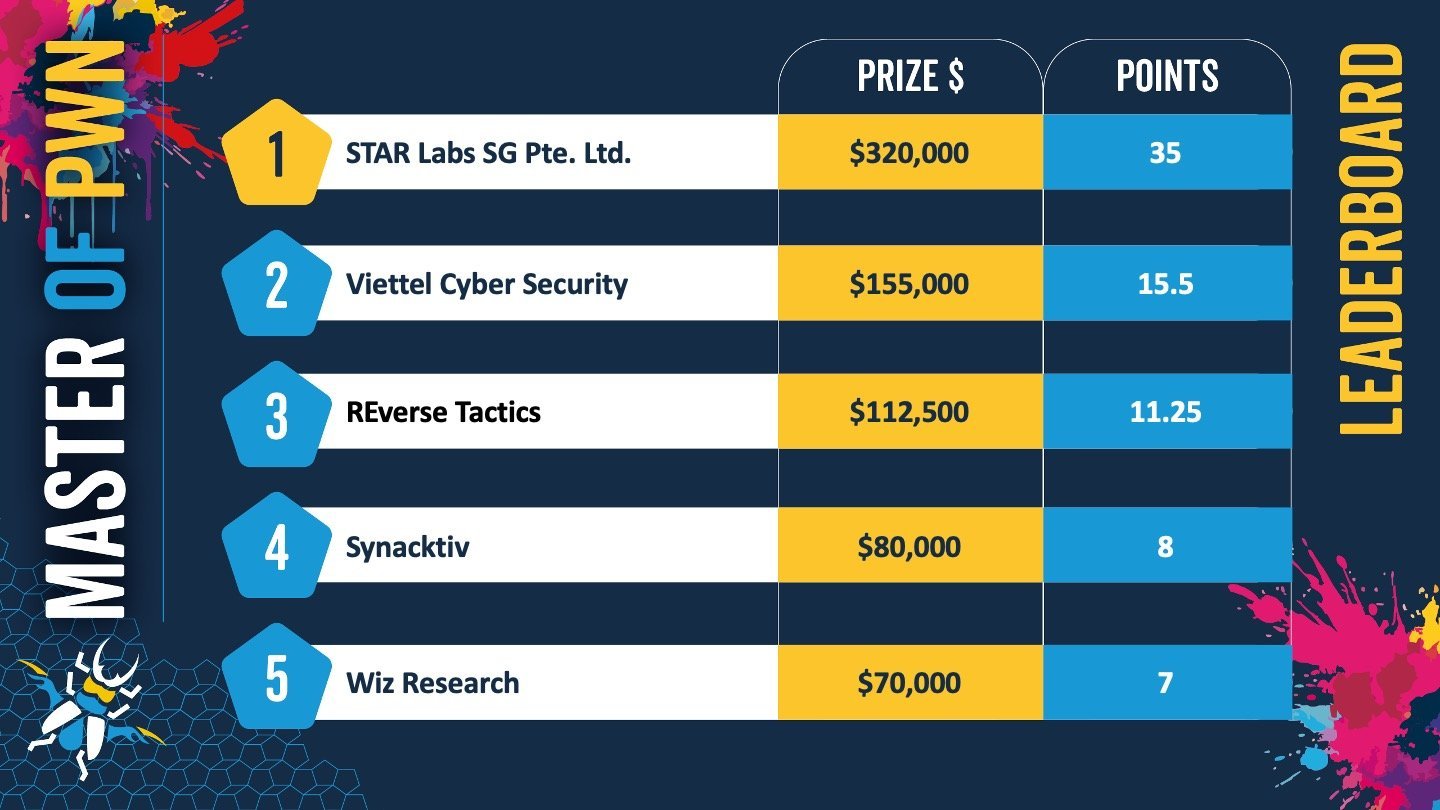
The STAR Labs SG team won this year's edition of Pwn2Own Berlin with 35 Master of Pwn points and $320,000 earned throughout the three-day contest after hacking Red Hat Enterprise Linux, Docker Desktop, Windows 11, VMware ESXi, and Oracle VirtualBox.
STAR Labs' Nguyen Hoang Thach won the competition's highest reward of $150,000 after using an integer overflow exploit to hack the VMware ESXi hypervisor software.
Team Viettel Cyber Security took second place after demonstrating zero-day flaws that could let attackers escape to the host system from Oracle VirtualBox guests and hack Microsoft SharePoint using an exploit chain combining an auth bypass and an insecure deserialization.
On the third day, team Reverse Tactics again hacked VMware's hypervisor software using an exploit chain abusing an integer overflow and an uninitialized variable bug to earn $112,500 and take third place in the rankings.
Mozilla has already patched the two Firefox zero-day bugs (CVE-2025-4918 and CVE-2025-4919) demoed during the competition after releasing Firefox 138.0.4, Firefox ESR 128.10.1, Firefox ESR 115.23.1, and a new Firefox for Android version over the weekend to address them.
In March 2024, Mozilla fixed two other zero-day vulnerabilities in the Firefox web browser (CVE-2024-29943 and CVE-2024-29944) after security researcher Manfred Paul exploited and reported them at Pwn2Own Vancouver 2024.
Hope you enjoyed this news post.
Thank you for appreciating my time and effort posting news every day for many years.
News posts... 2023: 5,800+ | 2024: 5,700+ | 2025 (till end of April): 1,811
RIP Matrix | Farewell my friend ![]()
- phen0men4
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.