Security researchers have revealed that hackers can hijack your online accounts before you even register them by exploiting flaws that have been already been fixed on popular websites, including Instagram, LinkedIn, Zoom, WordPress, and Dropbox.
Andrew Paverd, a researcher at Microsoft Security Response Center, and Avinash Sudhodanan, an independent security researcher, analyzed 75 popular online services and found that at least 35 are vulnerable to account pre-hijacking attacks.
These attacks vary in type and severity, but they all stem from poor security practices on the side of the websites themselves.
As some vulnerable websites run bug bounty programs, it is surprising and worrying to see that such elementary attacks are still possible against their users.
"The impact of account pre-hijacking attacks is the same as that of account hijacking. Depending on the nature of the target service, a successful attack could allow the attacker to read/modify sensitive information associated with the account (e.g., messages, billing statements, usage history, etc.) or perform actions using the victim's identity (e.g., send spoofed messages, make purchases using saved payment methods, etc.)." - A. Paverd, A. Sudhodanan.
How pre-hijacking works
For a pre-hijacking attack to work, the hacker needs to know a target's email address, which is relatively easy through email correspondence or via the numerous data breaches that plague companies daily.
Next, an attacker creates an account on a vulnerable site using the target's email address and hopes that the victim dismisses the notification that arrives in their inbox, deeming it spam. Finally, the attacker waits for the victim to create an account on the site or indirectly tricks them into doing it.
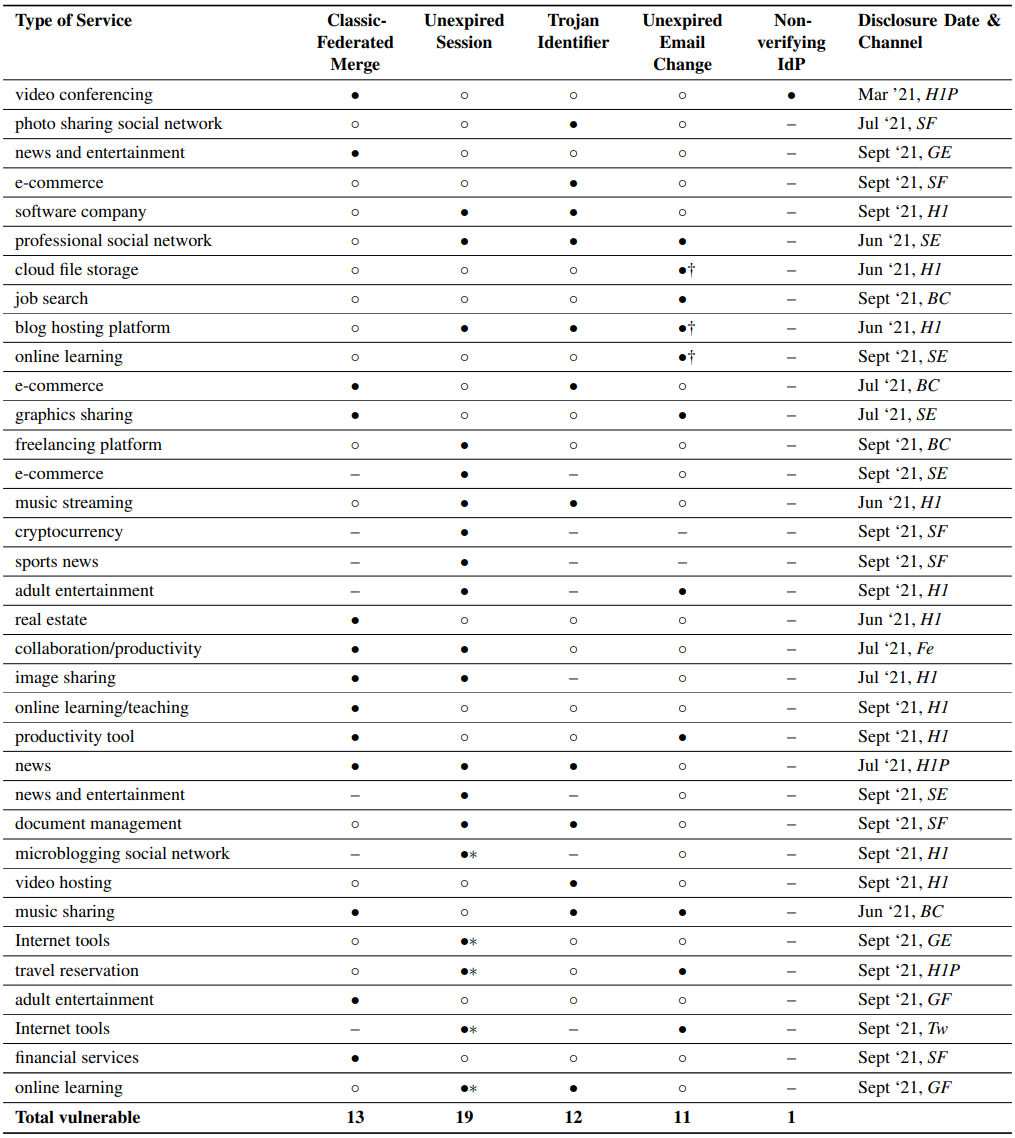
During this process, there are five different attacks that threat actors can conduct, namely the classic-federated merge (CFM), the unexpired session (US) ID, the trojan identifier (TID), the unexpired email change (UEC), and the non-verifying Identity provider (IdP) attack (NV).
In the first case, CFM, the vulnerable platform uses account merging when the target creates an account with an existing email address and, in some cases, doesn't even inform them of the fact. This attack relies on giving the victim a single-sign-on (SSO) option, so they never change the password set by the attacker.
In the unexpired session attack, the hacker keeps the session active after creating the account using an automated script. When the victim creates an account and resets the password, the active session might not be invalidated, so the attacker can continue accessing the account.
The trojan identifier method combines the Classic-Federated Merge and Unexpired Session attacks.
"The attacker creates a pre-hijacked account using the victim’s email address, but then associates the account with the attacker’s IdP account for federated authentication. When the victim resets the password (as in the Unexpired Session Attack), the attacker can still access the account via the federated authentication route," explains the paper.
In the UEC attack, the attacker creates an account using the victim's email address and then submits a change request for that email but doesn't confirm it. Then, after the victim performs the password reset, the attacker validates the change and assumes control of the account.
Finally, in the NV attack, the threat actor exploits the lack of verifying ownership of an IdP when creating the account, opening up the way to abuse cloud-based login services like Okta and Onelogin.
.png)
Bypassing the email verification step
Many services today require new users to validate ownership of the email address, so creating new accounts with other people's email addresses wouldn't work without access to the email account.
To bypass this, the attacker can create the account using their email address and then switch to the victim's email address, abusing a standard functionality available in most online services.
In some cases, the service will not require a second verification for the new email address, allowing the threat actors to mount the attacks described above.
Results and protection
The study shows that the availability of the different attacks are similar, with the unexpired session issue being the most common in the limited dataset.
Some notable examples of vulnerable platforms are Dropbox (UEC), Instagram (TID), LinkedIn (US), Wordpress.com (US and UEC), and Zoom (CFM and NV).
The researchers reported these problems responsibly to the platforms, many of which fixed them after categorizing them as high severity.
However, it is crucial to underline that these findings concern only a handful of sites, and there should be many more following similar lousy security practices.
The main issue with this subcategory of security problems and the root cause of the identified vulnerabilities is the lack of strict verification.
As the analysts explain, the reason behind these flawed systems is that all online platforms want to minimize friction during sign-up as much as possible, which has an adverse effect on account security.
To deal with the risk of pre-hijacked accounts, users can immediately set up MFA (multi-factor authentication) on their accounts, which should also force all previous sessions to be invalidated.
Hackers can hack your online accounts before you even register them



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)


Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.