A new malicious campaign is using a legitimate but old and vulnerable Avast Anti-Rootkit driver to evade detection and take control of the target system by disabling security components.
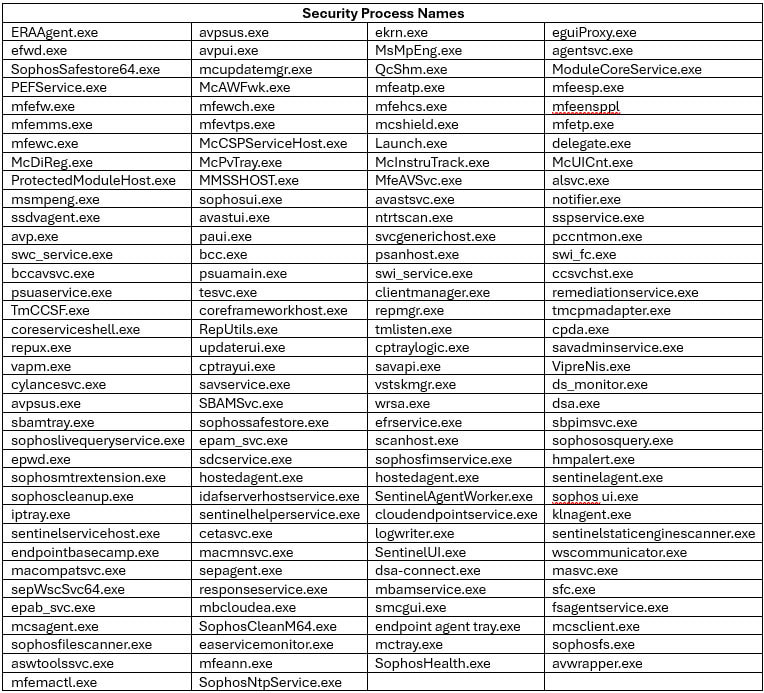
The malware that drops the driver is a variant of an AV Killer of no particular family. It comes with a hardcoded list of 142 names for security processes from various vendors.
Since the driver can operate at kernel level, it provides access to critical parts of the operating system and allows the malware to terminate processes.
Security researchers at cybersecurity company Trellix recently discovered a new attack that leverages the bring-your-own-vulnerable-driver (BYOVD) approach with an old version of the anti-rootkit driver to stop security products on a targeted system.
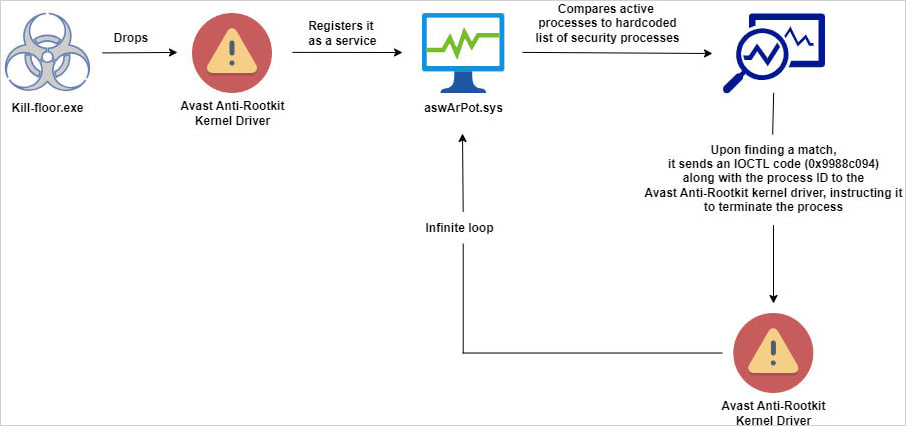
They explain that a piece a piece of malware with the file name kill-floor.exe drops the vulnerable driver with the file name ntfs.bin in the default Windows user folder. Next, the malware creates the service ‘aswArPot.sys’ using the Service Control (sc.exe) and registers the driver.
Source: Trellix
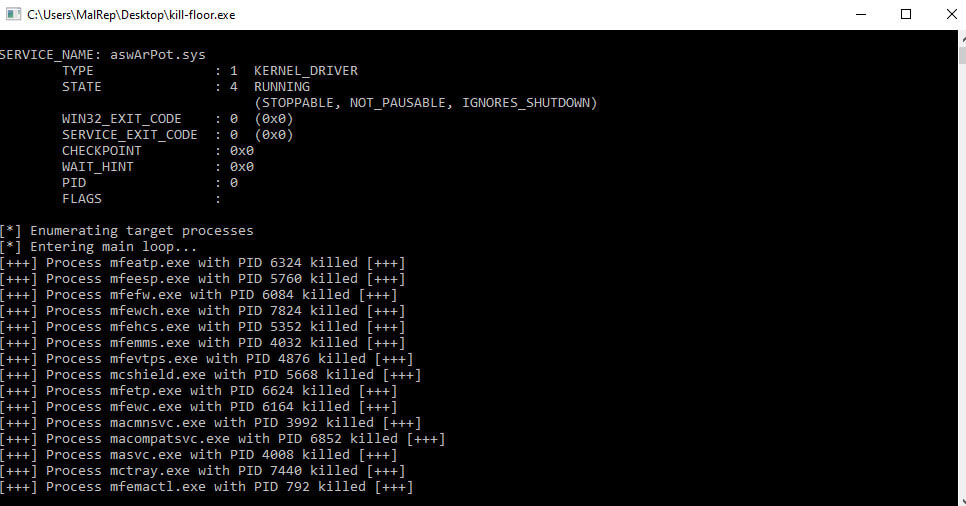
The malware then uses a hardcoded list of 142 processes associated with security tools and checks it against multiple snapshots of active processes on the system.
Trellix researcher Trishaan Kalra says that when it finds a match, "the malware creates a handle to reference the installed Avast driver."
It then leverages the ‘DeviceIoControl’ API to issue the required IOCTL commands to terminate it.
Source: Trellix
As seen in the screenshot above, the malware targets processes from various security solutions, including those from McAfee, Symantec (Broadcom), Sophos, Avast, Trend Micro, Microsoft Defender, SentinelOne, ESET, and BlackBerry.
With defenses deactivated, the malware can perform malicious activities without triggering alerts to the user or getting blocked.
Source: Trellix
It is worth noting that the driver and similar procedures were observed in early 2022 by researchers at Trend Micro while investigating an AvosLocker ransomware attack.
In December 2021, the Stroz Friedberg’s Incident Response Services team found that Cuba ransomware used in attacks a script that abused a function in Avast's Anti-Rootkit kernel driver to kill security solutions on victim's systems.
Around the same time, researchers at SentinelLabs discovered discovered two high-severity flaws (CVE-2022-26522 and CVE-2022-26523) that had been present since 2016, which could be exploited "to escalate privileges enabling them to disable security products."
The two issues were reported to Avast in December 2021 and the company addressed them silently with security updates.
Protecting against attacks that rely on vulnerable drivers is possible by using rules that can identify and block components based on their signatures or hashes, such as this one that Trellix recommends.
Microsoft also has solutions, such as the vulnerable driver blocklist policy file, which is updated with every major Windows release. Starting Windows 11 2022, the list is active by default on all devices. The latest version of the list is possible through App Control for Business.
Hope you enjoyed this news post.
Thank you for appreciating my time and effort posting news every day for many years.
2023: Over 5,800 news posts | 2024 (till end of October): 4,832 news posts
RIP Matrix | Farewell my friend ![]()



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.