Hackers are conducting widescale attacks on WordPress sites to inject scripts that force visitors' browsers to bruteforce passwords for other sites.
The campaign was first spotted by website cybersecurity firm Sucuri, which has been tracking a threat actor known for breaching sites to inject crypto wallet drainer scripts.
Crypto wallet drainers are malicious scripts that steal all cryptocurrency and assets when someone connects their wallet.
When people visit these compromised sites, the scripts display misleading messages to convince users to connect their wallets to the site. However, once they do so, the scripts steal all the contained assets.
These scripts have become very common over the past year, with threat actors creating fake Web3 sites with wallet drainers. They then hack X accounts, create YouTube videos, or take out Google and X advertisements to promote the sites and steal visitor's cryptocurrency.
Sucuri researchers reported that the threat actors were breaching compromised WordPress sites to inject the AngelDrainer wallet drainer in multiple waves from multiple URLs, the last being 'dynamiclink[.]lol/cachingjs/turboturbo.js.'
In late February, the threat actor switched from wallet draining to hijacking visitors' browsers to bruteforce other WordPress sites. using a malicious script from a newly registered domain 'dynamic-linx[.]com/chx.js'.
Building a bruteforce army
According to a new report from Sucuri, the threat actor is using compromised WordPress sites to load scripts that force visitors' browsers to conduct bruteforce attacks for account credentials on other websites.
A bruteforce attack is when a threat actor attempts to log in to an account using different passwords to guess the correct one. With the credentials, the threat actor can steal data, inject malicious scripts, or encrypt files on the site.
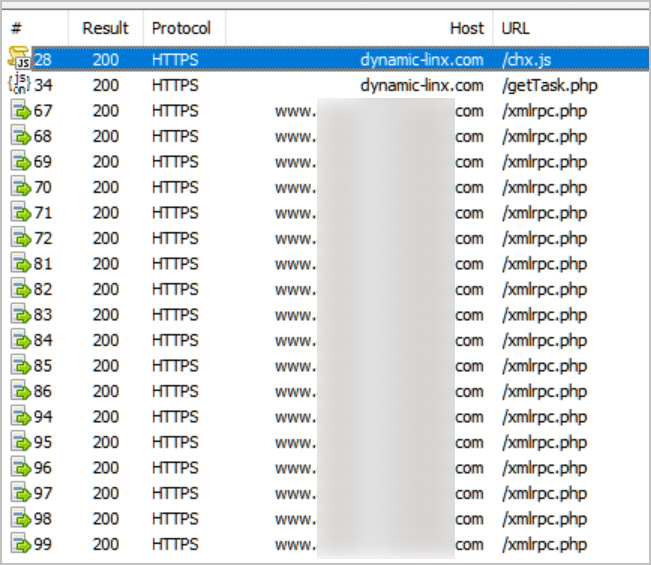
As part of this hacking campaign, the threat actors compromise a WordPress site to inject malicious code into the HTML templates. When visitors access the website, the scripts are loaded in their browser from https://dynamic-linx[.]com/chx.js.
These scripts will cause the browser to quietly contact the threat actors' server at 'https://dynamic-linx[.]com/getTask.php' to receive a password bruteforcing task.
This task comes in the form of a JSON file containing the parameters for the bruteforce attack: an ID, the website URL, account name, a number denoting the current batch of passwords to go through, and one hundred passwords to try.
Once the task is received, the script will cause the visitor's browser to quietly upload a file using the WordPress site's XMLRPC interface using the account name and passwords in the JSON data.
If a password is accurate, the script will notify the threat actor's server that a password was found for the site. The hacker can then connect to the site to retrieve the uploaded file containing the base64 encoded username and password pair.
As long as the page remains open, the malicious script will cause the web browser to repeatedly connect back to the attacker's server and retrieve a new task to execute.
According to the HTML source code search engine PublicHTML, there are currently over 1,700 sites hacked with these scripts or their loaders, providing a massive pool of users who will be unwittingly conscripted into this distributed bruteforce army.
CronUp researcher Germán Fernández found that the website of Ecuador's Association of Private Banks was compromised in this campaign, acting as a watering hole for unsuspecting visitors.
It is unclear why the threat actors switched from injecting crypto wallet drainers to bruteforcing other sites. However, Sucuri believes it is to build a more extensive portfolio of sites from which to launch further attacks at a larger scale, such as crypto-draining attacks.
"Most likely, they realized that at their scale of infection (~1000 compromised sites) the crypto drainers are not very profitable yet," concluded Sucuri researcher Denis Sinegubko.
"Moreover, they draw too much attention and their domains get blocked pretty quickly. So, it appears reasonable to switch the payload with something stealthier, that at the same time can help increase their portfolio of compromised sites for future waves of infections that they will be able to monetize in one way or another."



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.