The Gootkit loader malware operators are running a new SEO poisoning campaign that abuses VLC Media Player to infect Australian healthcare entities with Cobalt Strike beacons.
The campaign goal is to deploy the Cobalt Strike post-exploitation toolkit on infected devices for initial access to corporate networks.
From there, the remote operators can perform network scans, move laterally throughout the network, steal account credentials and files, and deploy more dangerous payloads such as ransomware.
Gootkit loader, more commonly known as Gootloader, began delivering Cobalt Strike on systems last summer in a similar search engine result poisoning campaign.
Gootloader has been associated with ransomware infections several times, with the malware coming back in 2020 through a high-profile collaboration with the REvil gang.
Poisoning Google search results
In a new report by Trend Micro, researchers explain that Gootloader's recent campaign uses SEO poisoning to inject its malicious websites into Google search results to target the Australian healthcare industry.
The campaign started in October 2022 and managed to rank highly in search results for medical-related keywords, such as "agreement", "hospital", "health", and "medical" combined with Australian city names.
SEO poisoning is a tactic that cybercriminals employ, creating many posts on many legitimate sites that include links to the threat actor's websites.
As search engine spiders index these legitimate sites and see the same URL repeatedly, they will add them to the search engine results for associated keywords. As a result, these search terms often rank quite highly in Google search results, as shown below.
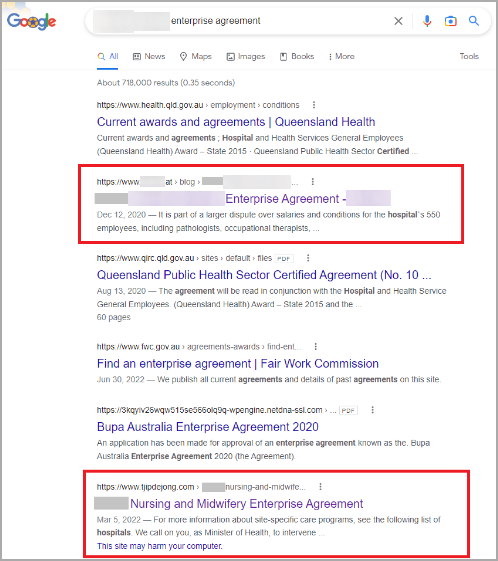
Malicious search results from current Gootloader campaign
Source: Trend Micro
The sites used by Gootkit are commonly hacked websites with JavaScript scripts injected to display fake Q&A forums to visitors coming from search engine results.
These fake Q&A forums will contain an "answer" to a question that links to associated searched-for resources, such as an agreement template or Word document. However, these links are malware that infects users' devices.
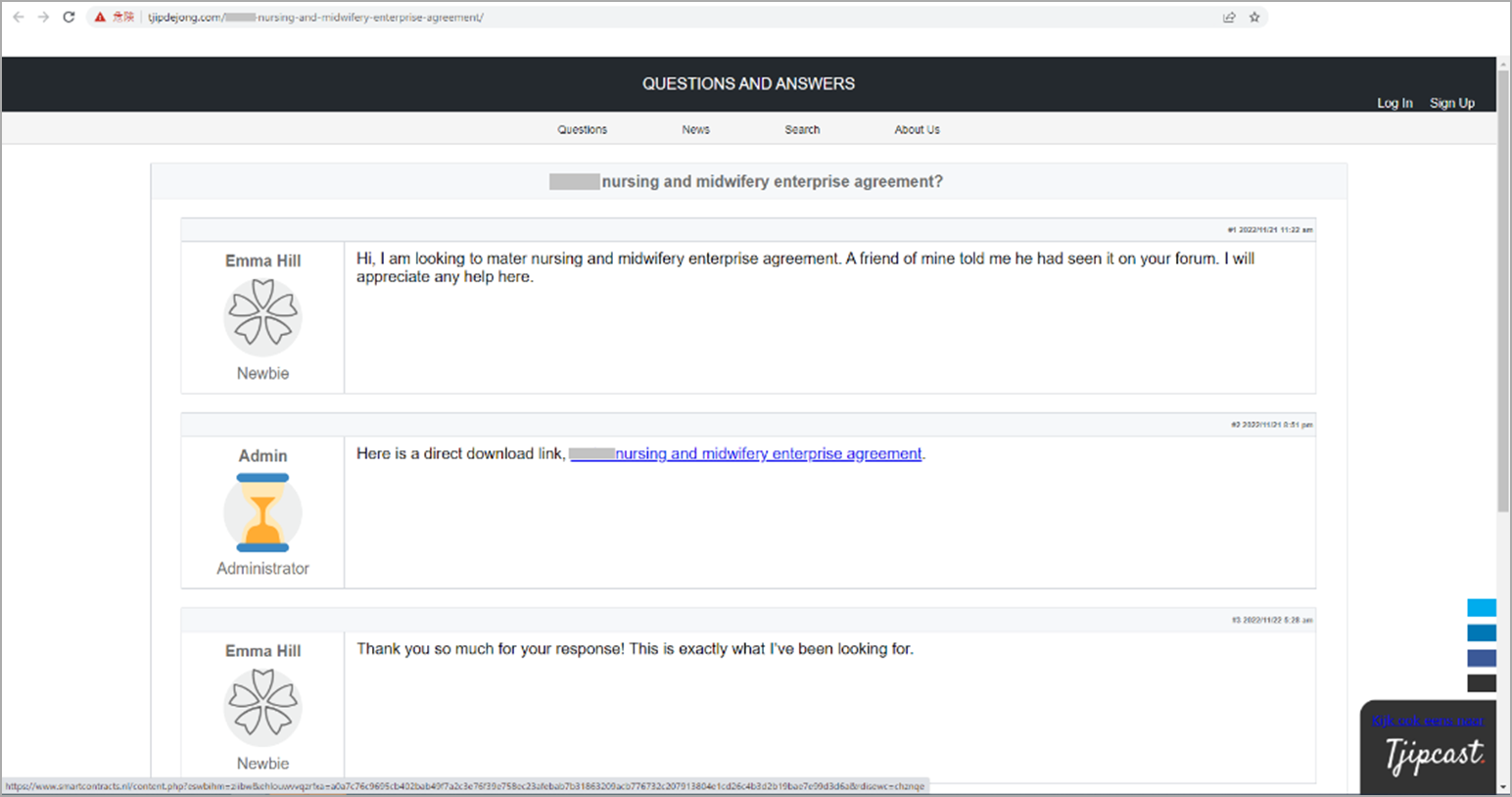
Fake Q&A forum on hacked website
Source: Trend Micro
A similar tactic has been employed extensively by malware loaders, like in this Batloader and Atera Agent campaign from February 2022, where the operators used Zoom, TeamViewer, and Visual Studio search terms to poison the results.
Planting Cobalt Strike beacons
In the latest Gootloader campaign, the threat actors use a direct download link for what is supposedly a healthcare-related agreement document template inside a ZIP archive.
This ZIP archive contains the Gootkit loader components in the form of a JS file that, when launched, drops a PowerShell script that is then executed to download further malware on the device.
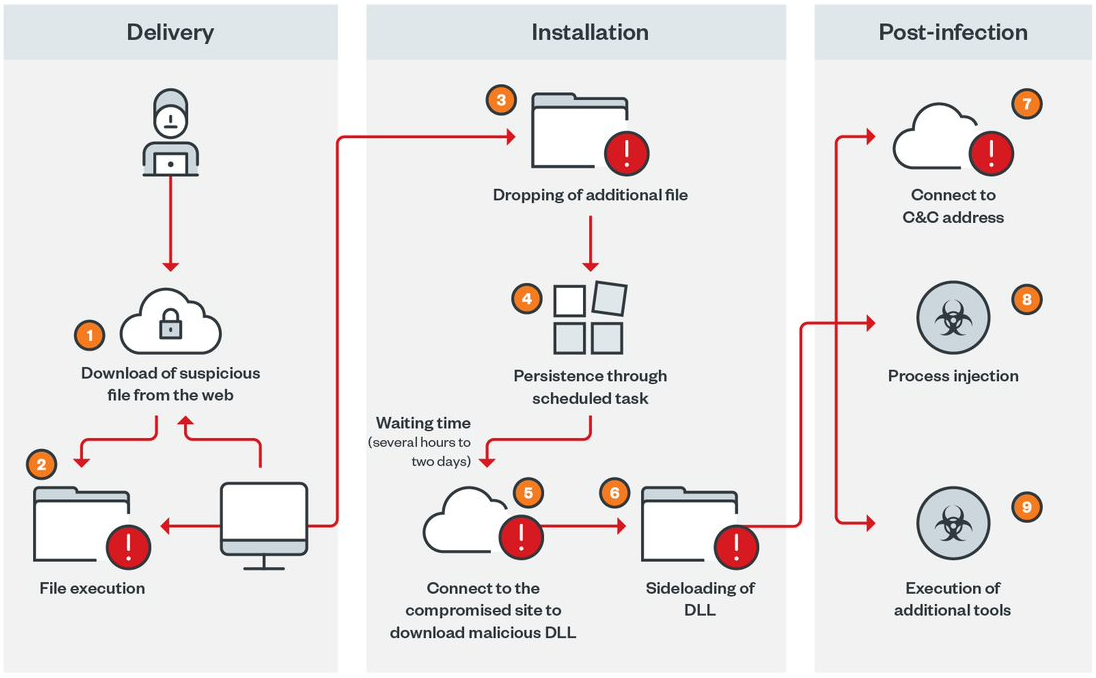
Gootloader's latest attack chain
Source: Trend Micro
At the second stage of the infection, the malware downloads 'msdtc.exe' and 'libvlc.dll' from the Gootloader command and control servers.
The executable is a legitimate and signed copy of the VLC media player masked to appear as the Microsoft Distributed Transaction Coordinator (MSDTC) service. The DLL is named after a legitimate VLC file required for the media player to start but is laced with a Cobalt Strike module.
When the VLC executable is launched, it uses a DLL-side loading attack to load the malicious DLL in the context of a trusted process.
This causes the VLC executable to spawn two processes, dllhost.exe and wabmig.exe, which host the Cobalt Strike beacon activities.
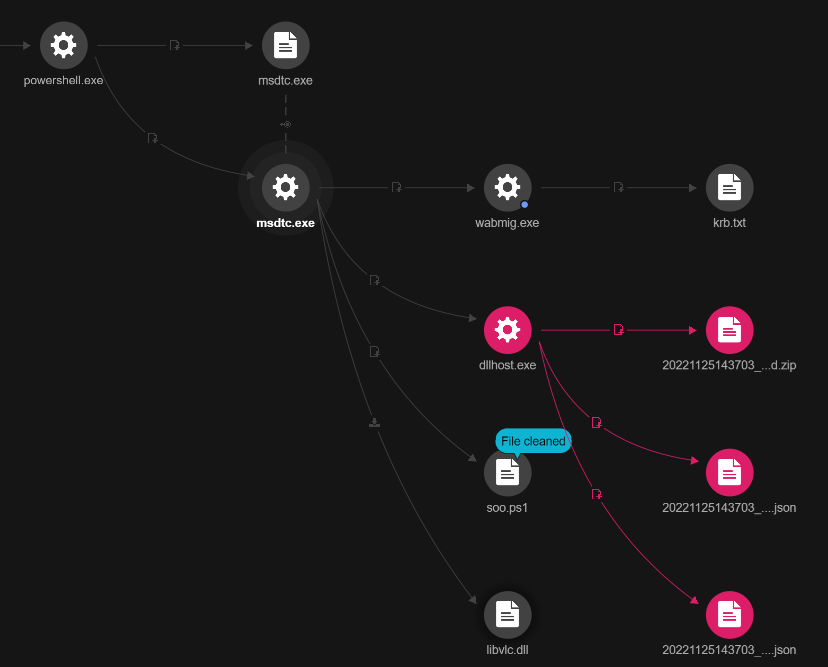
Processes spawned by the VLC executable
Source: Trend Micro
Using Cobalt Strike, the threat actors loaded 'PSHound.ps1' and 'soo.ps1' for network surveillance, connected to machines via ports 389, 445, and 3268, and dumped Kerberos hashes for several accounts on a text file ('krb.txt').
Cobalt Strike is usually a precursor to ransomware attacks, but in the case observed by Trend Micro, the researchers didn't have the opportunity to capture the final payload.
A DLL side-loading vulnerability in VLC Media Player was used in attacks by Chinese state-sponsored hackers. These vulnerabilities are believed to have led to the media player being banned in India.
Unfortunately, getting tricked by one of these search result poisoning campaigns can be hard to avoid.
Ultimately, the best way to avoid being infected is to only download files from trusted sources, enable file extensions so you can see the actual filename, and avoid clicking on files with dangerous extensions.
Furthermore, it is advised to upload any downloaded file to VirusTotal to check for malicious behavior before executing it.




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.