Google on Monday announced that it will pay security researchers to find exploits using vulnerabilities, previously remediated or otherwise, over the next three months as part of a new bug bounty program to improve the security of the Linux kernel.
To that end, the company is expected to issue rewards worth $31,337 for exploiting privilege escalation in a lab environment for each patched vulnerability, an amount that can climb up to $50,337 for working exploits that take advantage of zero-day flaws in the kernel and other undocumented attack techniques.
Specifically, the program aims to uncover attacks that could be launched against Kubernetes-based infrastructure to defeat process isolation barriers (via NSJail) and break out of the sandbox to leak secret information.
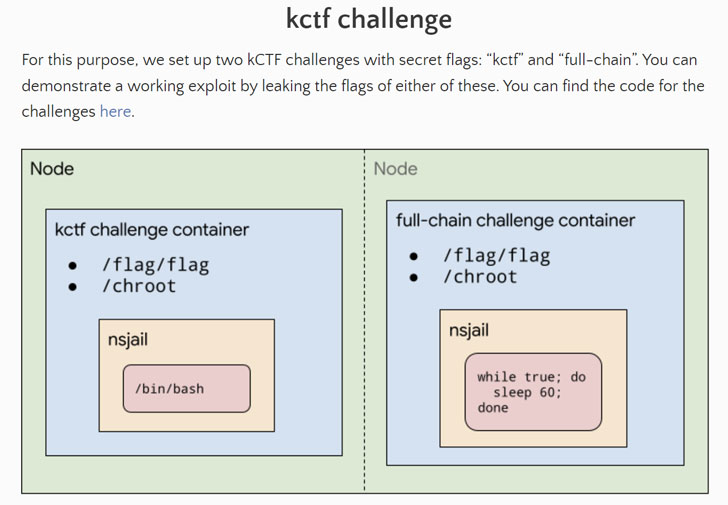
The program is expected to last until January 31, 2022.
"It is important to note, that the easiest exploitation primitives are not available in our lab environment due to the hardening done on Container-Optimized OS," Eduardo Vela of Google Bug Hunters Team said.
The rewards program also exists in conjunction with Android's VRP rewards, allowing researchers to demonstrate exploits that work on the mobile operating system, which could be eligible for up to $250,000 in bug bounties. More details about the contest can be found here.
- Karlston
-

 1
1



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.