A Google Cloud Armor customer was hit with a distributed denial-of-service (DDoS) attack over the HTTPS protocol that reached 46 million requests per second (RPS), making it the largest ever recorded of its kind.
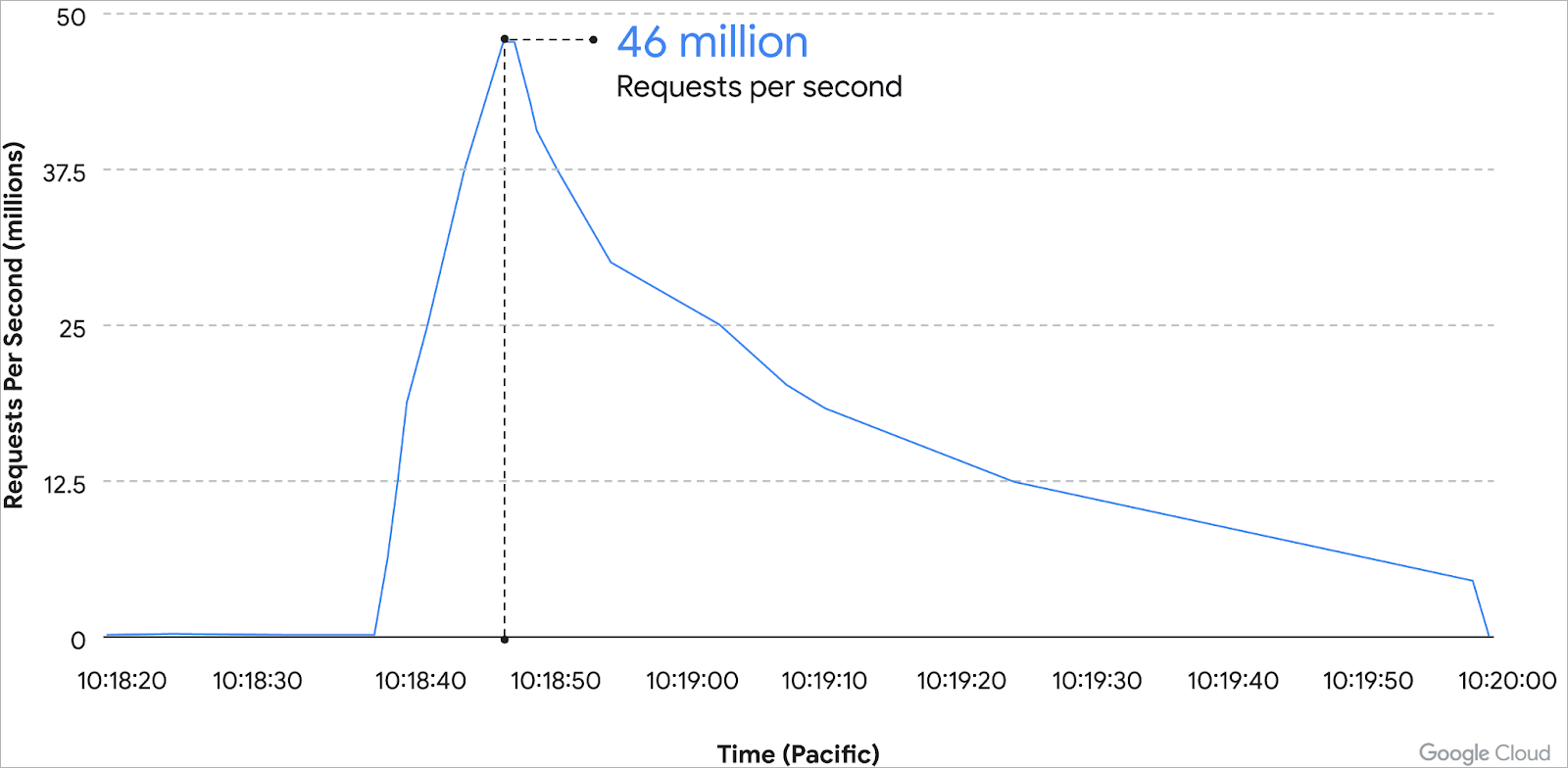
In just two minutes, the attack escalated from 100,000 RPS to a record-breaking 46 million RPS, almost 80% more than the previous record, an HTTPS DDoS of 26 million RPS that Cloudflare mitigated in June.
Assault lasted 69 minutes
The attack started on the morning of June 1, at 09:45 Pacific Time, and targeted the victim’s HTTP/S Load Balancer initially with just 10,000 RPS.
In eight minutes, the attack intensified to 100,000 RPS and Google’s Cloud Armor Protection kicked in by generating an alert and signatures based on certain data pulled from traffic analysis.
Two minutes later, the attack peaked at 46 million requests per second:
To put into perspective how massive the attack was at its peak, Google says that it was the equivalent of getting all the daily requests to Wikipedia in just 10 seconds.
Luckily, the customer had already deployed the recommended rule from Cloud Armor allowing operations to run normally. The assault ended 69 minutes after it started.
“Presumably the attacker likely determined they were not having the desired impact while incurring significant expenses to execute the attack,” reads a report from Google’s Emil Kiner (Senior Product Manager) and Satya Konduru (Technical Lead)
The malware behind the attack has yet to be determined but the geographic distribution of the services used points to a Mēris, a botnet responsible for DDoS attacks peaking at 17.2 million RPS and 21.8 million RPS, both record-breaking at their time.
Mēris is known for using unsecured proxies to send out bad traffic, in an attempt to hide the origin of the attack.
Google researchers say that the attack traffic came from just 5,256 IP addresses spread in 132 countries and leveraged encrypted requests (HTTPS), indicating that the devices sending the requests have rather strong computing resources.
“Although terminating the encryption was necessary to inspect the traffic and effectively mitigate the attack, the use of HTTP Pipelining required Google to complete relatively few TLS handshakes.”
Another characteristic of the attack is the use of Tor exit nodes to deliver the traffic. Although close to 22% or 1,169 of the sources channeled the requests through the Tor network, they accounted for just 3% of the attack traffic.
Despite this, Google researchers believe that Tor exit nodes could be used to deliver “a significant amount of unwelcome traffic to web applications and services.”
Starting last year, an era of record-breaking volumetric DDoS attacks started with a few botnets leveraging a small number of powerful devices to hit various targets.
In September 2021, Mēris botnet hammered Russian internet giant Yandex with an attack peaking at 21.8 million requests per second. Previously, the same botnet pushed 17.2 million RPS against a Cloudflare customer.
Last November, Microsoft's Azure DDoS protection platform mitigated a massive 3.47 terabits per second attack with a packet rate of 340 million packets per second (pps) for a custmer in Asia.
Another Cloudflare customer was hit with DDoS reaching 26 million RPS.
- aum
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.