Searching for 'GIMP' on Google as recently as last week would show visitors an ad for 'GIMP.org,' the official website of the well known graphics editor, GNU Image Manipulation Program.
This ad would appear to be legitimate as it'd state 'GIMP.org' as the destination domain. But clicking on it drove visitors to a lookalike phishing website that provided them with a 700 MB executable disguised as GIMP which, in reality, was malware.
'GIMP' malvertising abuses Google ads
Up until last week, googling for 'GIMP' would bring up a Google ad that'd appear to take you to the open source graphics editor's official website 'GIMP.org.'
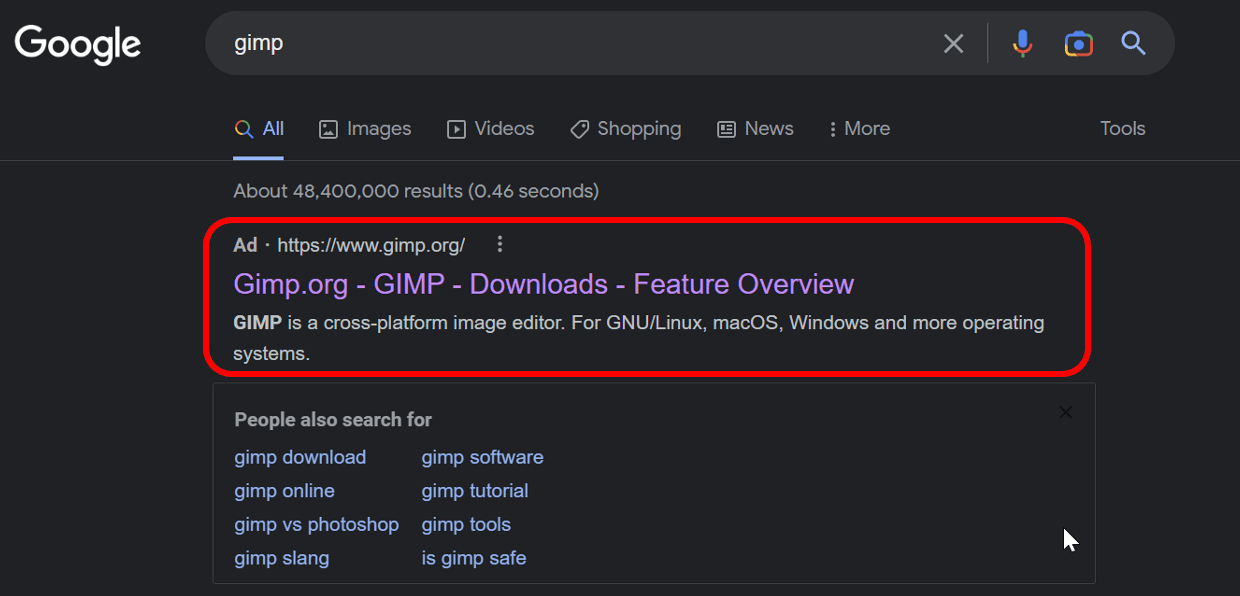
Problematic Google ad leading visitors to GIMP phishing site
But instead this malvertising campaign drove visitors to a lookalike, phishing page delivering a malicious 'Setup.exe' that appeared to be the GIMP utility for Windows.

Fake GIMP site 'gilimp.org' (BleepingComputer)
Reddit user ZachIngram04 earlier shared the development stating that the ad previously took users to a Dropbox URL to serve malware, but was soon "replaced with an even more malicious one" which employed a fake replica website 'gilimp.org' to serve malware.
BleepingCompuer observed another domain 'gimp.monster' related to this campaign.
To pass off the trojanized executable as GIMP in a believable manner to the user, the threat actor artificially inflated the malware, that is otherwise under 5 MB in size, to 700 MB by a simple technique known as binary padding.
Google ads 'display URL' vs. 'landing URL'
All of this has still left users puzzled as to why the Google ad showed 'GIMP.org' as the destination domain in the first place, when the ad actually took users to the fake 'gilimp.org' site.
Redditor RawPacket surmised if this was result of the threat actor creating a Google ad using IDN homograph technique that'd make Cyrillic 'gіmp.org', which is reality is http://xn--gmp-jhd.org/, appear akin to the Latin 'gimp.org.'
But, given the use of phishing domains 'gilimp.org' and 'gimp.monster' used in this campaign, the scenario seems unlikely.
Google lets publishers create ads with two different URLs: a display URL to be shown in the ad, and a landing URL where the user will actually be taken to.
The two need not be the same, but there are strict policies around what is permitted when it comes to display URLs, and these need to use the same domain as the landing URL.
"Advertisers use a landing page URL to send people to a specific area of their website," explains Google.
"Your ads' URLs should give customers a clear idea of what page they'll arrive at when they click on an ad. For this reason, Google's policy is that both display and landing page URLs should be within the same website. This means that the display URL in your ad needs to match the domain that visitors land on when they click on your ad."
It still isn't clear if this instance was a slip up caused by a potential bug in Google Ad Manager that allowed malvertising. BleepingComputer has approached Google for comment.
Part of ongoing VIDAR infostealer campaigns
BleepingComputer was able to obtain a copy of the malicious executable and we can confirm it is an infostealing trojan called VIDAR.
VIDAR infostealers work by connecting to their command-and-control (C2) server and awaiting further instructions.
But, before accomplishing that, the malicious 'Setup.exe' fetches a 'Htcnwiij.bmp' file from a Russia-based URL:
The file above appears to be a Bitmap image in a web browser but is instead a DLL packed as hex instructions for the malware to execute.
Further, BleepingComputer observed 'Setup.exe' contacting its C2 server (95.216.181.10), to retrieve C2 configuration, before downloading stage 2 payload.

Stage 2 of VIDAR typically comprises downloading a ZIP archive with additional DLL dependencies and modules that'd aid in its credential theft and info-stealing activities:
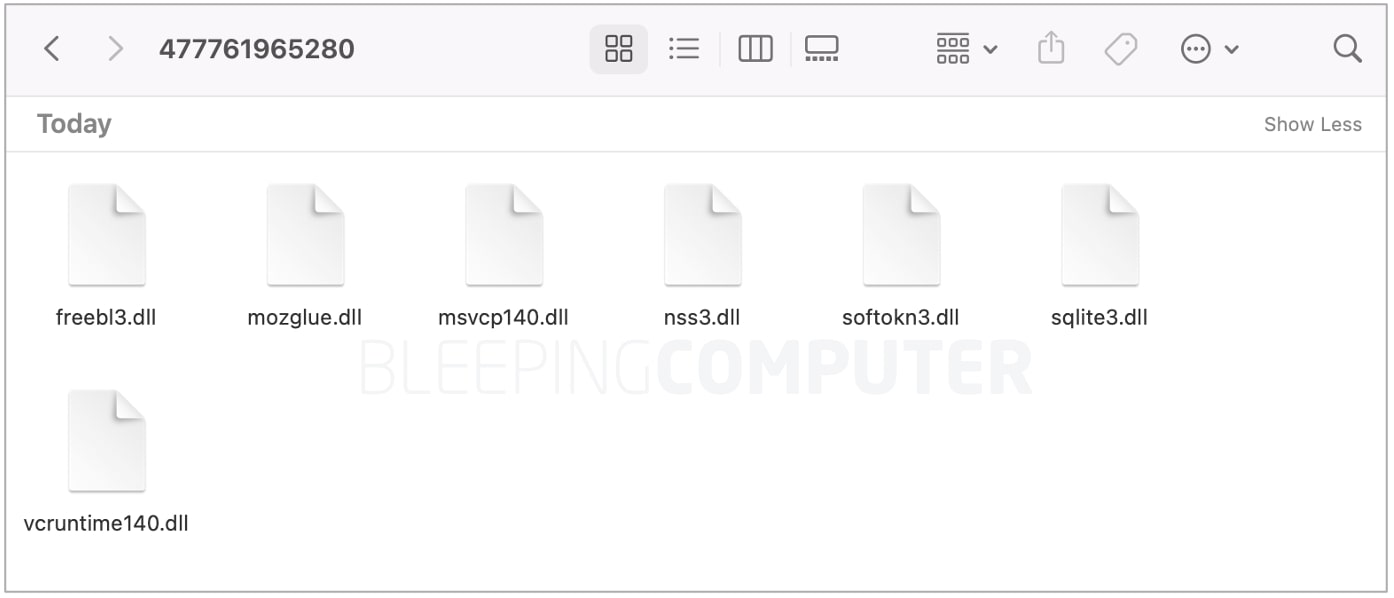
The data that Vidar variants attempt to steal from infected machines includes the following:
- All popular browser information such as passwords, cookies, history, and credit cards details.
- Cryptocurrency wallets.
- Files according to regex strings given by the TA.
- Telegram credentials for Windows versions.
- File transfer application information (WINSCP, FTP, FileZilla)
- Mailing application information.
Security researcher and bug bounty hunter 0x0Luke further analyzed the malvertising campaign targeting GIMP users and described what all 'Setup.exe' was stealing.
Previously, domain typosquatting campaigns employing VIDAR have targeted users of at least 27 software products including Notepad++, Microsoft Visual Studio, and Brave browser.
In another instance, threat actors employing VIDAR were caught abusing Mastodon, an open source social networking platform to silently retrieve the malware's C2 configuration.




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.