IT and software consultancy firm Globant has confirmed that they were breached by the Lapsus$ data extortion group, where data consisting of administrator credentials and source code was leaked by the threat actors.
As part of the leak, the hacking group released a 70GB archive of data stolen from Globant, describing it as “some customers source code.”
Source code and private keys
Globant is an IT and software development firm with over 16,000 employees worldwide and $1.2 billion in revenue for 2021.
Founded in Buenos Aires, Argentina, Globant is currently headquartered in Luxembourg and boasts a well-known list of customers, including Metropolitan Police, SmileDirectClub, Autodesk, Electronic Arts, Santander, Interbank, Royal Carribbean, and many more.
Following the leak from Lapsus$, Globant issued a press release confirming that some of the company source code has been exposed to an unauthorized party.
“We have recently detected that a limited section of our company's code repository has been subject to unauthorized access” - Globant
Among the data published by Lapsus$, there is a screenshot the group claims to be of an archived directory from Globant, containing folder names that appear to be company customers.
Some of the source code folders listed in the screenshot include, Abbott, apple-health-app, C-span, Fortune, Facebook, DHL, and Arcserve.
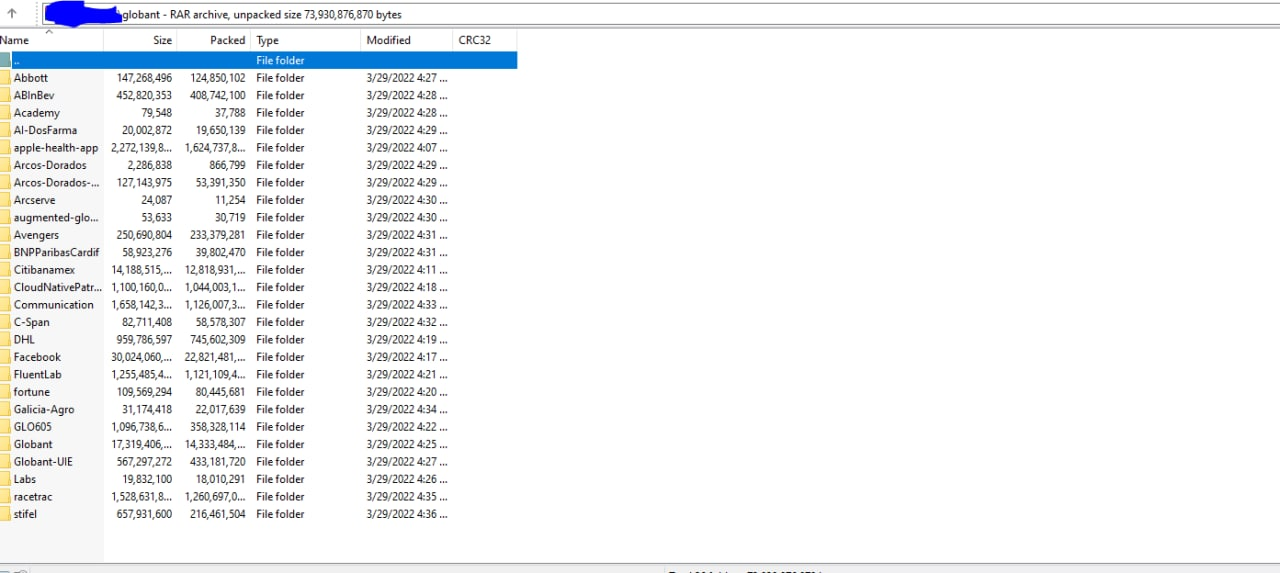
The metadata for the entries shows that the folders have been modified on March 29, which could indicate when the data was stolen.
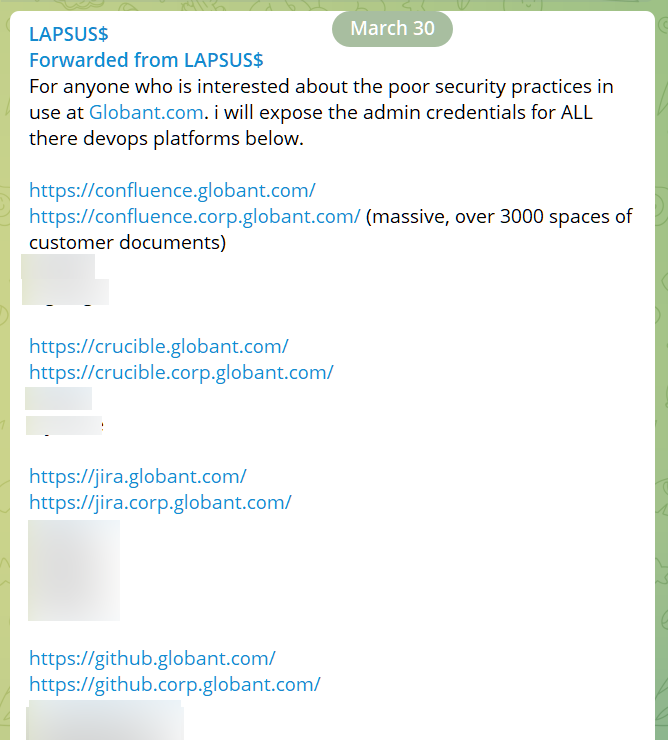
In a follow-up post, Lapsus$ published a set of credentials for what they say give administrator access to various platforms used by Globant for developing, reviewing, and collaborating on customer code (Jira, Confluence, GitHub, Crucible).
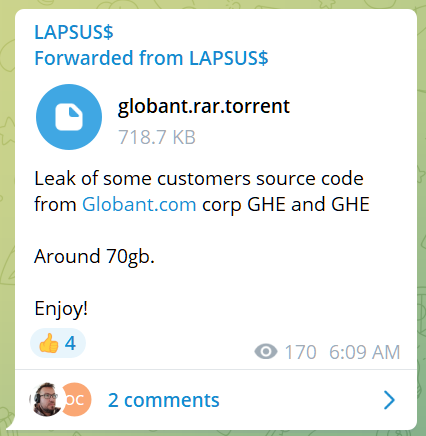
A third post from the gang today shared a torrent file for about 70GB of data stolen from Globant. The company says that the intruder on its systems accessed “certain source code and project-related documentation for a very limited number of clients.”
The damage appears to be significant.
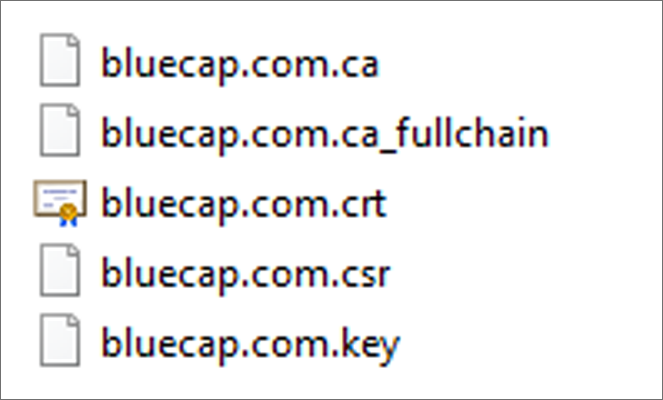
According to threat intelligence company SOS Intelligence, the leaked data contains customer information as well as a code repositories with a large number of private keys (full chain, web server SSL certificates, Globant server, API keys).
One of the repositories is for the Bluecap app for consultancy in the financial sector, that Globant acquired in late 2020.
The cache that Lapsus$ leaked also includes a little over 150 SQL database files for various customer applications, SOS Intelligence says.
"In terms of legitimacy, going just by volume alone it's hard to fabricate that amount of data - however samples of the data have been cross referenced with live systems and other methods that show the leak is legitimate and very significant as far as Globant and Globant's impacted customers are concerned" - SOS Intelligence
Globant said today that its investigation into the incident did not reveal any evidence that the hackers compromised other parts of its infrastructure system.
Lapsus$ on LE radar
The Lapsus$ data extortion group has been constantly making the news due to their attacks on big technological companies, like Microsoft, Nvidia, Samsung, Okta, Ubisoft, many of them resulting in big data leaks.
Despite the big names on their victim list, Lapsus$ is believed to be formed mainly by teenagers exercising their hacking skills driven mainly by making a name on the hacking scene, not by financial motivation.
The group has been on the radar of law enforcement for a while and some individuals, all teens believed to be connected to Lapsus$, have been arrested in the U.K.
The FBI is also investigating the activities of the group and has asked the public for any information leading to identifying Lapsus$ members involved in the compromise of computer networks from U.S.-based companies.
However, it is unclear how many active members are in the group and what roles they play.
It is believed that Lapsus$ has affiliates all over the world, as their Telegram chats seem to suggest that some of them speak English, Russian, Turkish, German, and Portuguese.
Globant confirms hack after Lapsus$ leaks 70GB of stolen data
- aum
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.