Cloud-based repository hosting service GitHub has addressed a high-severity security flaw that could have been exploited to create malicious repositories and mount supply chain attacks.
The RepoJacking technique, disclosed by Checkmarx, entails a bypass of a protection mechanism called popular repository namespace retirement, which aims to prevent developers from pulling unsafe repositories with the same name.
The issue was addressed by the Microsoft-owned subsidiary on September 19, 2022 following responsible disclosure.
RepoJacking occurs when a creator of a repository opts to change the username, potentially enabling a threat actor to claim the old username and publish a rogue repository with the same name in an attempt to trick users into downloading them.
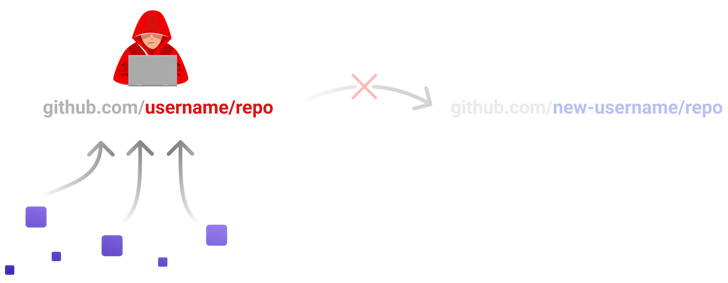
While Microsoft's countermeasure "retire[s] the namespace of any open source project that had more than 100 clones in the week leading up to the owner's account being renamed or deleted," Checkmarx found that this can be circumvented through the "repository transfer" feature.
The way this works is as follows -
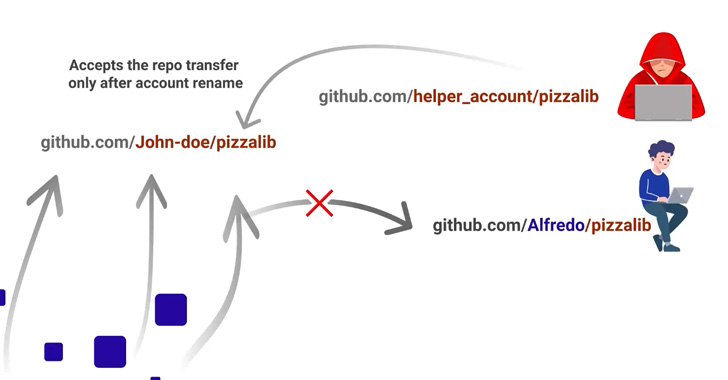
- A threat actor creates a repository with the same name as the retired repository (say, "repo") owned by a user named "victim" but under a different username (say, "helper")
- "helper" transfers ownership of "repo" to a second account with username "attacker"
- "attacker" renames the account's username to "victim"
- The namespace "victim/repo" is now under the adversary's control
In other words, the attack hinges on the quirk that GitHub only considers as retired the namespace, i.e., the combination of username and repository name, permitting a bad actor to reuse the repository name in conjunction with an arbitrary username.
- alf9872000 and Karlston
-

 2
2



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.