Ukraine's defense ministry and two banks were knocked offline on Tuesday by a flood of malicious traffic designed to prevent people from visiting the sites, Ukraine's information security center said.
The distributed denial-of-service attacks targeted the websites for Ukraine's defense ministry, the Armed Forces of Ukraine, and two banks, Privatbank and Oschadbank, the country's State Service for Special Communication and Information Protection reported. At the time this post was being reported, the Defense Ministry site remained completely unreachable. Meanwhile, only the homepage for PrivatBank was available, and it was defaced. Oschadbank's site provided only limited access.

The malicious data floods were also reported by the Ukrainian cyberpolice, but at the time this post was being reported, attempts to visit most of the department's website were unsuccessful. The homepage said: "We apologize for the inconvenience. The site is under maintenance."
On Twitter, department personnel also said they had identified individuals who were sending texts reporting fraudulent ATM failures. Ukraine's Security Service website was also not loading.
No pizza for you
Campaigns that use DDoSes (short for distributed denial-of-service) deliver torrents of junk traffic that are intended to overwhelm targets so they are unable to deliver services. DDoSes can be difficult to stop because they are delivered by large numbers of devices distributed in a wide geographic region.
They're analogous to flooding a pizza parlor with so many calls that it's unable to accept orders from customers.
While DDoSes have the capacity to paralyze websites or even huge swaths of the Internet, the disruptions they cause are temporary and usually last only as long as the responsible party continues to deliver the torrent or until a DDoS mitigation service filters out the junk traffic.
Network observability company Kentik has been tracking Internet traffic flowing through Ukraine. Graphs showed the DDoSes starting on Tuesday, when the volume of traffic to various targets suddenly spiked by orders of magnitude. AS28907, the autonomous system that hosts the Ukrainian Army, was hit by three waves, as the following two images show:
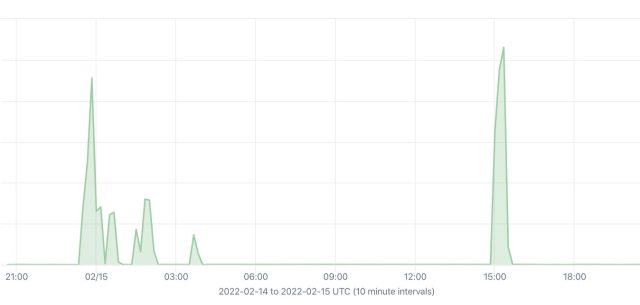
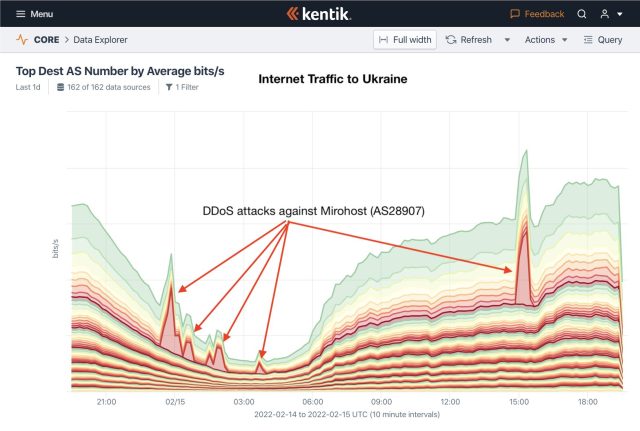
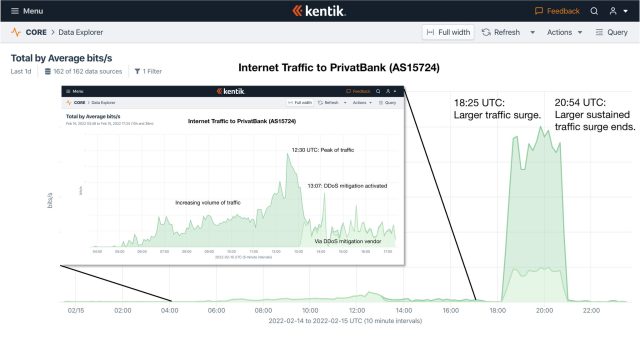
AS60173 AND AS15742, which host Oschadbank and PrivatBank respectively, saw similar floods:
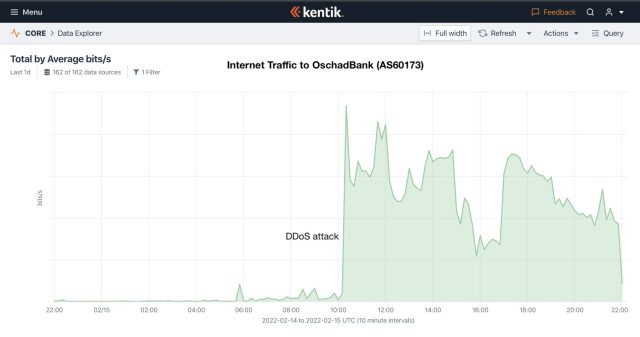
The DDoSes arrived as Russia has amassed more than 100,000 soldiers at its border with Ukraine. There's no evidence the Russian government or citizens are behind the cyber actions, but a statement from Ukraine's Center for Strategic Communications and Information Security posted on Facebook hinted who it suspected.
"It is not ruled out that the aggressor used tactics of little dirty tricks because its aggressive plans are not working out on a large scale," the center officials wrote in a rough translation.



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)

Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.