The Federal Bureau of Investigation (FBI) said today that the notorious Hive ransomware gang has successfully extorted roughly $100 million from over a thousand companies since June 2021.
To add insult to injury, the FBI says that the Hive gang will deploy additional ransomware payloads on the networks of victims who refuse to pay the ransom.
"As of November 2022, Hive ransomware actors have victimized over 1,300 companies worldwide, receiving approximately US$100 million in ransom payments, according to FBI information," the FBI revealed.
"Hive actors have been known to reinfect—with either Hive ransomware or another ransomware variant—the networks of victim organizations who have restored their network without making a ransom payment."
The list of victims includes organizations from a wide range of industries and critical infrastructure sectors such as government facilities, communications, and information technology, with a focus on Healthcare and Public Health (HPH) entities.
This was revealed in a joint advisory published today with the Cybersecurity and Infrastructure Security Agency (CISA) and the Department of Health and Human Services (HHS).
Today's advisory was issued to share Hive indicators of compromise (IOCs) and tactics, techniques, and procedures (TTPs) discovered by the FBI while investigating Hive ransomware attacks.
The end goal is to help defenders detect malicious activity associated with Hive affiliates and reduce or eliminate the impact of such incidents.
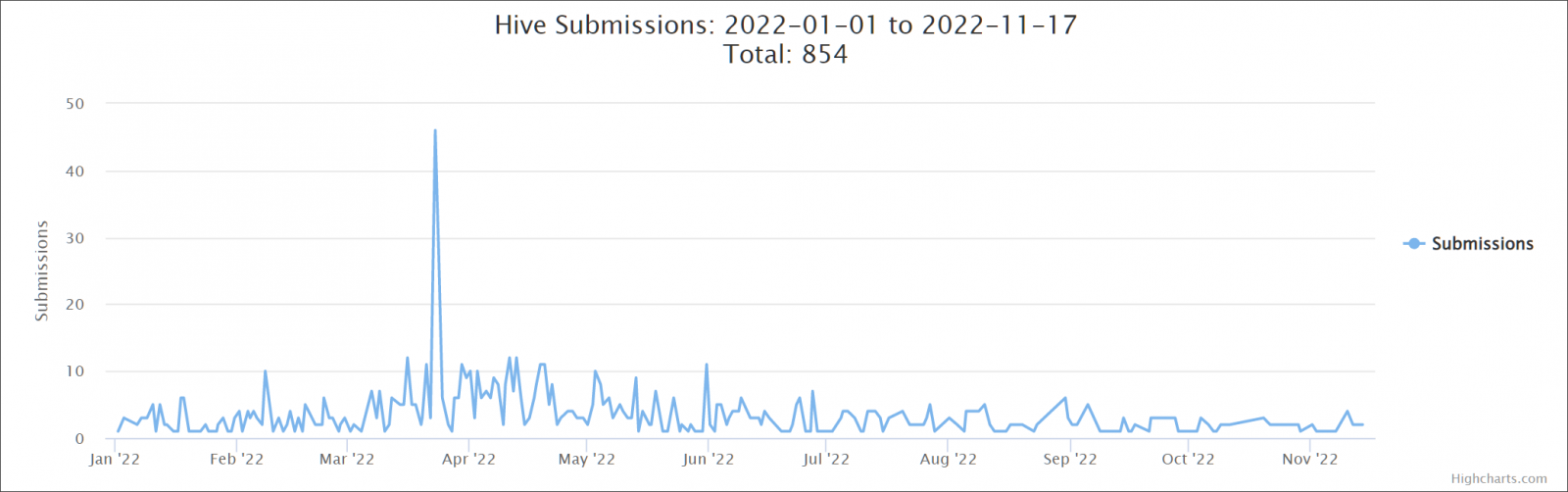
While submissions to the ID Ransomware platform don't include all Hive ransomware attacks, victims have submitted more than 850 samples since the start of the year, many of them pushed following a huge spike of activity between late March and mid-April.
Request for incident reports
While the three federal agencies behind the advisory do not encourage paying the ransoms as it will most likely encourage other threat actors to join the ransomware onslaught, victims are urged to report Hive attacks to their local FBI field office or to CISA at [email protected] regardless of whether they pay the ransom or not.
This will help law enforcement collect critical information needed to keep track of the ransomware operation's activity, prevent additional attacks, or hold the attackers accountable for their actions.
The FBI also released additional indicators of compromise and technical details associated with Hive ransomware attacks in August 2021.
Hive is a Ransomware-as-a-Service (RaaS) operation active since at least June 2021, with some of its members known to have worked for both Hive and the Conti cybercrime gang simultaneously for at least six months, starting in November 2021.
"We have identified extended evidence of HIVE actively using both the initial attack accesses provided by Conti and the services of Conti's pen-testers," Advanced Intel's Head Of Research Yelisey Boguslavskiy told BleepingComputer in May 2022.
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.