Fake extortionists are piggybacking on data breaches and ransomware incidents, threatening U.S. companies with publishing or selling allegedly stolen data unless they get paid.
Sometimes the actors add the menace of a distributed denial-of-service (DDoS) attack if the message recipient does not comply with the instructions in the message.
Bad actors
The attackers behind this activity use the name Midnight and started targeting companies in the U.S. since at least March 16.
They have also impersonated some ransomware and data extortion gangs in emails and claimed to be the authors of the intrusion, stealing hundreds of gigabytes of important data.
In one email to the employee of a holding company in the industry of petroleum additives, the threat actor claimed to be the Silent Ransom Group (SRG) - a splinter of the Conti syndicate focused on stealing data and extorting the victim, also known as Luna Moth.
The same message, however, used in the subject line the name of another threat actor, the Surtr ransomware group, first seen to encrypt company networks in December 2021.

Midnight Group impersonating Surtr ransomware and Silent Ransom
source: BleepingComputer
BleepingComputer found another email from Midnight Group, professing that they were the authors of the data breach and that they stole 600GB of “essential data” from the servers.
The messages were sent to the address of a senior financial planner that had left the target company more than half a year before.
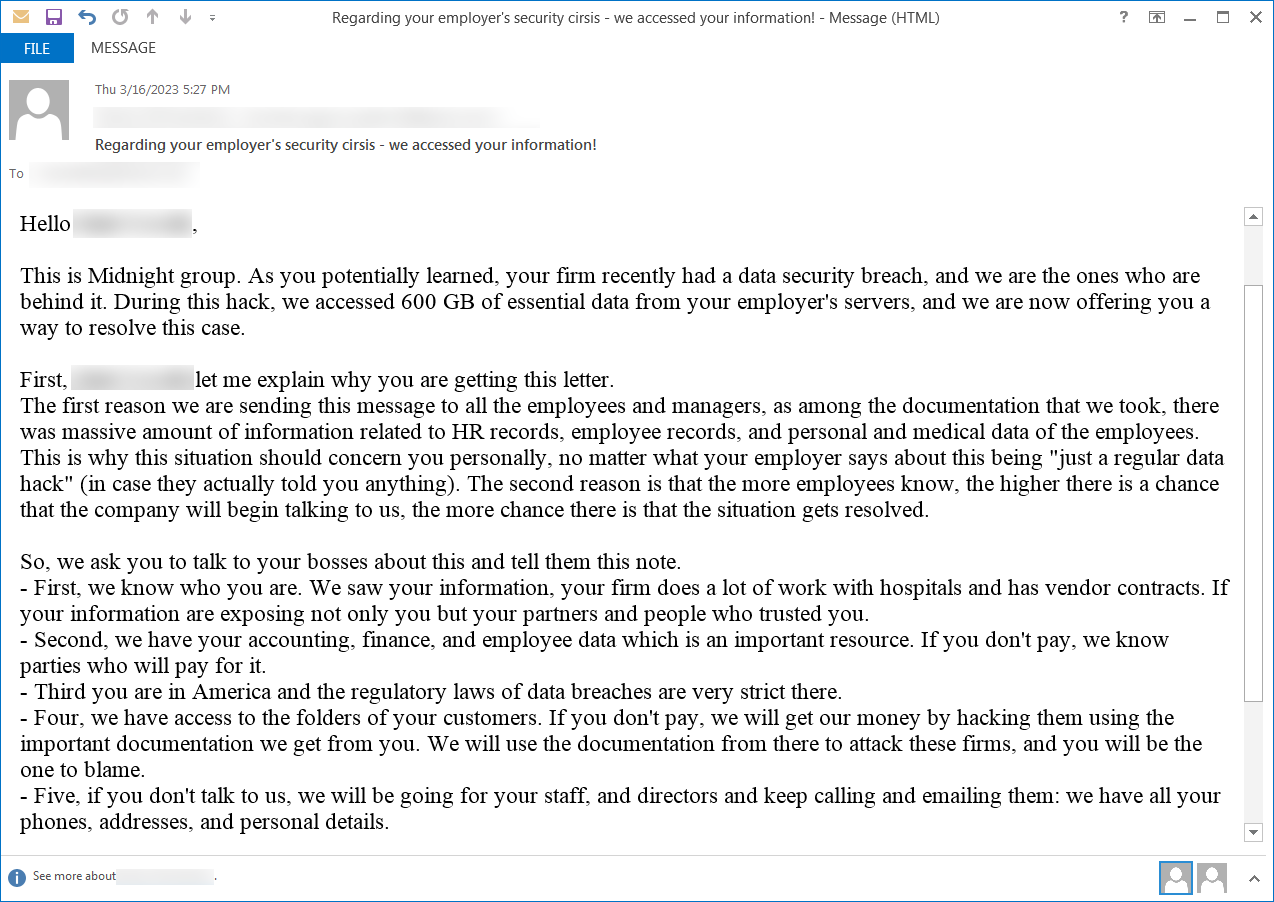
Midnight Group claiming to have stolen company data in cyberattack
source: BleepingComputer
Pending DDoS threat
A report in late March from the managed detection and response division at the Kroll corporate investigation and risk consulting firm notes that some senders of similar emails also threatened with DDoS attacks.
Kroll investigators say that starting March 23 organizations started filing an increased number of reports for emails received under the Silent Ransom Group name.
It’s “a new wave of fake extorsion attempts,” Kroll responders say in the report, adding that the authors use the names of better-known cybercriminals in an attempt to intimidate and give legitimacy to the threat.
“This method is cheap and easily conducted by low-skilled attackers. Much like 419 wirefraud scams, the scam relies on social engineering to extort victims by placing pressure on the victim to pay before a deadline. We expect this trend to continue indefinitely due to its cost effectiveness and ability to continue to generate revenue for cybercriminals” - Kroll
Kroll has seen such incidents since 2021, although such activity started in early November 2019, when non-paying victims also experienced DDoS attacks.
Nevertheless, the attacks were low-level DDoS and came with the threat of larger ones unless the extortionists got paid.
Such incidents echo the activity of an extortion group that in 2017 sent DDoS threats to thousands of companies under the names of infamous hacker groups at the time (e.g. New World Hackers, Lizard Squad, LulzSec, Fancy Bear, and Anonymous).
Targeting ransomware attack victims
Another report from incident response company Arete confirms Kroll’s observations about Midnight Group’s fraudulent emails impersonating Surtr and SRG and the larger number of messages delivered in the weeks before March 24.
Based on their visibility, though, the incident responders observed that Midnight targeted organizations that had previously been victims of a ransomware attack.
According to Arete’s analysts, among the initial attackers are QuantumLocker (currently rebranded as DagonLocker), Black Basta, and Luna Moth.
Arete says that at least 15 of their current and previous clients received fake threats from the Midnight Group, which supported their data theft claims with vague details.
It is unclear how victims are selected but one possibility is from publicly available sources, such as the initial attacker’s data leak site, social media, news reports, or company disclosures.
However, Arete notes that the fake attacker identified some ransomware victims even when the info was not publicly available, possibly indicating collaboration with the initial intruders.
Ransomware actors often sell the data they steal from victims even when they get paid. If Midnight Group has access to the markets and forums where this data is traded or sold they could learn about ransomware victims that have yet to disclose the cyberattack.
Empty threats since 2019
Midnight Group’s extortion scam is not new. The tactic has been observed in 2019 by ransomware incident response company Coveware who calls it Phantom Incident Extortion.
Coveware explains that the threat actor tries to give credibility to the threat by using data that is unique to the recipient target, adds the pressure of a costly outcome, and demands payment that is far less than the damage of public exposure.
All these three components are the mainstays of a phantom incident extortion (PIE) and a clear indication of an empty threat.
Coveware initially provided four examples of PIE scams and updated the report only recently with a sample email from the Midnight Group.
All three companies assess that Midnight Group’s threats are part of a fraud campaign. Arete’s attempt to engage with the actor resulted in no response or evidence of stolen data from the actor.
The recommendation is to carefully analyze such emails to recognize the components of a phantom incident extortion message and dismiss them as an empty threat.
- Karlston and aum
-

 2
2




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.