Windows gamers and power users are being targeted by fake MSI Afterburner download portals to infect users with cryptocurrency miners and the RedLine information-stealing malware.
The MSI Afterburner is a GPU utility that allows you to configure overclocking, create fan profiles, perform video capturing, and monitor your installed graphics cards' temperature and CPU utilization.
While created by MSI, the utility can be used by users of almost all graphics cards, leading to its use by millions of gamers worldwide who tweak settings to improve game performance, make their GPUs more silent, and achieve lower temperatures.
However, the tool's popularity has also made it a good target for threat actors, who are looking to target Windows users with powerful GPUs that can be hijacked for cryptocurrency mining.
Impersonating MSI Afterburner
According to a new report by Cyble, over 50 websites impersonating the official MSI Afterburner site have appeared online in the past three months, pushing XMR (Monero) miners along with information-stealing malware.
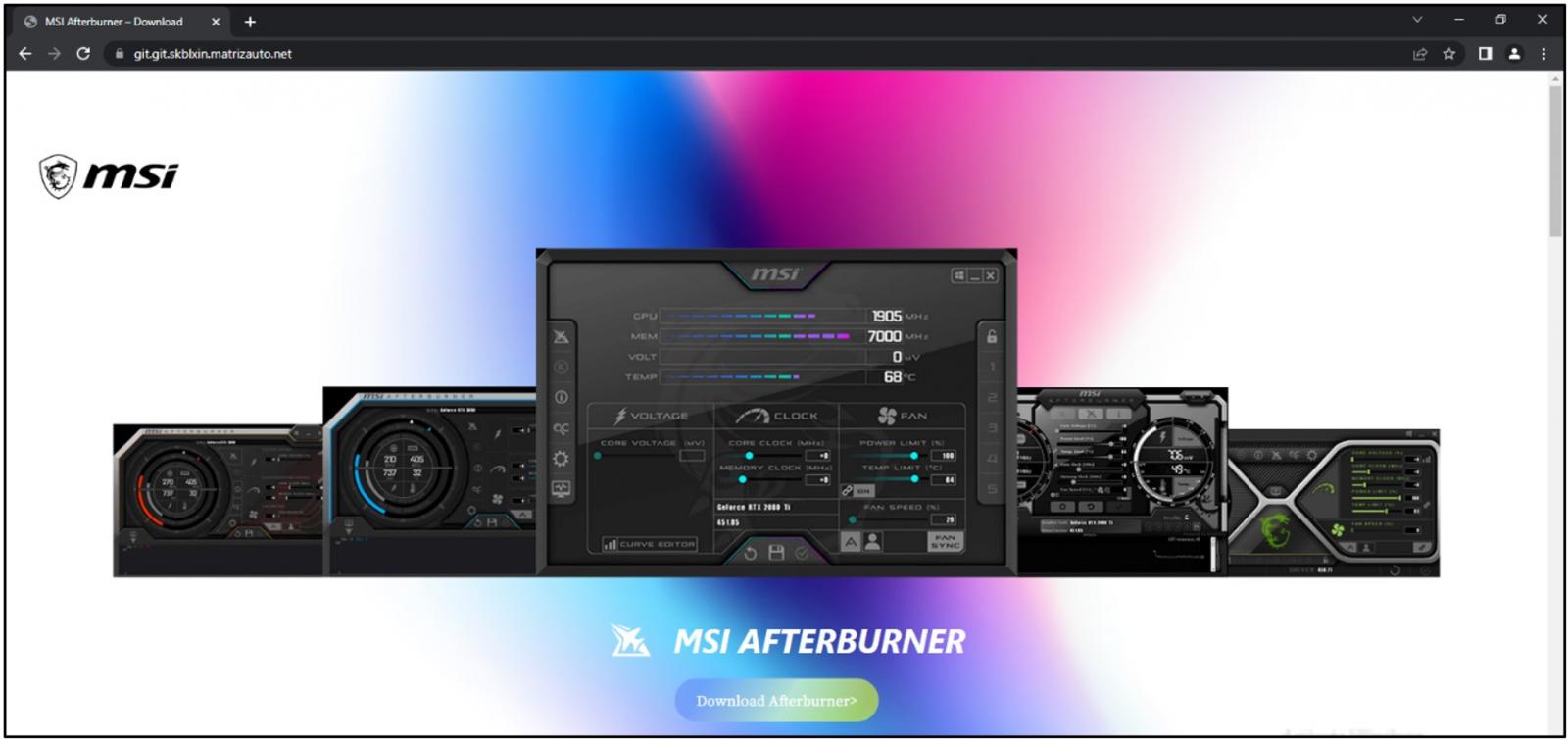
Malicious website pushing laced MSI Afterburner (Cyble)
The campaign used domains that could trick users into thinking they were visiting the legitimate MSI website and which are easier to promote using BlackSEO. Some of the domains spotted by Cyble are listed below:
- msi-afterburner--download.site
- msi-afterburner-download.site
- msi-afterburner-download.tech
- msi-afterburner-download.online
- msi-afterburner-download.store
- msi-afterburner-download.ru
- msi-afterburner.download
- mslafterburners.com
- msi-afterburnerr.com
In other cases, the domains did not resemble the MSI brand and were likely promoted via direct messages, forums, and social media posts. Examples include:
- git[.]git[.]skblxin[.]matrizauto[.]net
- git[.]git[.]git[.]skblxin[.]matrizauto[.]net
- git[.]git[.]git[.]git[.]skblxin[.]matrizauto[.]net
- git[.]git[.]git[.]git[.]git[.]skblxin[.]matrizauto[.]net
Stealthy mining while stealing your passwords
When the fake MSI Afterburner setup file (MSIAfterburnerSetup.msi) is executed, the legitimate Afterburner program will be installed. However, the installer will also quietly drop and run the RedLine information-stealing malware and an XMR miner in the compromised device.
The miner is installed through a 64-bit Python executable named 'browser_assistant.exe' in the local Program Files directory, which injects a shell into the process created by the installer.
This shellcode retrieves the XMR miner from a GitHub repository and injects it directly into memory in the explorer.exe process. Since the miner never touches the disk, the chances of being detected by security products are minimized.
The miner connects to its mining pool using a hardcoded username and password and then collects and exfiltrates basic system data to the threat actors.
One of the arguments the XMR miner uses is 'CPU max threads' set to 20, topping most modern CPU thread count, so it's set to capture all available power.
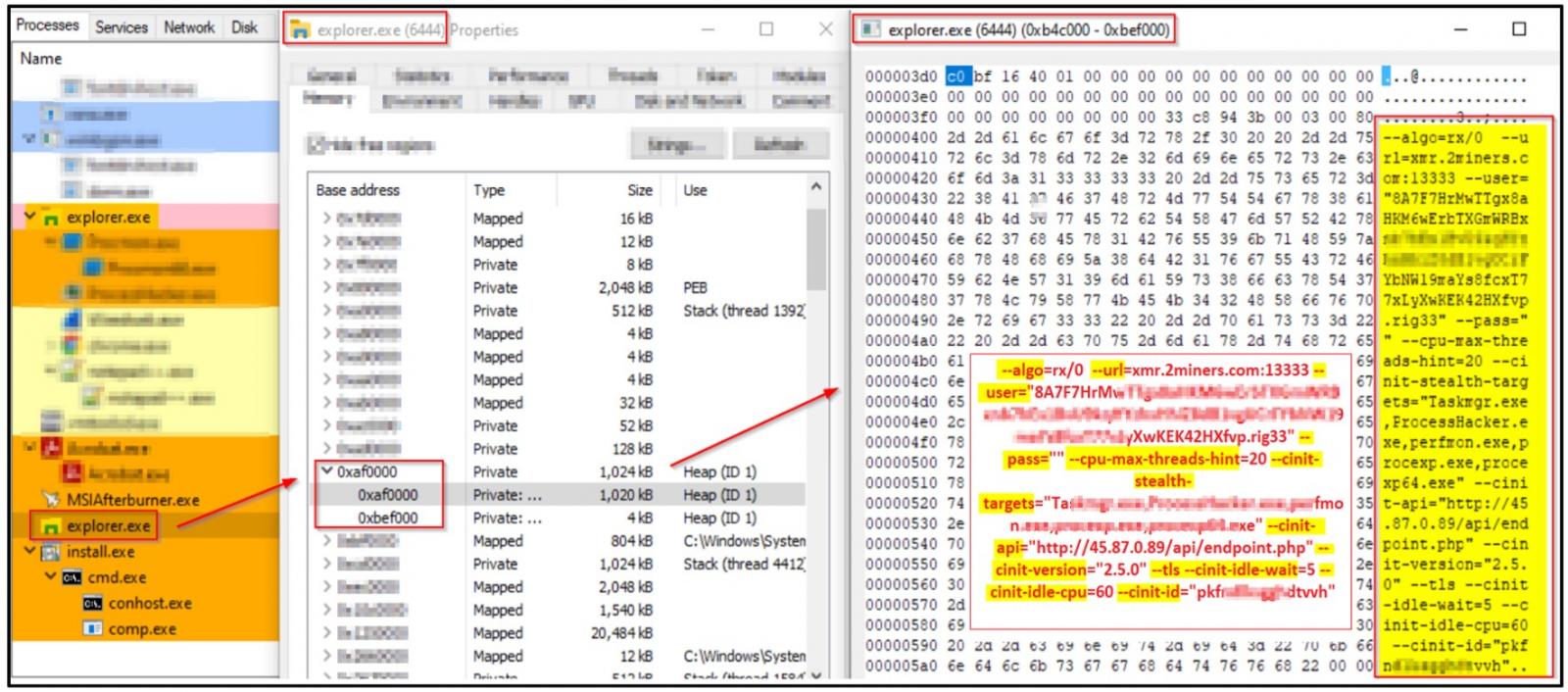
XMRminer argument details (Cyble)
The miner is set to mine only after 60 minutes since the CPU has entered idling, meaning that the infected computer is not running any resource-intensive tasks and is most likely left unattended.
Also, it uses the "-cinit-stealth-targets" argument, which is an option to pause mining activity and clear GPU memory when specific programs listed under "stealth targets" are launched.
These could be process monitors, antivirus tools, hardware resource viewers, and other tools that help the victim spot the malicious process.
In this case, the Windows applications from which the miner attempts to hide are Taskmgr.exe, ProcessHacker.exe, perfmon.exe, procexp.exe, and procexp64.exe.
While the miner is quietly hijacking your computer's resources to mine Monero, RedLine has already run in the background stealing your passwords, cookies, browser information, and, potentially, any cryptocurrency wallets.
Unfortunately, almost all of this fake MSI Afterburner campaign's components have poor antivirus software detection.
VirusTotal reports that the malicious 'MSIAfterburnerSetup.msi' setup file is only detected by three security products out of 56, while the 'browser_assistant.exe' is only detected by 2 out of 67 products.
To stay safe from miners and malware, download tools directly from official sites rather than sites shared in forums, social media, or direct messages.
In this case, the legitimate MSI Afterburner can be downloaded directly from MSI at www.msi.com/Landing/afterburner/graphics-cards.
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.