Fake Bitwarden password manager advertisements on Facebook are pushing a malicious Google Chrome extension that collects and steals sensitive user data from the browser.
Bitwarden is a popular password manager app with a "free" tier featuring end-to-end encryption, cross-platform support, MFA integration, and a user-friendly interface.
Its user base has been growing steadily in the past couple of years, especially following security breaches of competitors that led many to look for alternatives.
A new malvertising campaign impersonating Bitwarden was spotted by Bitdefender Labs, whose researchers report that the operation launched on November 3, 2024.
Source: Bitdefender
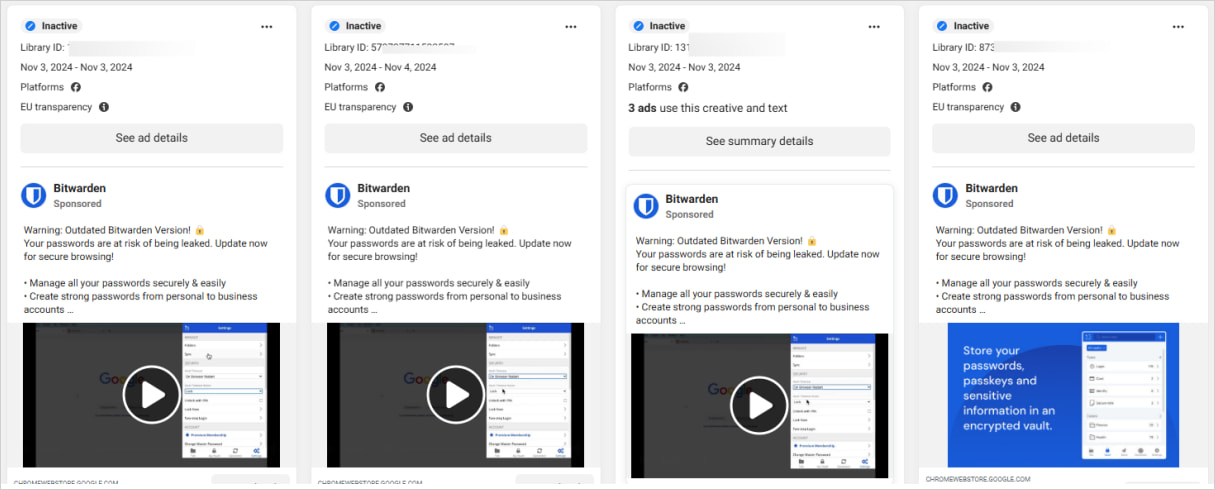
Malicious Facebook advertisements
The Facebook advertising campaign warns users that they're "using an outdated version of Bitwarden," and need to update the program immediately to secure their passwords.
The link included in the ad is 'chromewebstoredownload[.]com,' which pretends to be Google's official Chrome Web Store at 'chromewebstore.google.com.'
The landing page also features a design closely resembling the Chrome Web Store, including an 'Add to Chrome' button.
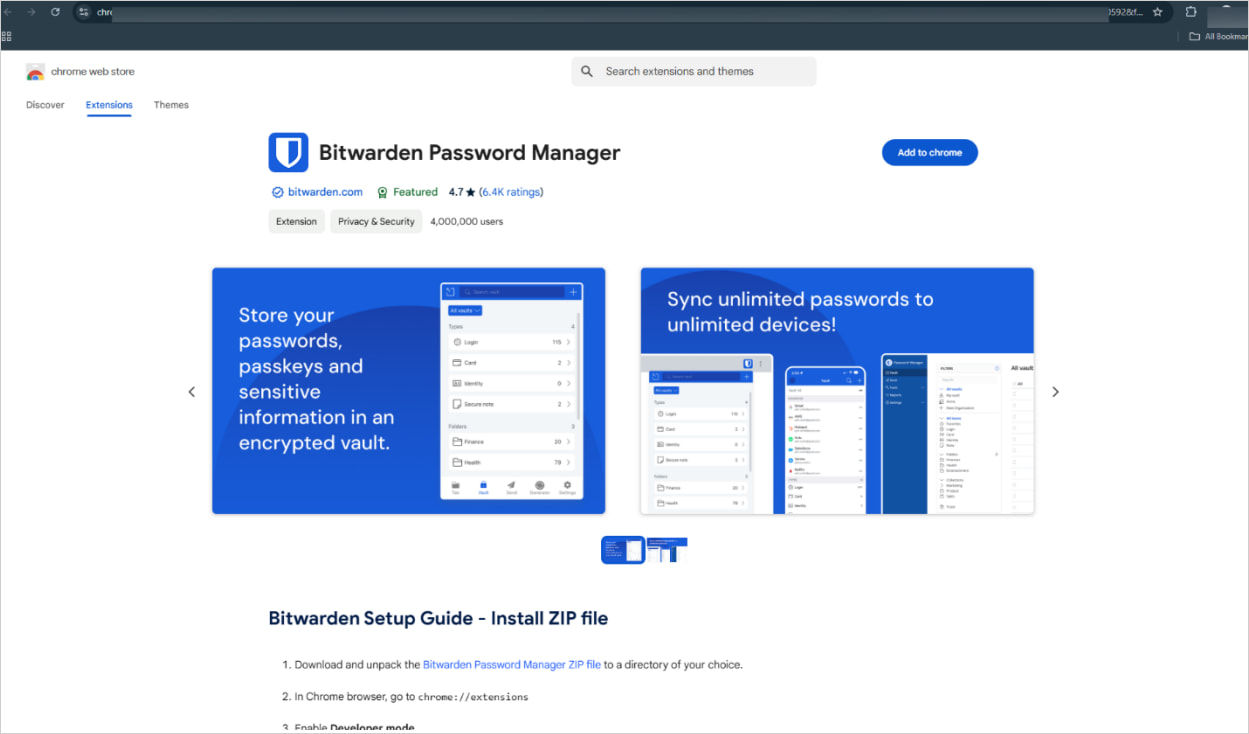
Source: Bitdefender
However, instead of the extension automatically installing when you click the link, visitors are prompted to download a ZIP file from a Google Drive folder.
Though this should be a clear sign of danger, users unfamiliar with the Chrome Web Store may proceed with the manual installation, following the instructions on the webpage.
The installation requires enabling 'Developer Mode' on Chrome and manually sideloading the extension on the program, so essentially, security checks are bypassed.
Once installed, the extension registers as 'Bitwarden Password Manager' version 0.0.1 and secures permissions that enable it to intercept and manipulate user activities.
Its main functions are the following:
- Collect Facebook cookies, particularly the 'c_user' cookie containing the user ID.
- Gather IP and geolocation data using public APIs
- Collect Facebook user details, account information, and billing data through Facebook's Graph API
- Manipulates browser DOM to display fake loading messages for legitimacy or deception.
- Encodes sensitive data and transmits it to a Google Script URL under the attackers' control.
To mitigate this risk, Bitwarden users are advised to ignore ads prompting extension updates, as Chrome extensions are automatically updated when the vendor releases a new version.
Extensions should only be installed via Google's official web store or by following links from the project's official website, in this case, bitwarden.com.
When installing a new extension, always check the requested permissions and treat overly aggressive requests involving access to cookies, network requests, and website data with high suspicion.
Hope you enjoyed this news post.
Thank you for appreciating my time and effort posting news every day for many years.
2023: Over 5,800 news posts | 2024 (till end of October): 4,832 news posts
RIP Matrix | Farewell my friend ![]()



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.