Proof-of-concept exploit code is now available online for a critical authentication bypass vulnerability in multiple VMware products that allows attackers to gain admin privileges.
VMware released security updates to address the CVE-2022-22972 flaw affecting Workspace ONE Access, VMware Identity Manager (vIDM), or vRealize Automation.
The company also shared temporary workarounds for admins who cannot patch vulnerable appliances immediately, requiring them to disable all users except one provisioned administrator.
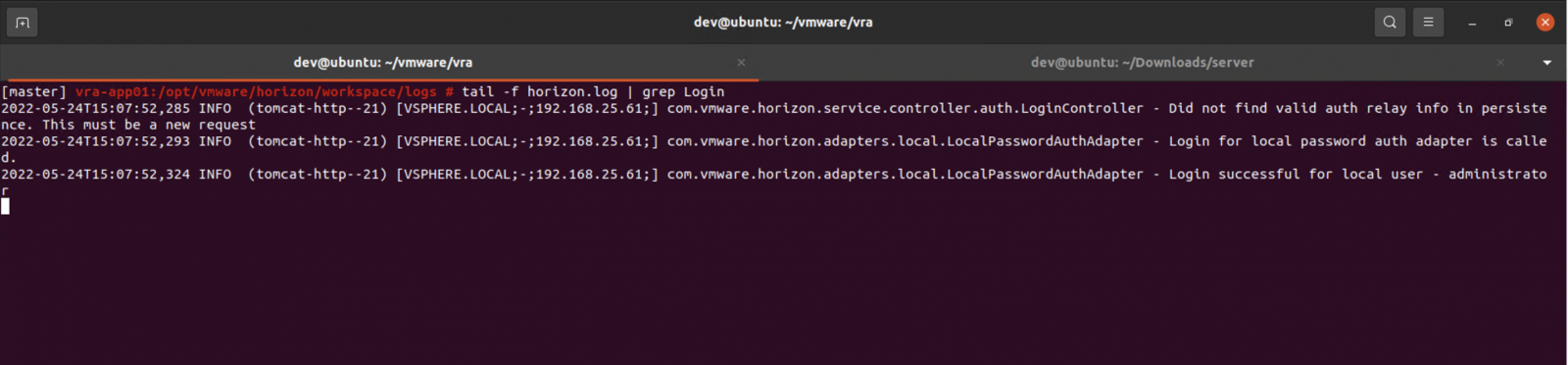
Horizon3 security researchers released a proof-of-concept (PoC) exploit and technical analysis for this vulnerability today, following an announcement made on Tuesday that a CVE-2022-22972 PoC will be made available later this week.
"This script can be used by bypass authentication on vRealize Automation 7.6 using CVE-2022-22972," the researchers said.
"Workspace ONE and vIDM have different authentication endpoints, but the crux of the vulnerability remains the same.
While Shodan only shows a limited number of VMware appliances exposed to attacks that would target this bug, there are several healthcare, education industry, and state government organizations with an increased risk of being targeted.
CVE-2022-22972 is a relatively simple 'Host' header manipulation vulnerability. Motivated attackers would not have a hard time developing an exploit for this vulnerability," Horizon3 added.
Critical security flaw with "serious" ramifications
"This critical vulnerability should be patched or mitigated immediately per the instructions in VMSA-2021-0014," VMware warned last week.
"The ramifications of this vulnerability are serious. Given the severity of the vulnerability, we strongly recommend immediate action."
The Cybersecurity and Infrastructure Security Agency (CISA) further highlighted this security flaw's severity level by issuing a new Emergency Directive that ordered Federal Civilian Executive Branch (FCEB) agencies to urgently update or remove VMware products from their networks.
In April, VMware has patched two more critical vulnerabilities, a remote code execution bug (CVE-2022-22954) and a 'root' privilege escalation (CVE-2022-229600) in VMware Workspace ONE Access and VMware Identity Manager.
Although the CVE-2022-22972 VMware auth bypass is not yet exploited in the wild, attackers have started abusing the ones addressed in April within 48 hours to backdoor vulnerable systems and deploy coin miners.
"CISA expects threat actors to quickly develop a capability to exploit these newly released vulnerabilities in the same impacted VMware products," the cybersecurity agency said.
Exploit released for critical VMware auth bypass bug, patch now
- aum
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.