Proof-of-concept exploit code has been released online for two actively exploited and high-severity vulnerabilities in Microsoft Exchange, collectively known as ProxyNotShell.
Tracked as CVE-2022-41082 and CVE-2022-41040, the two bugs affect Microsoft Exchange Server 2013, 2016, and 2019 and allow attackers to escalate privileges to run PowerShell in the context of the system and gain arbitrary or remote code execution on compromised servers.
Microsoft released security updates to address the two security flaws as part of the November 2022 Patch Tuesday, even though ProxyNotShell attacks have been detected since at least September 2022.
One week after Microsoft released ProxyNotShell security updates, security researcher Janggggg released the proof-of-concept (PoC) exploit attackers have used in the wild to backdoor Exchange servers.
Will Dormann, a senior vulnerability analyst at ANALYGENCE, tested the exploit and confirmed that it's working against systems running Exchange Server 2016 and 2019, and added that the code needs some tweaking to get it to work when targeting Exchange Server 2013).
Threat intelligence company GreyNoise has been tracking ProxyNotShell exploitation since late September and provides info on ProxyNotShell scanning activity and a list of IP addresses linked to these attacks.
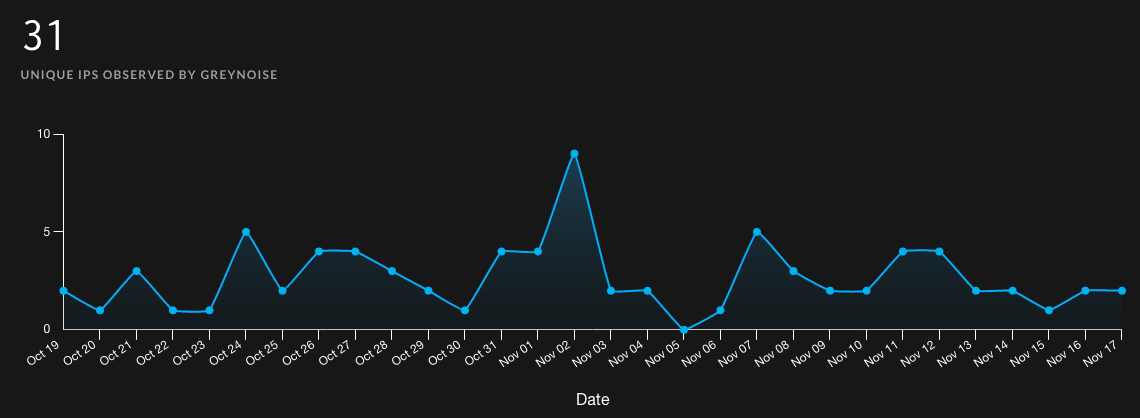
ProxyNotShell vulnerability scans (GreyNoise)
Attackers have been chaining the two security flaws to deploy Chinese Chopper web shells on compromised servers for persistence and data theft, as well as for lateral movement in their victims' networks since at least September 2022.
Redmond also confirmed they were actively abused in the wild on September 30, saying it was "aware of limited targeted attacks using the two vulnerabilities to get into users' systems."
"Because we are aware of active exploits of related vulnerabilities (limited targeted attacks), our recommendation is to install these updates immediately to be protected against these attacks," the Exchange Team warned after patches were released. [emphasis ours]
"These vulnerabilities affect Exchange Server. Exchange Online customers are already protected from the vulnerabilities addressed in these SUs and do not need to take any action other than updating any Exchange servers in their environment."
Security researchers at Vietnamese cybersecurity outfit GTSC, who first spotted and reported the attacks, said attackers have been chaining the two security flaws to deploy Chinese Chopper web shells on compromised servers.




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.