Israeli researcher Mordechai Guri has discovered a new method to exfiltrate data from air-gapped systems using the LED indicators on network cards. Dubbed 'ETHERLED', the method turns the blinking lights into Morse code signals that can be decoded by an attacker.
Capturing the signals requires a camera with a direct line of sight to LED lights on the air-gapped computer's card. These can be translated into binary data to steal information.
.png)
Air-gapped systems are computers typically found in highly-sensitive environments (e.g. critical infrastructure, weapon control units) that are isolated from the public internet for security reasons.
However, these systems work in air-gapped networks and still use a network card. If an intruder infects them with specially crafted malware, they could replace the card driver with a version that modifies the LED color and blinking frequency to send waves of encoded data, Mordechai Guri has found.
The ETHERLED method can work with other peripherals or hardware that use LEDs as status or operational indicators like routers, network-attached storage (NAS) devices, printers, scanners, and various other connected devices.
Compared to previously disclosed data exfiltration methods based on optical emanation that take control of LEDs in keyboards and modems, ETHERLED is a more covert approach and less likely to raise suspicion.
ETHERLED details
The attack begins with planting on the target computer malware that contains a modified version of the firmware for the network card. This allows taking control of the LED blinking frequency, duration, and color.
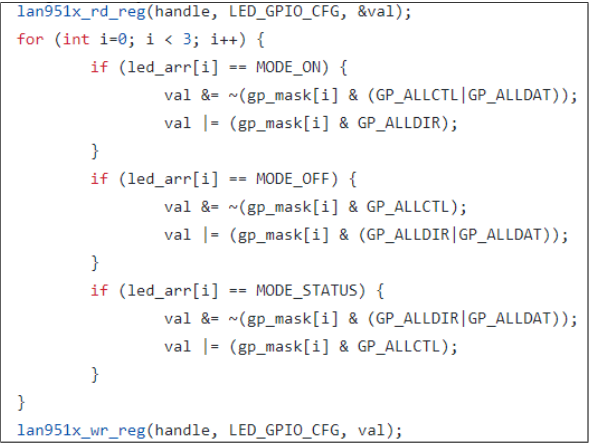
Alternatively, the malware can directly attack the drive for the network interface controller (NIC) to change connectivity status or to modulate the LEDs required for generating the signals.
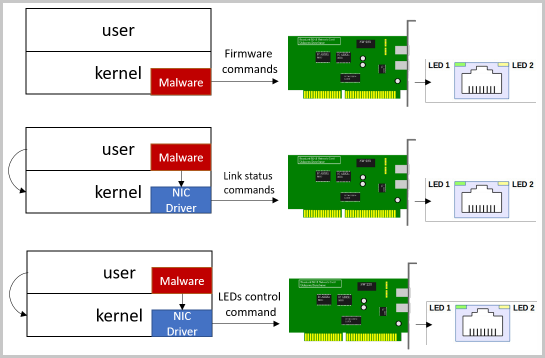
The researcher found that the malicious driver can exploit documented or undocumented hardware functionality to fiddle with network connection speeds and to enable or disable the Ethernet interface, resulting in light blinks and color changes.

Guri's tests show that each data frame begins with a sequence of '1010', to mark the start of the package, followed by a payload of 64 bits.
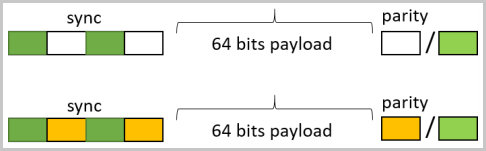
For data exfiltration through single status LEDs, Morse code dots and dashes lasting between 100 ms and 300 ms were generated, separated by indicator deactivation spaces between 100 ms and 700 ms.
The bitrate of the Morse code can be increased by up to ten times (10m dots, 30m dashes, and 10-70ms spaces) when using the driver/firmware attack method.
To capture the signals remotely, threat actors can use anything from smartphone cameras (up to 30 meters), drones (up to 50m), hacked webcams (10m), hacked surveillance cameras (30m), and telescopes or cameras with telephoto or superzoom lenses (over 100 meters).
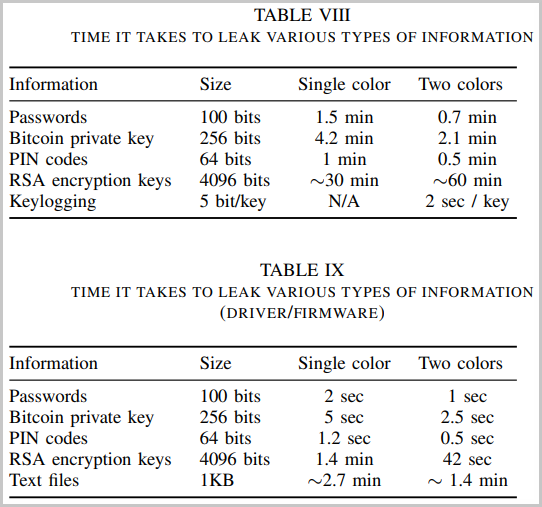
The time needed to leak secrets such as passwords through ETHERLED ranges between 1 second and 1.5 minutes, depending on the attack method used, 2.5 sec to 4.2 minutes for private Bitcoin keys, and 42 seconds to an hour for 4096-bit RSA keys.
Other exfiltration channels
Mordechai also published a paper on 'GAIROSCOPE', an attack on air-gapped systems relying on the generation of resonance frequencies on the target system, captured by a nearby (up to 6 meters) smartphone's gyroscope sensor.
In July, the same researcher presented the 'SATAn' attack, which uses SATA cables inside computers as antennas, generating data-carrying electromagnetic waves that can be captured by nearby (up to 1.2 meters) laptops.
The complete collection of Dr. Mordechai Guri's air-gap covert channel methods can be found in a dedicated section on the Ben-Gurion University of the Negev website.
ETHERLED: Air-gapped systems leak data via network card LEDs
- aum
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.