Hackers breached ESET's exclusive partner in Israel to send phishing emails to Israeli businesses that pushed data wipers disguised as antivirus software for destructive attacks.
A data wiper is malware that intentionally deletes all of the files on a computer and commonly removes or corrupts the partition table to make it harder to recover the data.
In a phishing campaign that started on October 8th, emails branded with ESET's logo were sent from the legitimate eset.co.il domain, indicating that the Israel division's email server was breached as part of the attack.
While the eset.co.il domain is branded with ESET's content and logos, ESET told BleepingComputer it is operated by Comsecure, their Israel distributor.
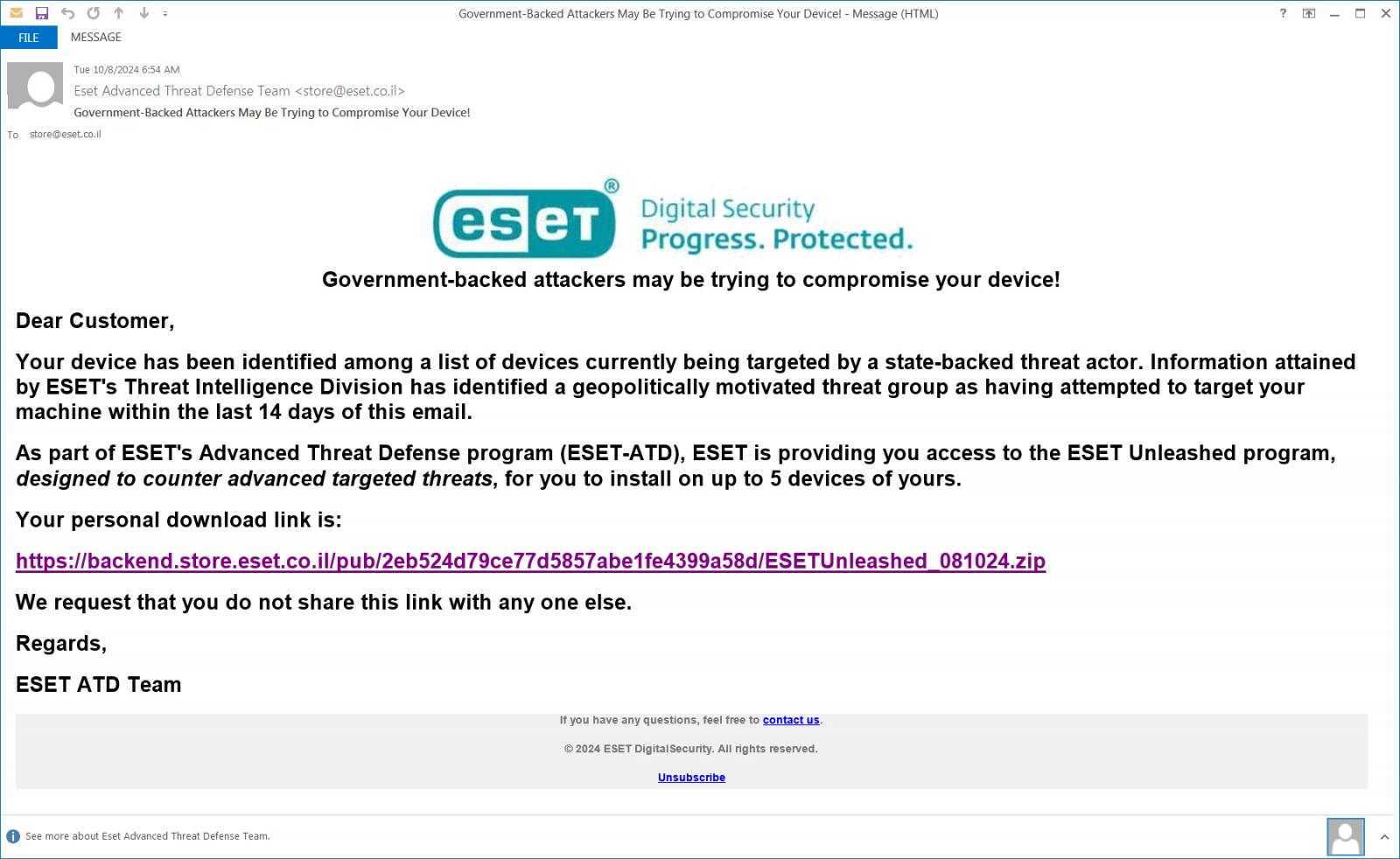
The emails pretend to be from "ESET's Advanded Threat Defense Team," warning customers that government-backed attackers are trying to target the recipient's device. To help protect the device, ESET offers a more advanced antivirus tool called "ESET Unleashed" to protect against the threat.
"Your device has been identified among a list of devices currently being targeted by a state-backed threat actor. Information attained by ESET's Threat Intelligence Division has identified a geopolitically motivated threat group as having attempted to target your machine within the last 14 days of this email," reads the phishing email obtained by BleepingComputer.
"As part of ESET's Advanced Threat Defense program (ESET-ATD), ESET is providing you access to the ESET Unleashed program, designed to counter advanced targeted threats, for you to install on up to 5 devices of yours."
Source: BleepingComputer
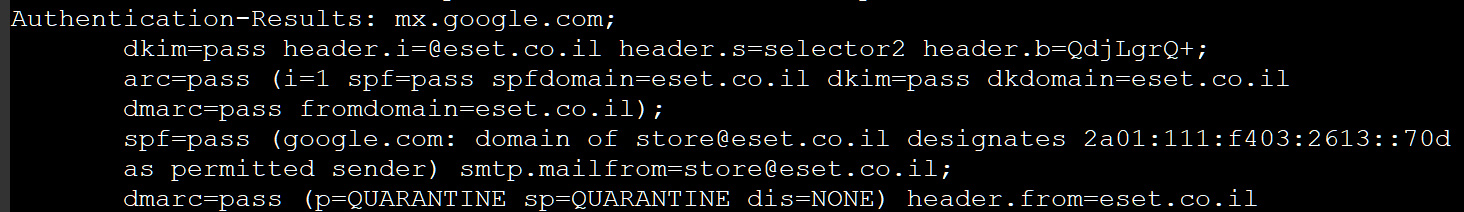
From the phishing email headers, BleepingComputer has confirmed that the email originated from legitimate mail servers for eset.co.il, passing SPF, DKIM, and DMARC authentication tests.
Source: BleepingComputer
To further add legitimacy to the attack, the link to the download was hosted on eset.co.il domain at URLs like, https://backend.store.eset.co[.]il/pub/2eb524d79ce77d5857abe1fe4399a58d/ESETUnleashed_081024.zip, which are now disabled.
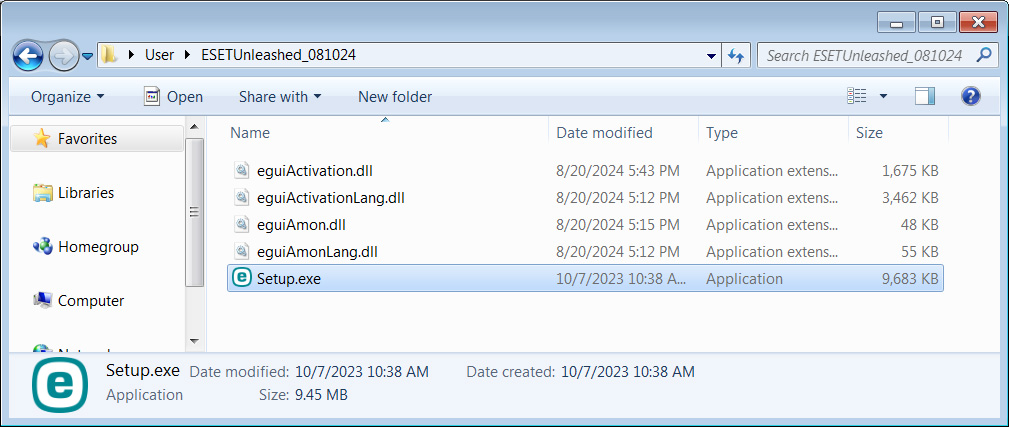
This ZIP archive [VirusTotal] contains four DLL files digitally signed by ESET's legitimate code signing certificate and a Setup.exe that is not signed.
The four DLLs are legitimate files distributed as part of ESET's antivirus software. However, the Setup.exe [VirusTotal] is the malicious data wiper.
Source: BleepingComputer
BleepingComputer attempted to test the wiper on a virtual machine, but the executable automatically crashed.
Cybersecurity expert Kevin Beaumont had better success when run on a physical PC, stating that it would reach out to a legitimate Israeli news site at www.oref.org.il.
"etup.exe is malicious. It uses a host of obvious techniques to try to evade detection," explains Beaumont.
"I could only get it to detonate properly on a physical PC. It calls variously obviously malicious things, e.g. it uses a Mutex from the Yanluowang extortion/ransomware group."
At this time, it is unknown how many companies were targeted in this phishing campaign or how Comsecure, ESET's Israeli distributor, was breached.
BleepingComputer emailed various people at Comsecure, including its CEO, but has not received a reply yet.
While the attack has not been attributed to any particular threat actor or hacktivism, data wipers have long been a popular tool in attacks against Israel.
In 2017, an anti-Israel & pro-Palestinian data wiper called IsraBye was discovered in attacks on Israeli organizations.
In 2023, Israel suffered a wave of BiBi wiper attacks targeting organizations, including in the education and technology sectors.
Many of these attacks were linked to Iranian threat actors, whose goal was not to generate revenue, but rather to sow chaos and disrupt Israel's economy.
RIP Matrix | Farewell my friend ![]()
Hope you enjoyed this news post.
Thank you for appreciating my time and effort posting news every day for many years.
2023: Over 5,800 news posts | 2024 (till end of September): 4,292 news posts
- coopers
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.