The Japan CERT has released a new version of their EmoCheck utility to detect new 64-bit versions of the Emotet malware that began infecting users this month.
Emotet is one of the most actively distributed malware spread through emails using phishing emails with malicious attachments, including Word/Excel documents, Windows shortcuts, ISO files, and password-protected zip files.
The phishing emails use creative lures to trick users into opening the attachments, including reply-chain emails, shipping notices, tax documents, accounting reports, or even holiday party invites.
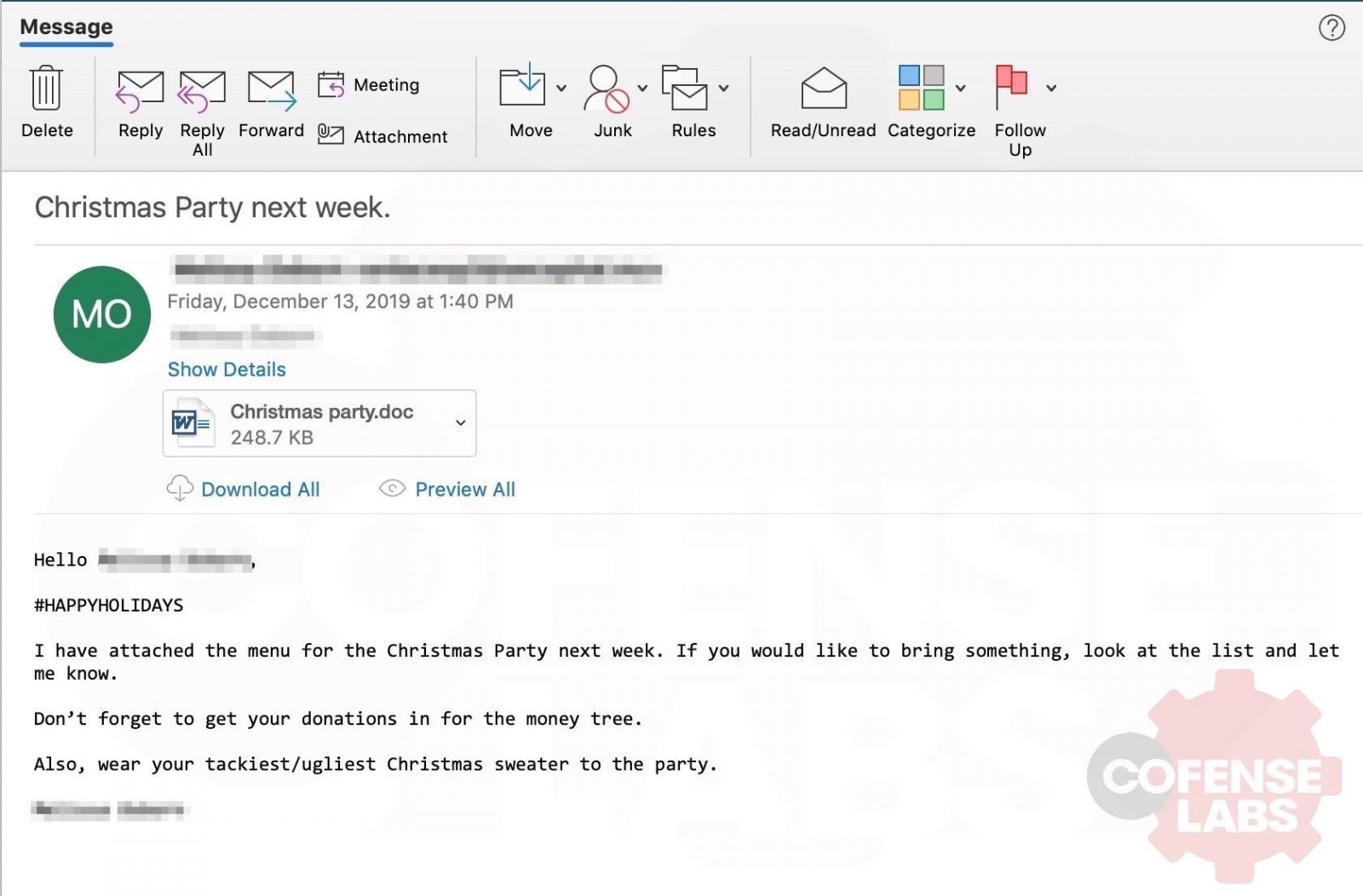
Once a device is infected, Emotet will steal users' emails to be used in future reply-chain phishing attacks and download further malware payloads on the computer.
As further malware commonly leads to data theft and ransomware attacks, it is crucial to detect Emotet malware infections quickly before further damage is done.
EmoCheck udpated for 64-bit versions
In 2020, the Japan CERT (computer emergency response team) released a free tool called EmoCheck to scan a computer for Emotet infections.
If one is detected, it will display the full path to the malware infection so that it can be deleted.
However, earlier this month, the Emotet gang switched to 64-bit versions of their loader and stealers, making existing detections less useful. Furthermore, with this switch, the EmoCheck tool could no longer detect the new 64-bit Emotet versions.
This week, JPCERT released EmoCheck 2.2 to support the new 64-bit versions and can now detect them, as shown below.
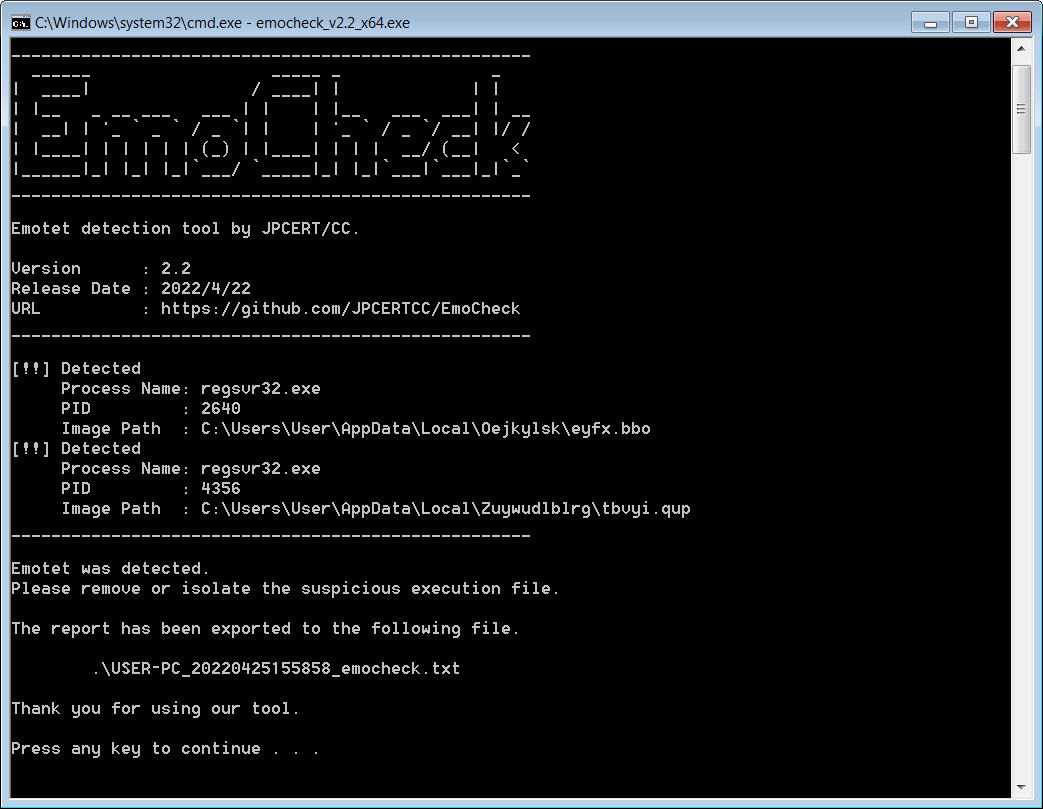
To check if you are infected with Emotet, you can download the EmoCheck utility from Japan CERT's GitHub repository.
Once downloaded, double-click on the emocheck_x64.exe (64-bit version) or emocheck_x86.exe (32-bit version), depending on what you downloaded.
EmoCheck will scan for the Emotet Trojan, and if the malware is detected, display the process ID it is running under and the location of the malware DLL.
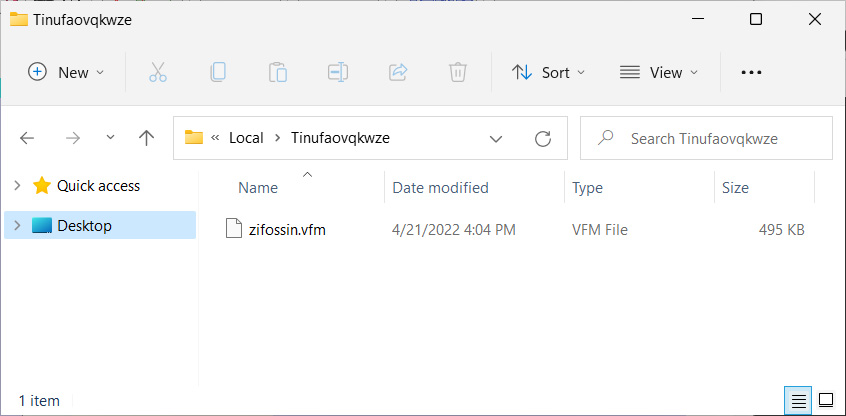
Emotet is currently being installed in a random folder under C:\Users\[username]\AppData\Local. While the Emotet malware is a DLL, it will not have the DLL extension but rather a random three-letter extension, like .bbo or .qvp.
An example of an installed Emotet malware infection can be seen below.
EmoCheck will also create a log in the same folder as the program that contains the detected information, allowing you to reference it as needed.
If you run EmoCheck and discover that you are infected, you should immediately open Task Manager and terminate the listed process, usually regsvr32.exe.
You should then scan your computer with trusted antivirus software to ensure other malware has not already been installed on your device.
This tool can be handy for Windows admins, who can execute it on login to detect Emotet infections on their network.


3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)


Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.