Sports betting company DraftKings revealed last week that more than 67,000 customers had their personal information exposed following a credential attack in November.
In credential stuffing attacks, automated tools are used to make a massive number of attempts (up to millions at a time) to sign into accounts using credentials (user/password pairs) stolen from other online services.
This tactic works exceptionally well against user accounts whose owners have reused the same login information across multiple platforms.
The attackers aim to take over as many accounts as possible to steal personal and financial info, which gets sold on hacking forums or the dark web. However, the stolen information may also be used in identity theft scams to make unauthorized purchases or empty banking accounts linked to compromised accounts.
Almost 68,000 DraftKings customers affected
In a data breach notification filed with the Main Attorney General's office, DraftKings disclosed that the data of 67,995 people was exposed in last month's incident.
The company said the attackers obtained the credentials needed to log into the customers' accounts from a non-DraftKings source.
"In the event an account was accessed, among other things, the attacker could have viewed the account holder's name, address, phone number, email address, last four digits of payment card, profile photo, information about prior transactions,
account balance, and last date of password change," the breach notification reads.
"At this time, there is currently no evidence that the attackers accessed your Social Security number, driver's license number or financial account number.
"While bad actors may have viewed the last four digits of your payment card, your full payment card number, expiration date, and your CVV are not stored in your account."
After detecting the attack, DraftKings reset the affected accounts' passwords and said it implemented additional fraud alerts.
It also restored the funds withdrawn as a result of the credential attack, refunding up to $300,000 identified as stolen during the incident, as DraftKings President and Cofounder Paul Liberman said in November.
Bank accounts of breached DraftKings users targeted in attack
The common denominator for user accounts that got hijacked seems to be an initial $5 deposit followed by a password change, enabling two-factor authentication (2FA) on a different phone number and then withdrawing as much as possible from the victims' linked bank accounts.
While DraftKings has not shared additional info on how the attackers stole funds, BleepingComputer has since learned that the attack was conducted by a threat actor selling stolen accounts with deposit balances on an online marketplace for $10 to $35.
The sales included instructions on how the buyers could make $5 deposits and withdraw all of the money from hijacked DraftKings user accounts.
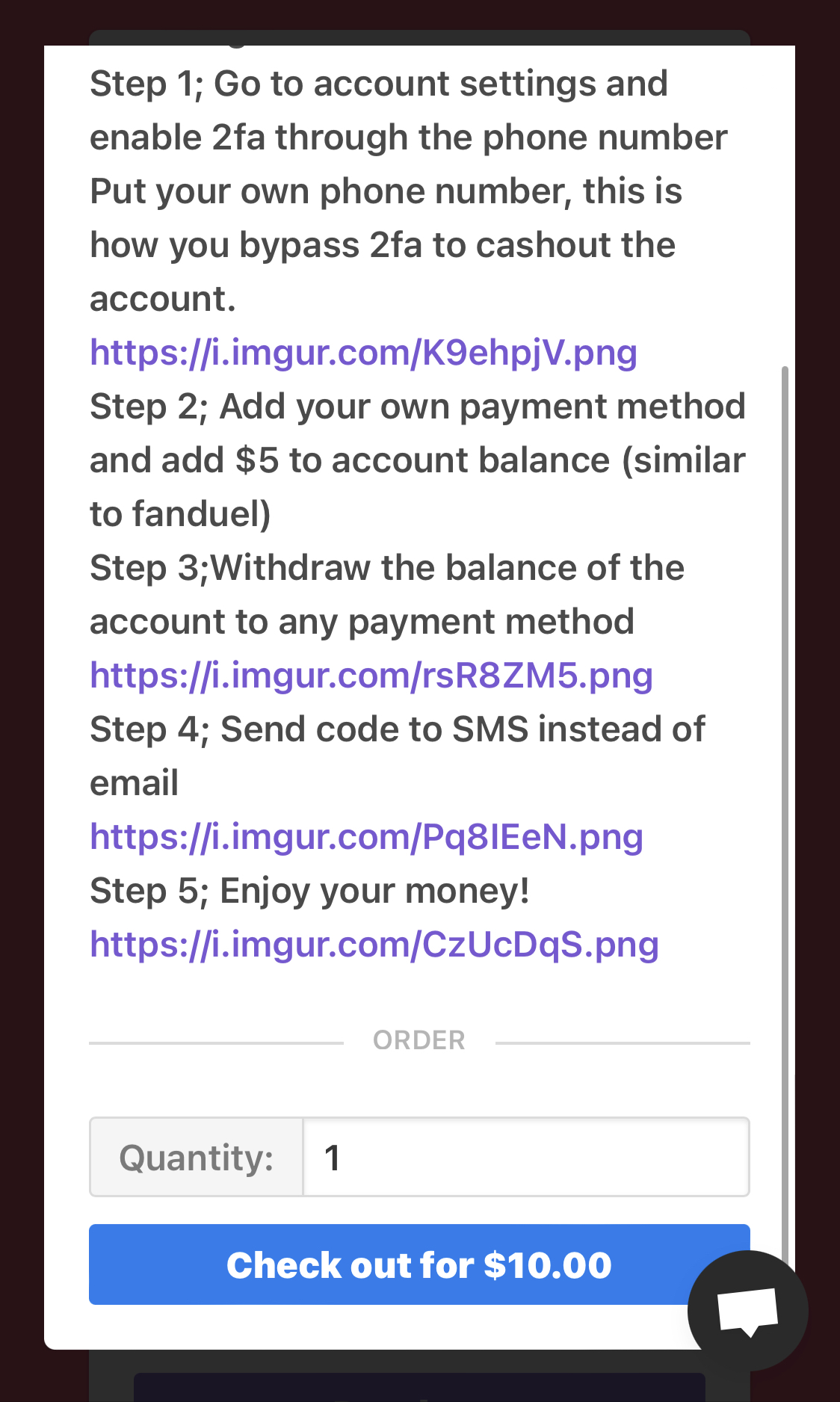
Instructions on how to empty breached DraftKings accounts (BleepingComputer)
After DraftKings announced the credential stuffing attack, they locked down the breached accounts, with the threat actors warning that their campaign was no longer working.
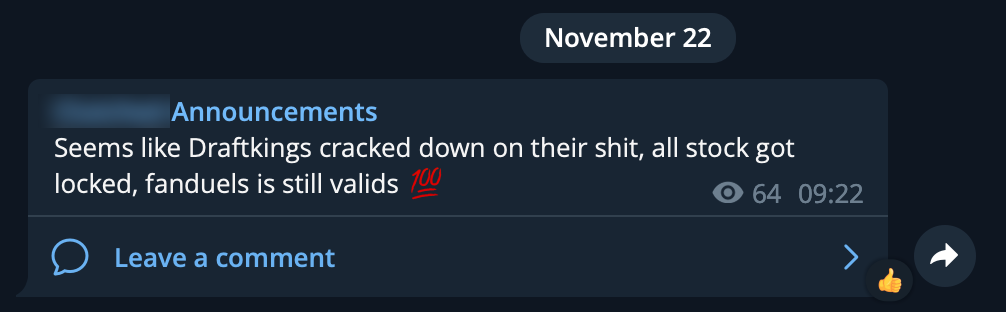
Warning that DraftKings locked the breached accounts (BleepingComputer)
The company is now advising customers never to use the same password for multiple online services, never share their credentials with third-party platforms, turn
on 2FA on their accounts immediately, and remove banking details or unlink their bank accounts to block future fraudulent withdrawal requests.
As the FBI warned recently, credential stuffing attacks are quickly growing in volume due to readily available automated tools and aggregated lists of leaked credentials.
In September, identity and access management company Okta also reported that the situation has drastically worsened this year since it recorded over 10 billion credential-stuffing events during the first three months of 2022.
This amounts to roughly 34% of the overall authentication traffic tracked by Okta, which means that one in three sign-in attempts are malicious and fraudulent.
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.