Dozens of Vulnerable NuGet Packages Allow Attackers to Target .NET Platform
An analysis of off-the-shelf packages hosted on the NuGet repository has revealed 51 unique software components to be vulnerable to actively exploited, high-severity vulnerabilities, once again underscoring the threat posed by third-party dependencies to the software development process.
In light of the growing number of cyber incidents that target the software supply chain, there is an urgent need to assess such third-party modules for any security risks and minimize the attack surface, ReversingLabs researcher Karlo Zanki said in a report shared with The Hacker News.
NuGet is a Microsoft-supported mechanism for the .NET platform and functions as a package manager designed to enable developers to share reusable code. The framework maintains a central repository of over 264,000 unique packages that have collectively produced more than 109 billion package downloads.
"All identified precompiled software components in our research were different versions of 7Zip, WinSCP and PuTTYgen, programs that provide complex compression and network functionality," Zanki explained. "They are continuously updated to improve their functionality and to address known security vulnerabilities. However, sometimes it happens that other software packages get updated but still keep using several years old dependencies containing known vulnerabilities."
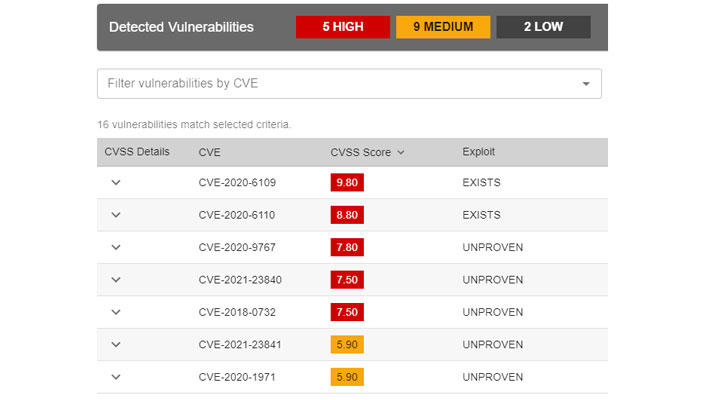
In one instance, it was found that "WinSCPHelper" — a remote server file management library and which has been downloaded more than 35,000 times — use an old and vulnerable WinSCP version 5.11.2, whereas WinSCP version 5.17.10 released earlier this January addresses a critical arbitrary execution flaw (CVE-2021-3331), thus exposing users of the package to the vulnerability.
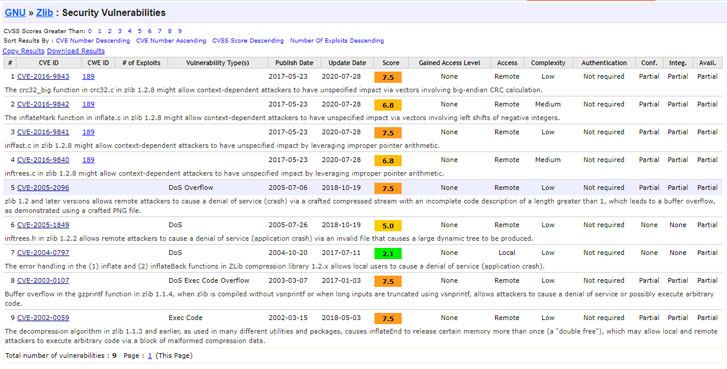
Furthermore, the researchers established that more than 50,000 software components extracted from NuGet packages were statically linked to a vulnerable version of "zlib" data compression library, rendering them vulnerable to a number of known security issues such as CVE-2016-9840, CVE-2016-9841, CVE-2016-9842, and CVE-2016-9843.
Some of the packages that were observed to have a zlib vulnerability are "DicomObjects" and "librdkafka.redist", each of which have been downloaded no less than 50,000 and 18.2 million times. A matter of more concern is that "librdkafka.redist" is listed as a dependency for several other popular packages, counting Confluent's .NET Client for Apache Kafka (Confluent.Kafka), which, in turn, has been downloaded more than 17.6 million times to date.
"Companies developing software solutions need to become more aware of such risks, and need to become more involved in their handling," Zanki said. "Both the inputs and final outputs of the software development process need to be checked for tampering and code quality issues. "Transparent software development is one of the keystones needed to enable early detection and prevention of software supply-chain attacks."
- Karlston
-

 1
1



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.